SEC Consult
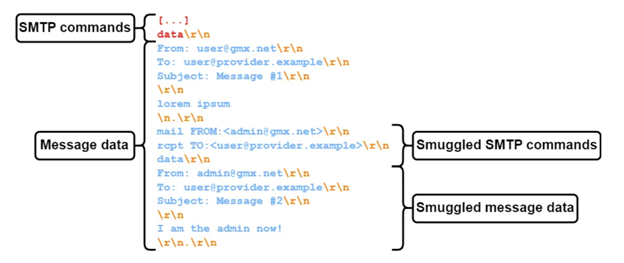
Longin identified two big email providers whose SMTP servers interpreted
The researcher now had the ability to spoof any GMX identities to users of any of these vulnerable SMTP servers in a way where the messages would pass SPF, DKIM and DMARC validation because they were delivered through the real GMX SMTP server without being blocked.
The issue was worse, because GMX also runs the web.de domain and is also a subsidiary of Ionos, a large web hosting company. It turns out Ionos’s SMTP servers ran the same custom software as GMX’s and were therefore also allowing outbound email messages with
Like GMX and Ionos, another SMTP provider that allowed outbound emails with
However, the impact was more limited because Outlook and Exchange Online use the BDAT (or chunking) command to send messages by default. This is an SMTP feature that specifies the exact message length in bytes instead of relying on end-of-data sequences and it makes SMTP smuggling impossible. However, there’s a fallback mechanism because not all receiving SMTP servers support BDAT. For those that don’t, the Exchange servers will fall back to using the regular DATA command to send messages.
To be vulnerable to spoofing via Exchange Online messages, an incoming SMTP server needs to meet two conditions instead of one: Not support BDAT and interpret
Cisco Secure Email settings could allow SMTP smuggling
While testing other exotic end-of-data sequences against inbound SMTP servers of the former Alexa top 1,000 domains, Longin found several high-profile domains that accepted
All those domains were using Cisco’s Secure Email service with on-premises deployments of Cisco Secure Email Gateway or the cloud-based Cisco Secure Email Cloud Gateway. The Cisco Secure Email Gateway can be thought of as a proxy server that checks emails for malicious content before passing them to the user’s real SMTP email server. The software has a configuration option for how to handle messages that contain bare carriage return (CR) or line feed (LF) characters with three settings: Clean, Reject, or Allow.
The behavior of the “clean” setting, which is the default one, consists of converting bare CR or LF characters into CRLF characters meaning that
SEC Consult advises Cisco Secure Email Gateway users to change this setting from “Clean” to “Allow” so that messages with
https://www.csoonline.com/article/1269779/smtp-smuggling-enables-email-spoofing-while-passing-security-checks.html






