For the previous year, one in every of Russia’s prime state-sponsored hacking models has spent its time scanning and probing the web for vulnerable email servers, in line with a report revealed yesterday by cyber-security agency Trend Micro.
The report offers with the actions of APT28, often known as Fancy Bear, Sednit, and Pawn Storm.
The group, believed to be working on behalf of the Russian army intelligence service GRU, has been lively since 2004 and is likely one of the two Russian teams which have breached the DNC’s email server in 2016.
Being one of many oldest state-sponsored hacking teams round, its actions have been recorded, analyzed, and labeled in nice depth throughout a giant variety of trade stories.
According to those stories, APT28’s main weapon for the previous decade has been the usage of spear-phishing campaigns. Through fastidiously crafted emails geared toward specifically chosen targets and the usage of zero-day exploits, APT28 operators have contaminated victims with a big selection of malware strains for more than 15 years.
Scanning the web for vulnerable servers
However, in a report revealed yesterday by Trend Micro, the cyber-security agency’s analysts have noticed an necessary change within the group’s operations.
While spear-phishing and malware have remained on the menu, Trend Micro says APT28 has additionally begun final year conducting scans of your entire web, in the hunt for vulnerable webmail and Microsoft Exchange Autodiscover servers — on TCP ports 445 and 1433.
It is unclear what assaults APT28 launches in opposition to servers it identifies as vulnerable, though it would not be arduous to think about they’d attempt to take over the unpatched system — both to steal delicate knowledge saved inside or use the email server as a pawn in different operations.
Taking over email accounts to launch phishing operations
But on prime of server scans, APT28 has additionally been busy with one other scheme, Trend Micro mentioned.
Through a community of VPN servers, APT28 operators connect with compromised email accounts on the email servers of respectable corporations.
Trend Micro believes APT28 is phishing the workers of respectable corporations and stealing their login credentials for company email accounts, or performing brute-force assaults to guess email account passwords.
Once they’ve credentials in hand, by way of a community of VPN servers, APT28 operators connect with the compromised accounts utilizing the stolen passwords.
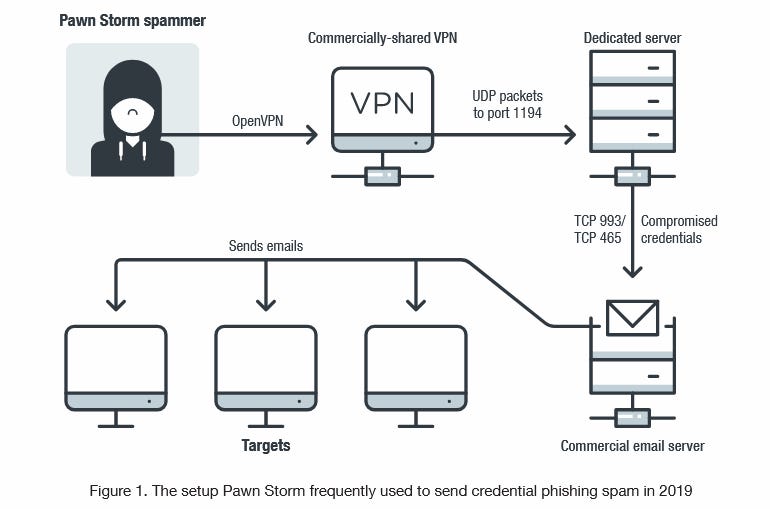
Here, APT28 both exfiltrate knowledge they discover of curiosity, or they use the compromised email accounts to ship phishing email campaigns to different targets.
Since the emails come from actual individuals at respectable corporations, these phishing campaigns are believed to be more efficient than most different phishing spam, supplying APT28 with new stolen credentials from new sufferer corporations.
Trend Micro says the overwhelming majority of corporations that had email accounts compromised are primarily based within the United Arab Emirates, and are working within the protection sector.
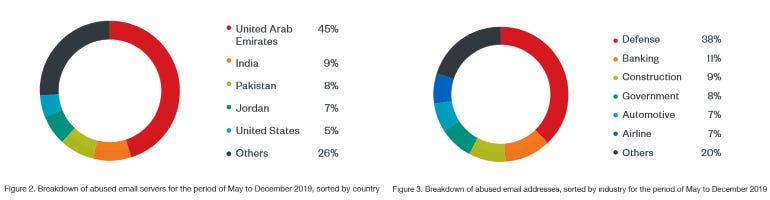
Image: Trend Micro
Below is a checklist of among the corporations that had email accounts compromised (and later utilized to ship out more phishing spam) by APT28 hackers between August and November 2019.
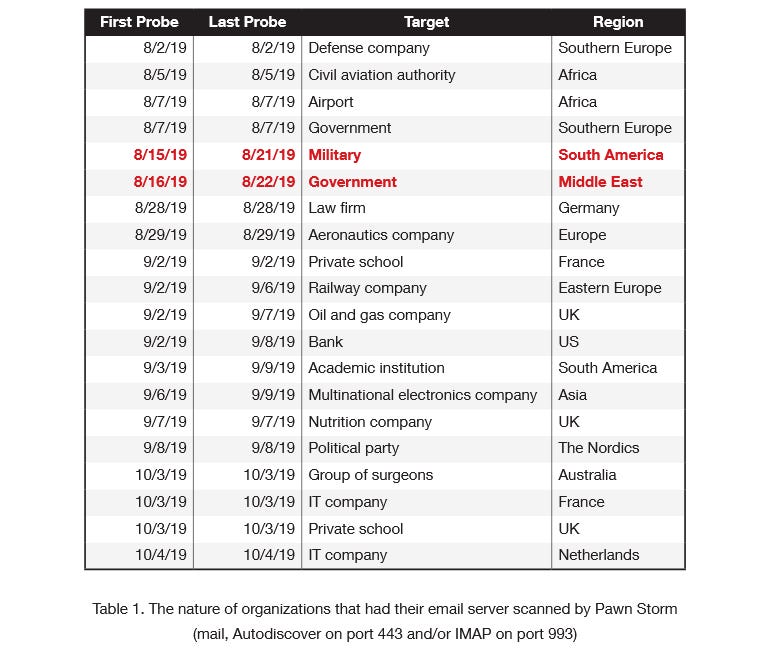
Image: Trend Micro
APT28’s new techniques present that this specific menace actor cannot be pigeonholed inside a specific menace matrix and can probably diversify its assault arsenal with out limitations — having proven the abilities and ingenuity wanted to adapt to new techniques prior to now.
https://www.zdnet.com/article/apt28-has-been-scanning-and-exploiting-vulnerable-email-servers-for-more-than-a-year/