The IT infrastructure of bigger organizations may be very heterogeneous. They have endpoints, servers and cell units working numerous working techniques and accessing inside techniques. On these techniques, there’s a nice variety of disparate instruments – from open-source databases and internet servers to industrial instruments utilized by the group’s monetary division. Furthermore, these functions can now even be deployed on completely different clouds to attain additional resilience, including much more complexity to an already intricate infrastructure.
Managing IT infrastructure poses a tough downside, particularly in these pandemic occasions the place the workforce tends to work remotely. Building an extra layer of safety over this infrastructure is an advanced endeavor and the success of this mission will rely on the provision of safety personnel and of safety monitoring, detection and response instruments that may cut back their burden. Unfortunately, as a result of complexity of securing infrastructure and the large quantity of assault vectors, the maturity of organizations’ safety monitoring can fall behind.
One of the options to this downside is to make use of applied sciences that may present visibility within the group’s infrastructure, whereas concurrently gathering and detecting anomalous occasions in addition to responding to them.
A number of years in the past, safety professional Anton Chuvakin instructed the idea of EDR (endpoint detection and response) within the type of a light-weight endpoint agent that fills the hole between detection and response capabilities accessible at the moment.
EDR has progressed to the idea of XDR – prolonged detection and response – which represents a merger of protection and response capabilities between numerous infrastructure layers (community site visitors, electronic mail, endpoints, cloud cases, shared storage, and so on.).
To achieve success, XDR ought to examine completely different layers, file and retailer occasions, and – based mostly on its superior analytics options – correlate occasions over layers to detect those who must be inspected by higher-tier analysts. The aim is a quicker detection and response cycle to cut back the time attackers can lurk in your infrastructure, but in addition to cut back SOC analysts’ alert fatigue and stop burnout.
We have examined Group-IB’s Threat Hunting Framework (THF), which tells the total story of an incident and its mastermind and might correlate occasions and alerts between completely different infrastructure layers, earlier than escalating incidents that want further consideration from analysts. Its function is to do passive safety monitoring, but in addition to uncover assaults and cut back the time attackers spend in your techniques. It depends on international menace intelligence capabilities by Group-IB that may give analysts further context relating to safety alerts and incidents.
Methodology
For this evaluate, we used a cloud sensor and a Huntbox (administration system) occasion. We put in Huntpoint, a separate light-weight endpoint agent, on virtualized (KVM) endpoints. The endpoints’ working system was Windows 10 with the most recent patches, on which we manually put in Huntpoint. For some use instances we disabled Windows Defender (Microsoft’s antivirus answer) in order that we will take a look at Huntpoint detection and blocking capabilities within the wild.
On the endpoints, we carried out easy take a look at actions to see if these occasions are later accessible in THF. We:
- Accessed and downloaded malicious recordsdata
- Used Windows Script Host with a VBS script
- Used PowerShell to obfuscate command execution
- Made Wmic course of calls
- Dumped NTLM hashes with Mimikatz
- Opened a bind shell with Netcat
We additionally carried out a full an infection with the Ryuk ransomware and tried to isolate the host.
To take a look at electronic mail detection capabilities, we used numerous malicious paperwork (MS Word recordsdata, PDFs) and archives that have been moreover nested or have been password protected. We despatched these malicious paperwork as electronic mail attachments from a ProtonMail account, to keep away from emails getting blocked from being delivered to the monitored mailbox.
We examined THF Polygon, the malware detonation platform, with the identical set of recordsdata. We manually examined Ryuk and Sigma ransomware by importing them to Polygon. Other malicious recordsdata from the take a look at dataset have been despatched robotically from Huntpoint. The collected indicators have been used for testing Group-IB Threat Intelligence & Attribution system.
During the take a look at we stored an eye fixed on these success components that helped us type a last opinion of the product:
- Detection capabilities (endpoint occasions, recordsdata and electronic mail)
- Ease of use and integration capabilities
- Threat Intelligence knowledge high quality whereas offering context for present occasions
- Resource consumption (CPU/RAM for EDR, and so on.)
Threat Hunting Framework
Group-IB’s Threat Hunting Framework (THF) is an answer that helps organizations establish their safety blind spots and provides a holistic layer of safety to their most important companies each in IT and OT environments.
The framework’s goal is to uncover unknown threats and adversaries by detecting anomalous actions and occasions and correlating them with Group-IB’s Threat Intelligence & Attribution system, which is able to attributing cybersecurity incidents to particular adversaries. In different phrases, while you spot a suspicious area/IP type in your community site visitors, with just a few clicks you possibly can pivot and uncover what’s behind this infrastructure, view historic proof of earlier malicious actions and accessible attribution data that can assist you broaden or shortly shut your investigation. THF intently follows the incident response course of by having a devoted element for each step.
There are two flavors of THF: the enterprise model, which is tailor-made for many enterprise organizations that use a regular know-how stack (electronic mail server, Windows area, Windows/macOS endpoints, proxy server, and so on.), and the economic model, which is ready to analyze industrial-grade protocols and shield industrial management system (ICS) units and supervisory management and knowledge acquisition (SCADA) techniques.
Threat Hunting Framework is ready to:
- Analyze community site visitors and detect suspicious actions (covert channels, tunnels, distant management, C&C beaconing) by utilizing the Sensor module
- Terminate encrypted connections at Layer 2 and Layer 3
- Integrate with on-premises and cloud electronic mail techniques
- Provide visibility into endpoints and handle incidents on them utilizing the EDR element/system known as THF Huntpoint. THF Huntpoint can detect in style privilege escalation assaults and lateral motion methods (pass-the-hash/ticket, Mimikatz, NTLM bruteforce, use of living-of-the-land binaries and comparable instruments)
- Analyze recordsdata by utilizing the malware detonation platform THF Polygon
- Perform superior menace looking utilizing logs from THF Huntpoint, electronic mail channel, site visitors and habits markers of every analyzed file from any supply
- Detect anomalies and unknown threats by correlating all accessible knowledge between numerous THF modules
- Enriching occasions with knowledge/data from Group-IB’s Threat Intelligence & Attribution cloud database
All the information is enriched and accessible from a central dashboard and administration system known as THF Huntbox. THF Huntbox allows incident administration, correlation of occasions and collaboration between analysts throughout menace looking and IR actions. All community site visitors anomalies, electronic mail alerts, Huntpoint detections, and recordsdata detonated inside Polygon can be found and the person can correlate the occasion knowledge (IoCs) with the Threat Intelligence & Attribution database by utilizing graph evaluation and different methods.
THF will also be paired with CERT-GIB (Group-IB’s Computer Emergency Response Team) by sending telemetry knowledge or IoCs for additional investigation by consultants, which might deliver a better degree of experience to advanced incidents and enhance the maturity degree of your SOC.
Figure 1 – Threat Hunting Framework’s structure with all accessible parts
THF parts
THF Sensor and THF Decryptor
THF Sensor is a system used to investigate incoming and outgoing community site visitors in real-time, extract recordsdata from it, utilizing ML-based intelligence site visitors evaluation approaches (to detect lateral motion, DGA exercise and covert tunnels) and signatures, block suspicious recordsdata (with the proxy, ICAP integration). All recordsdata which can be collected from the community site visitors will be despatched to THF Polygon, a file detonation system that’s used for behavioral evaluation.
Sensor comes as a 1U bodily equipment or will be deployed as a Virtual Machine relying in your use case and necessities. For analyzing 250Mbps over a SPAN port, you’ll need at minimal 32Gb RAM and 12 vCPUs. Sensor can analyze mirrored site visitors from the SPAN/RSPAN port, TAP units or site visitors from RSPAN despatched over GRE tunnels, that means that, when deployed, it has no impact on the enterprise community throughput. Sensor helps a variety of bandwidth configurations, the usual variations help 250, 1000 and 5000 Mbps, however Sensor can help excessive throughput architectures as much as 10 Gbps. Client is ready to use multiple Sensor and mainly cowl any bandwidth, even on the ISP degree.
During evaluation, THF Sensor can detect community anomalies akin to covert channels, tunnels, distant management, and numerous methods of lateral motion. It may extract electronic mail content material from mail site visitors and analyze it – this functionality is fairly attention-grabbing as a result of it permits it to identify passwords for archive recordsdata despatched in emails (and keep away from brute-forcing them).
There is a particular THF Sensor model tailor-made for industrial techniques — THF Sensor Industrial — which is ready to dissect ICS protocols. Sensor Industrial helps a wide range of ICS protocols (Modbus, S7comm, S7comm+, UMAS, OPCUA, OPCDA, IEC104, DNP3, DeltaAV, CIP, MQTT and different), and might detect topology modifications and management integrity of software program and firmware used on PLCs. It can be potential to arrange detection guidelines based mostly on insurance policies which can be accessible by the configuration choices.
THF Sensor can analyze encrypted classes by utilizing the THF Decryptor element, which detects TLS/SSL-protected classes, performs a certificates substitute and might route the proxied site visitors. THF Decryptor helps all in style TLS variations (1.1 – 1.3) and cipher suites. It will be deployed and works in numerous modes: clear (bridge) mode that works on OSI Layer 2 the place it’s invisible to the person community, or gateway (router) mode, the place it acts as a gateway for the person networks.
THF Huntbox
THF Huntbox is a central administration dashboard and reporting level of Group-IB Threat Hunting Framework. It is accessible as an internet utility and accommodates administration capabilities for THF parts (THF Sensor, THF Polygon, and THF Huntpoint) and acts as a correlation engine for managing occasions, alerts and incidents in addition to scalable storage for all collected uncooked logs and different knowledge. Through the THF Huntbox interface, customers can see occasion particulars, create experiences and escalate incidents, in addition to produce experiences and do menace looking within the native and international context. THF Huntbox acts as a front-end for THF Polygon’s dynamic evaluation experiences.
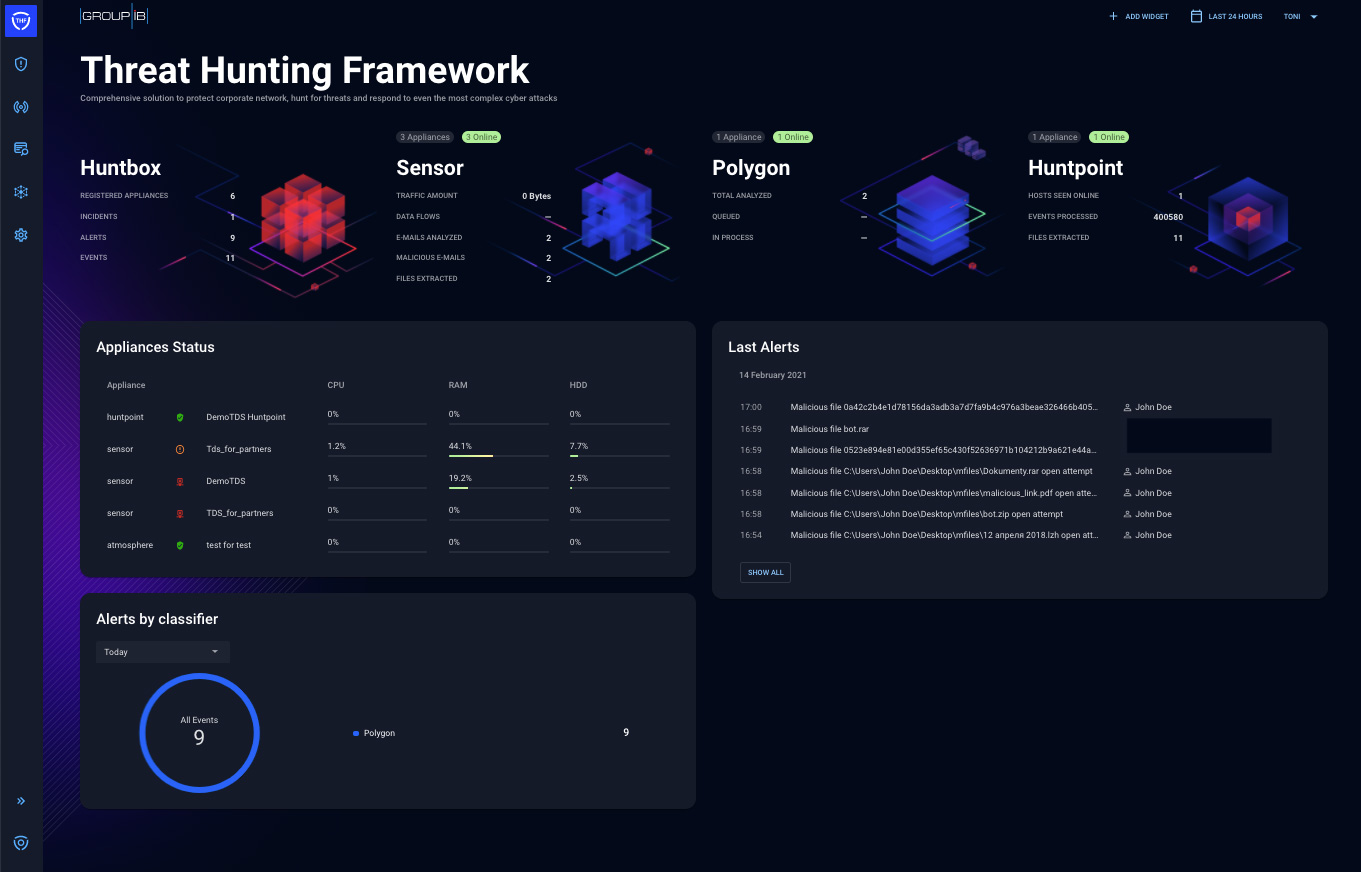
Figure 2 – The THF Huntbox welcome display screen is a dashboard containing the equipment standing, statistics and newest alerts
THF Huntbox has the next sections:
- Incidents – Critical tickets that want analysts’ instant consideration and determination. It is feasible to collaborate and touch upon the progress with different analysts inside your group. We collaborated with CERT-GIB, their help is a excessive worth service that may increase customers’ detection and response potential
- Alerts – Potentially malicious occasions escalated by numerous THF parts (e.g., THF Polygon, THF Huntpoint), containing correlated occasions and detection data
- Graph – Group-IB’s instrument for community evaluation working on Group-IB Threat Intelligence & Attribution database that accommodates menace knowledge and historic data of all community nodes (together with Whois historical past, SSLs, DNS data, and so on.) intelligence, but in addition unstructured knowledge collected from numerous underground communication channels, boards and social networks
- Investigation – All accessible occasions are situated right here. This part is split into:
- Emails – Containing all analyzed emails and detections of doubtless dangerous content material
- Files – Containing all of the recordsdata extracted from community site visitors, proxy-server, endpoints, emails, file shares. Files additionally could possibly be uploaded for dynamic evaluation manually or robotically with API. For each file there may be an accessible Polygon report that gives a verdict on whether or not the file is malicious or benign
- Computers – Containing particulars on and accessible actions (e.g., isolation from community) for all endpoints registered to the THF occasion
- Huntpoint occasions – Containing all occasions collected from Huntpoint purchasers
- Network connections – Containing extracted community connections from the sensors.
- Reports – Containing abstract experiences of all exercise in a given date vary and experiences associated to particular incidents, alerts or occasions.
Figure 3 – Correlation in motion: Multiple malicious emails despatched from the identical deal with resulted in an escalation of an incident
We spent more often than not within the Investigation part, looking for uncooked occasions and brushing the recordsdata and emails experiences. Events and their metadata will be built-in with SIEMs with syslog and with different monitoring techniques. THF correlates and aggregates occasions throughout all of its modules (e.g., electronic mail from THF Sensor and a THF Polygon evaluation of malicious attachment) and might block them robotically or manually, based mostly in your configuration, guidelines and insurance policies (see Figure 3 for electronic mail). THF Huntbox workflows are simple to get used to, assist cut back analysts’ cognitive load and permit them to give attention to actionable alerts. All triaging options are current in a central place and looking for further context is on the market beneath the Graph view.
THF Huntbox may change a classical ticketing system for monitoring incidents and alerts. The Alerts and Incident sections are useful for incident response workflows, a number of occasions will be robotically correlated and analysts can hyperlink alerts to incidents, manually correlate occasions and touch upon the timeline.
Alerts are normally triggered by particular indicators of compromise (domains, IPs, recordsdata, emails, Huntpoint occasions) discovered throughout menace looking actions. Incidents comprise one or a number of alerts and different related occasions that give extra context.
The collaboration possibility removes the necessity for having one other system for this particular function. Analysts can remark and fix recordsdata (though a wider view could be useful for prolonged feedback).
Figure 4 – Alert accommodates a timeline the place it’s potential to collaborate and touch upon new findings
THF Huntpoint
THF Huntpoint is a light-weight agent put in on endpoints that collects and analyzes all system modifications and person’s behaviour (80+ occasions sorts, together with created processes, inter-process communications, registry modifications, file system modifications, community connections, and so on.), and extracts recordsdata from the endpoints and forwards them to THF Polygon for extra evaluation. It is used to attain full visibility of a corporation’s endpoints and supplies a whole timeline of occasions that occurred on it.
THF Huntpoint detects anomalies and blocks malicious recordsdata and can be utilized to remotely acquire forensic knowledge wanted for triage or to isolate the contaminated machine throughout incident response. The occasions will be searched with a question language that’s just like different SIEM question languages, like Splunk and Elasticsearch. An instance of occasion particulars will be seen in Figure 5.
Figure 5 – Huntpoint Event particulars
Installing THF Huntpoint is an easy course of. We put in it manually, however it may be put in with Group Policy or by way of a specialised THF Huntpoint Installer that’s built-in with Active Directory.
We examined our endpoints with malicious recordsdata in numerous codecs (paperwork, executables, archives like ZIP, RAR, ISO). Our checks have been carried out with Windows Defender turned off to not intrude with THF Huntpoint’s detection capabilities. Huntpoint detected all malicious recordsdata on the primary attempt, recordsdata have been quarantined and triggered alerts seen in THF Huntbox, as proven in Figure 6.
Figure 6 – Malicious recordsdata detected with Huntpoint
THF Huntpoint offers a variety of perception into what is occurring on the endpoint. All person exercise – creating or opening of recordsdata/processes/threads/registry keys, community site visitors and extra – is seen beneath the Huntpoint Events part in Huntbox.
Figure 7 and eight – Huntpoint Events search by area identify and IP deal with
To carry out a easy take a look at, we created a textual content file (motion seen in THF Huntbox in Figure 5) and we visited helpnetsecurity.com (motion seen in THF Huntbox in Figure 7). Without digging deeply within the documentation, we efficiently discovered the wanted fields for querying occasions. Although, time and endurance are wanted to get used to area names and turn out to be nimble with Huntpoint occasions querying for extra advanced queries.
In THF Huntbox, it can save you searches for future investigations and even share these searches together with your colleagues. This turns out to be useful while you need to have a “cookbook” of fundamental queries to detect some in style misuse instances (e.g., suspicious PowerShell downloads).
The different THF Huntpoint checks that we carried out have been associated to malware infections. We contaminated our endpoint with ransomware, and the executable recordsdata have been despatched to THF Polygon for detonation and a last verdict. The infections have been efficiently detected (Figure 9) and have been seen in THF Huntbox beneath Alerts.
Figure 9 – Detection of ransomware that has been despatched to Polygon
During this final take a look at, the THF Huntpoint consumer on the endpoint consumed solely 20-40 Mb of RAM, with an unnoticeable stress on CPU utilization. From a efficiency standpoint, you get full visibility with minimal influence on assets. Due to an enormous variety of occasions through the ransomware an infection, we seen that there was a brief delay earlier than some occasions grew to become accessible in Huntbox, however after a while, all occasions have been accessible for querying.
We carried out easy checks to see if all situations that may be carried out by an attacker are recorded in THF Huntpoint and accessible in THF Huntbox. E.g., in Figures 10 and 11 you possibly can see the detection of Netcat use and of a easy encoded PowerShell execution of a command.
Figure 10 and 11 – Events containing Netcat and PowerShell misuse
We additionally tried utilizing Mimikatz to dump NTLM hashes current on endpoints, and this occasion was additionally efficiently detected and escalated to an incident (Figure 12).
Figure 12 – Use of Mimikatz detected on Huntpoint endpoint, seen as an alert
THF Huntpoint is on the market just for Microsoft Windows for now, however within the close to future must also be accessible for different platforms like macOS and Linux.
THF Polygon
THF Polygon is a file detonation platform. It is built-in in THF with the aim to investigate unknown recordsdata and emails in an remoted surroundings. The supply of recordsdata will be community site visitors from THF Sensor, ICAP integration for web-traffic evaluation, native/public file storage,the THF Huntpoint consumer or API integrations.
Group-IB has developed and maintains an open supply library to simplify integration with THF Polygon API so it could possibly be employed in any present utility or a workflow that offers with untrusted sources of URLs of recordsdata (ticket techniques, help chats, and so on). The library is on the market on GitHub and it’s very easy to begin utilizing it.
Another integration functionality we favored is the existing integration with Palo Alto XSOAR answer: this permits to ember THF Polygon to present safety workflows that run on XSOAR platform.

Figure 13 – Malicious habits markers of the analyzed file
The analyzed file is executed in an remoted surroundings, and after just a few (2-5) minutes you get the total habits evaluation report relating to the file, community, registry, course of occasions that have been recorded (Figure 13). You can preview the execution modifications by a video that reveals how the analyzed artifact behaves.
Behavior markers can be found as an inventory or as a populated MITRE ATT&CK matrix (Figure 14). You may view the file composition and the method tree (Figure 15), which will be helpful in detecting methods that contain course of modifications (e.g., course of injection or course of hollowing).
Figure 14 – Malicious markers in a MITRE ATT&CK matrix
All IoCs which can be collected with THF Polygon will be enriched utilizing Graph Network Analysis to get a worldwide context. THF Polygon will also be used by way of an API that may set off evaluation and fetch outcomes when it’s completed.
Figure 15 – Process tree within the THF Polygon report
As we described within the Methodology part of this evaluate, we tried sending malicious attachments to the monitored mailbox. In Figures 16-18, you possibly can see that the recordsdata that contained a malicious doc and the identical archived doc have been efficiently detected after scanning the recordsdata with THF Polygon. The mail integration is on the market for inside mail servers however there may be additionally a brand new element (Atmosphere) that may scan and detect assaults for mailboxes which can be cloud-based (e.g., Office 365 or Google for Business). The mail integration performs attachment and hyperlink evaluation, however may detect BEC and spear phishing (i.e., emails that always don’t comprise attachments or hyperlinks).
Figure 16, 17, 18 – Email processing and detection in motion
Graph view (Group-IB Threat Intelligence & Attribution)
Global Threat Intelligence & Attribution is a menace intelligence database and analytical instrument that’s the results of Group-IB’s efforts aimed toward meticulously gathering and scanning the web for greater than a decade. The database accommodates:
- The entire accessible IPv4 and IPv6 areas (scanned each day)
- 211 million SSH fingerprints
- 650 million domains with historic knowledge going again for greater than 16 years (together with DNS registration modifications, WHOIS data)
- 1.6 billion certificates
- Hashes of malicious recordsdata
- Data collected from boards and social networks
The interface is straightforward and just like that of one other Group-IB product – the Fraud Hunting Platform.
This THF element is invaluable, as a result of typically you possibly can spot a bizarre area or hash whereas investigating some occasions and also you want extra context round it. You copy the indicator within the Graph view and in seconds you’ve a complete related graph that lets you degree up your investigation capabilities.
For instance, we used a malicious area that was a part of Emotet campaigns, the result’s seen in Figure 19. You can refine your search outcomes by shrinking the timeline beneath the precise graph. Or you possibly can management the depth of the graph by defining the variety of steps that refines the variety of indicators you possibly can see from the principle one – that is useful with indicators which have a variety of interconnections.
Figure 19 – Graph displaying knowledge about an Emotet-linked area
THF takes care of personal knowledge and it’s compliant with numerous knowledge safety and privateness laws, so it makes use of masks to cover non-public data (e.g., phone numbers accessible from social networks). Graph is actually useful to analysts but in addition to regulation enforcement, as a result of it may be used to construct a whole picture of a malware marketing campaign’s back-end infrastructure. It will not be unusual for organizations like nationwide CERTs, INTERPOL and Europol to collaborate and associate with Group-IB in takedowns of malware infrastructure and operations.
Figure 20 – Files associated to a site
Graph Network Analysis allows the attribution of particular indicators to a selected menace, and in addition to correlate occasions that in the first place look unrelated. In Figure 21 you possibly can see that our area search resulted within the attribution to the Emotet marketing campaign. Compared to guide evaluation, which is usually a rabbit gap with single indicators spawning further ones that additionally need to be analyzed, graph evaluation saves your time while you discover a suspicious area in your logs.
Figure 21 – The area giatot365.com is attributed to Emotet, and uncovers individuals associated to it
Conclusion and verdict
Threat Hunting Framework is a rock-solid product rooted in Group-IB’s ample experience. It is constructed across the classical incident dealing with workflow frequent in Community Emergency Response Team. It is straightforward to make use of and usable to SOC analysts of all ranges and CISOs, who can get abstract experiences and statistics illustrating the safe degree of their infrastructure.
After the set up of THF Huntpoint and THF Sensor modules, you get all the instruments for menace looking in your group out of the field. In most instances, quick triage will be performed with out leaving THF Huntbox. Depending in your use case situation, THF can eradicate the necessity for a full-fledged SIEM and change its performance as a result of it’s constructed across the similar concepts.
THF has a really delicate studying curve. After you get used to the question language and occasion fields, you may get artistic in your menace looking endeavors fairly shortly. THF helps battle-tested instruments like Yara and Suricata that make it suitable with most menace intelligence sources, and allows you to make customized detection guidelines. It is fastidiously designed to cut back the variety of alerts and, consequently, analysts’ fatigue. This can typically come at the price of lowering some computerized detections on endpoints associated to pink teaming methods.
THF is a invaluable instrument for analysts and incident responders. It can not change human consultants, however it is going to discover anomalies and correlate them over numerous layers in order that they don’t need to do it manually. The lack of skillful analysts will be mitigated by utilizing the THF in collaboration with CERT-GIB or different supervisor safety companies suppliers that make use of THF as a safety platform. Group-IB runs an open partnership program for MSSPs all over the world to ship cutting-edge safety companies all through the world.
We can suggest Threat Hunting Framework as a result of it delivers on the promise of engaged on numerous layers (community, electronic mail system, recordsdata, endpoints, cloud) and offering actionable analytics from incidents/occasions.
The incident administration capabilities are accessible and shall be sufficient for many organizations. Group-IB Threat Intelligence & Attribution will improve the menace intelligence and looking capabilities in each group, allow quick triage or extra in-depth analyses, will save time and cut back the necessity for the combination of further feeds.





















![Top 6 Server Management Software and Tools Compared [2023]](https://ta-relay-public-files-prod.s3.us-east-2.amazonaws.com/icp/product_images/23db1d70048ad120d46c9ea0e43f22e5.png)

