- Saturday
- January 11th, 2025
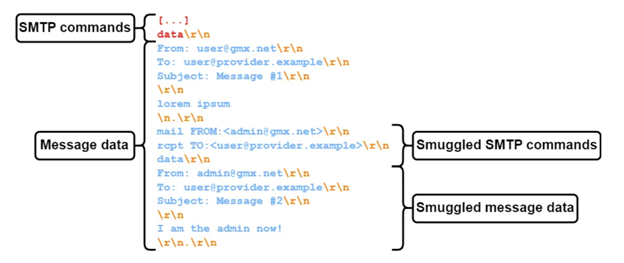
SEC Consult Longin identified two big email providers whose SMTP servers interpreted . as the end of data: Fastmail and Runbox. However, he also found that popular SMTP server software like Postfix and Sendmail were also accepting this end-of-data sequence...

Spammers, phishers and every kind of risk actors prefer to forge email to seduce customers into opening malicious email and letting the barbarians within the gates. Email authentication with the DomainKeys Identified Mail customary can cease -- or no less...

The world is so swamped by cybercrime that even massive eCommerce tycoons like Amazon battle to implement efficient e-mail spoofing safety. Lately, hackers are sending fake emails and textual content messages purporting to be from Amazon officers. They’re manipulating focused...

Organizations have a proper to be involved concerning the endless flood of undesirable email messages, nevertheless it wasn't till a few decade in the past that rising requirements for preventing spam, phishing and different malicious email got here on the...

What is the Sender Policy Framework (SPF)? Sender Policy Framework (SPF) is an e mail verification system. First launched via the Internet Engineering Task Force (IETF) in 2014, it helps decide whether or not a sender of a message has...

If you aren't utilizing international e mail safety requirements SPF, DKIM and DMARC, you have to be. They’ve been round for a few years and used and trusted by thousands and thousands of individuals. They can solely assist.Sender Policy Framework...

