If you aren’t utilizing international e mail safety requirements SPF, DKIM and DMARC, you have to be. They’ve been round for a few years and used and trusted by thousands and thousands of individuals. They can solely assist.
Sender Policy Framework (SPF), Domain Keys Identified Mail (DKIM) and Domain-Based Message Authentication, Reporting and Conformance (DMARC) mean you can stop malicious third events from spoofing your e mail area to others who use it. They don’t work completely, however when enabled will completely reduce down on some types of e mail maliciousness.
For these protocols to work, the sender’s e mail area administrator permits them in DNS utilizing TXT data. (TXT data are a specific kind of DNS file, like an A file is), or by enabling it of their e mail host supplier’s administrative console. When enabled, receivers (truly their e mail servers or shoppers on their behalf) of emails from activated domains can verify extra data to confirm whether or not a specific e mail got here from the e-mail area from which it claims to be despatched.
It’s just a little complicated. Sending domains allow the protocols in order that receivers can confirm that emails are actually from the sender’s area. Senders allow these protocols so different individuals can’t declare to be them. Receivers allow them to allow them to confirm whether or not a specific e mail is from the place it says it’s from. Both sides have to be enabled. Enabling them can’t damage something, except you determine to take the draconian step of rejecting all emails that fail any of the checks. Hint: This will trigger far too many false positives, so select to quarantine as an alternative.
SPF works by stopping spoofing of a legit e mail actual return address (i.e., the e-mail address that you’d be sending a reply to) area. This e mail address is called the 5321 address, as a result of it’s outlined in RFC 5321, which defines Simple Mail Transfer Protocol (SMTP). Depending on the e-mail shopper, the 5321 address might not all the time be displayed. This is very true of small form-factor e mail shoppers akin to those you see on smartphones.
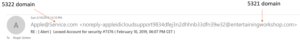
DKIM works by stopping the spoofing of the “Display From” e mail address (from RFC 5322, Internet Message Form e mail customary) area. The Display From address is sort of all the time proven to an end-user once they preview or open an e mail, therefore its identify. The determine under reveals the distinction between the 5321 and 5322 e mail addresses.
 Roger Grimes
Roger GrimesThe distinction between the 5321 and 5322 e mail addresses
Although these addresses can differ in legit e mail, they’re extra prone to differ in malicious emails. I’ve all the time thought-about it to be very like the distinction between what a URL hyperlink seems like in an e mail and what it truly is when hovering a mouse cursor above it. Whenever I see two various things, I get just a little cautious. In most emails, the 2 URL variations ought to agree, and hovering over one ought to simply confirm that it matches the extra apparent show identify (which might be spoofed).
SPF and DKIM enable receivers of emails to make sure that the domains (and domains solely) of a acquired e mail are actually from the e-mail servers of these claimed domains. However, they do it fairly in a different way. DMARC is a further customary that basically tells others relying in your SPF and DKIM data how they need to deal with failing or spoofed emails.
Note: SPF and DKIM solely confirm the legitimacy of the sending and claimed domains (e.g., @instance.com). The e mail address identify portion earlier than the e-mail area (e.g., roger@ or rogerg@) might nonetheless be spoofed by a malicious sender.
How to make use of SPF
Senders allow SPF for his or her area by creating at the very least one DNS TXT file. When creating the SPF DNS TXT file, you want to have a number of items of data helpful, together with which e mail server(s) would you like dealing with every outlined area and their public IP addresses.
Useful SPF configuration hyperlinks embody Rackspace’s instructions on creating an SPF TXT record; Proofpoint’s SPF Check, which helps you to discover out which servers are licensed to ship e mail on behalf of a site; and SPF Wizard, which helps you craft the required DNS file based mostly in your question solutions.
If nonetheless doubtful, contact your ISP or e mail area supplier. They ought to have the ability to let you know what you want to embody within the DNS TXT file. Here’s some easy SPF instance TXT data:
com. IN TXT "v=spf1 -all"
com. IN TXT “v=spf1 a ip4:192.168.1.1 ~all”
Microsoft Office 365 customers ought to confer with the Microsoft knowledgebase to allow SPF for his or her area.
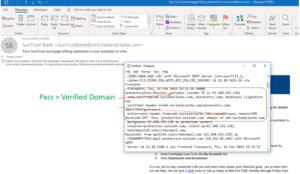
Here’s what a verified SPF e mail header seems like as soon as it will get to an e mail shopper:
 Roger Grimes
Roger GrimesVerified SPF e mail header
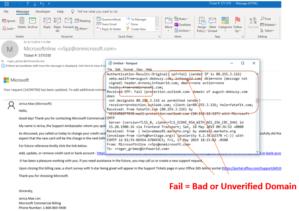
Here’s what a verified failed SPF header seems like as soon as it will get to an e mail shopper:
 Roger Grimes
Roger GrimesVerified failed SPF header
Remember, with all these applied sciences, the end-user isn’t normally inspecting headers or figuring out whether or not to take a look at a specific e mail. This is all carried out within the background by the receiving e mail server/service, though understanding what the headers seem like in cross and fail modes may help these of us who care sufficient to look at the headers once we see a suspicious e mail.
How to make use of DKIM
DKIM takes a bit more knowledge than SPF to set up. It requires a modification to that sender’s e mail server/servicei. The sender has to create/get a cryptographic public/non-public key pair, set up it on their e mail server/service, and then create a DNS TXT file that incorporates their public key. Each outgoing e mail is signed by the e-mail server’s non-public key and receivers can confirm the digitally signed e mail through the use of the sender’s public key.
Here’s an instance of a DKIM DNS TXT file (p is the general public key of e mail server in Base64 format):
selector._domainkey.instance.com IN TXT “v=DKIM1;p=RAG…123”
This is an instance DKIM e mail header:
 Roger Grimes
Roger GrimesDKIM e mail header
This is an instance of a DKIM e mail header efficiently verified:
 Roger Grimes
Roger GrimesVerified DKIM e mail header
How to make use of DMARC
DMARC is just an aggregator service to find out whether or not the sender makes use of SPF and DKIM, and how the sender recommends receivers ought to deal with failed/spoofed emails claiming to be from the sender’s area. Like SPF and DKIM, it’s set up in DNS as a TXT record by the sender.
A DMARC DNS TXT file may look just like this:
TXT IN "v=DMARC1;p=quarantine;pct=100;rua=mailto:[email protected];"
One of crucial fields is the p worth, which signifies how the sender desires receivers to deal with failed emails. P might be one in all three values:
- None – take no particular therapy for failed emails
- Quarantine – deal with as suspicious
- Reject – reject e mail at server earlier than it will get to shopper
Be conscious that legit emails fail a number of SPF, DKIM and DMARC checks routinely. This is actually because somebody configured one thing fallacious, the e-mail is incorrectly manipulated, or different causes. Anyone selecting the “reject” worth will most likely be killed by administration or their end-users as a result of they didn’t get legit emails. Be secure and go with “quarantine” as an alternative. Even then, many e mail companies will simply act as if “none” was specified.
Protocols are usually not good
SPF, DKIM DMARC are usually not good, for a lot of causes together with these:
- Hacker might be sending a malicious e mail from inside a compromised area setting
- Hacker might be utilizing a site that permits and makes use of SPF and DKIM
- Many business e mail hosts don’t respect your settings or all settings. Many instances, it’s because of the means massive e mail hosts work utilizing many servers over many altering IP addresses to ship e mail on behalf of your area
Even with the issues, enabling SPF, DKIM and DMARC can solely enable you. It will reduce down on some portion of your fraudulently acquired spoof emails, and that’s solely good.
Just be sure you by no means utterly reject any e mail that fails a number of verification checks. Legitimate emails fail these checks on a regular basis. You need to set SPF, DKIM and DMARC in order that they are going to let any failed e mail be inspected by a human defender (i.e., quarantined). If you discover that SPF, DKIM or DMARC causes too many issues, you may all the time select much less aggressive settings, or if an entire failure, disable them altogether (though I’ve not seen anybody who has had to do that but).
One extra be aware. Office 365 customers regularly complain that Microsoft doesn’t respect all their e mail protection settings. Many 0ffice 365 admins set up an Exchange rule to dam emails that spoof the receiver’s personal area.
Copyright © 2019 IDG Communications, Inc.