- Monday
- May 6th, 2024

In today’s digital age, email has become an essential tool for communication in the enterprise world. As a result, email hosting has become a critical aspect of business operations, with security and scalability being two key considerations, providing secure and...

What is it about authorities officers and their shoddy email practices? Several members of the Trump Administration were discovered to have used private or unclassified email accounts for categorised emails. Using a non-public server as Secretary of State may need...

In at present’s linked world, an organization’s network is the spine of its enterprise. However, the rising variety of gadgets, endpoints, and applied sciences that enterprises use makes community administration more and more advanced. For instance, the fashionable community now...
There are many finest practices for SEO, together with these offered by Google. Here are 17 ideas that may assist one develop a greater search presence. What Do Best Practices For SEO Even Mean? Best practices for SEO are usually...

Storage directors will probably want to assist with the legal hold course of in some unspecified time in the future. Most organizations finally face some sort of litigation, which normally signifies that they have to place legal holds on their...

1. Introduction With information leaks, ransomware assaults and different cyber security incidents turning into more and more rampant and round 18% (eighteen per cent) of Indians being victims of such cyber security incidents[1], one would anticipate the Indian Computer Emergency...
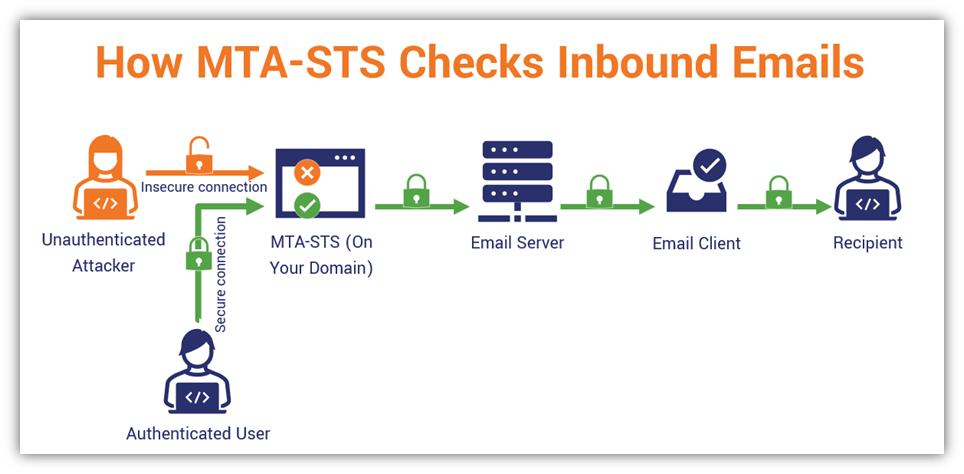
If you’re like most companies, it’s is your foremost communication channel with clients. Here are some e mail server safety greatest practices you need to use straight away to assist create a safe e mail server on your group Imagine...

MultiVersus is lastly right here, a minimum of in a closed alpha take a look at that has allowed more gamers to attempt the sport for themselves and see simply what the most recent platform fighter on the block is...

Aware that knowledge breaches are as a lot a governance problem as they are an IT problem, company authorized departments have change into accustomed to conserving a cautious watch over their group's digital defences lately. Presently, a current surge in...
 Loading posts...
Loading posts...  All posts loaded
All posts loaded
No more posts

