Logging is a vital facet of Linux server administration. Log messages are helpful for root trigger evaluation and avoiding potential error occurrences sooner or later. Analyzing and debugging server errors is a core talent to have for each IT engineers and system directors.
This information will present you ways to arrange a distant logging server, also referred to as a log host, on Linux. A log host permits you to combination native Linux logs to a distant centralized server for ease of entry and evaluation.
Why Have a Dedicated Log Server?
The Linux working system logs most actions on your server for auditing and debugging utilizing the syslog (system logging protocol) daemon. So you could be questioning, why do I would like a devoted server for my logs? Here are some benefits to having a devoted logging server:
- Better safety as a result of the distant logging server solely has a couple of ports open to the skin.
- Improved server efficiency as a result of the distant logging host doesn’t run many companies, besides those used for logging.
- Eases archiving and administration of log messages.
Log messages are essential for auditing your servers and base-lining and are a core a part of preventive upkeep procedures on your server infrastructure.
Step 1: Installing rsyslog on Linux
This information focuses on Ubuntu 20.04, however the course of must be just about the identical if you’re utilizing different mainstream Linux distros.
rsyslog is a distant logging service for Linux and comes preinstalled by default on most trendy Linux distros, for instance, Ubuntu and different Debian-based programs.
The rsyslog service is a contemporary and improved daemon to syslog, which solely permits you to handle logs regionally. With the rsyslog daemon, you may ship your native logs to some configured distant Linux server.
If you should not have rsyslog put in on your PC, you may simply accomplish that utilizing the next command, on Debian-based distros:
sudo apt set up rsyslogOn Red Hat Linux, you may set up it by typing:
yum set up rsyslogOn Fedora and its derivatives, run:
dnf set up rsyslogTo set up rsyslog on Arch Linux:
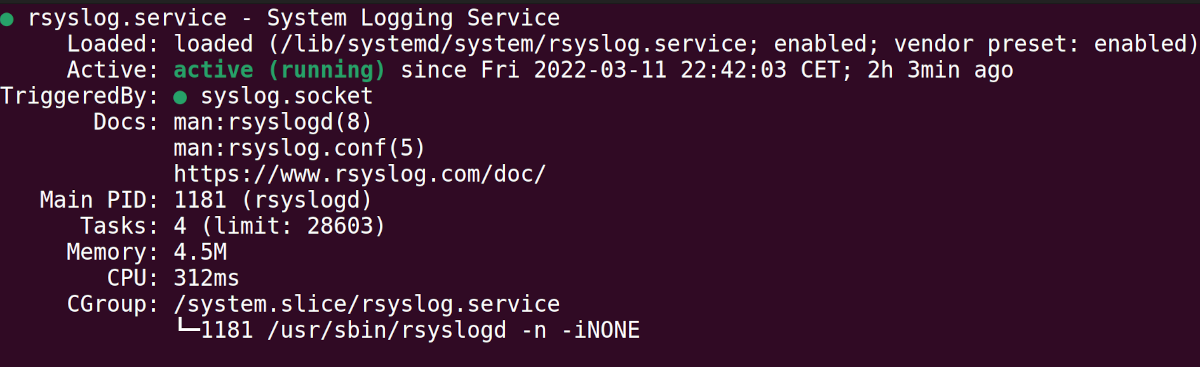
yay -S rsyslogTo test the standing of rsyslog, run the next command:
systemctl standing rsyslogOutput:
Step 2: Configuring the Log Host Server
The log host is the server configured to obtain log messages from different servers or PCs. The rsyslog configuration resides within the /and so forth/rsyslog.conf file.
You can open the /and so forth/rsyslog.conf file utilizing any text editor of your choice. In this information, we’ll use Vim.
You’ll want elevated privileges to make adjustments to the config file.
Before you begin modifying the config file, it is best to take a backup or copy of the file. To accomplish that, run the command:
sudo cp /and so forth/rsyslog.conf /and so forth/rsyslog_original.configNext, open the /and so forth/rsyslog.conf file utilizing a textual content editor.
sudo vim /and so forth/rsyslog.conf There are two protocols you should utilize for sending/receiving log information with rsyslog: TCP and UDP. This information exhibits you ways to configure each.
You don’t want to configure each UDP and TCP for distant logging to work. Only select one of many two.
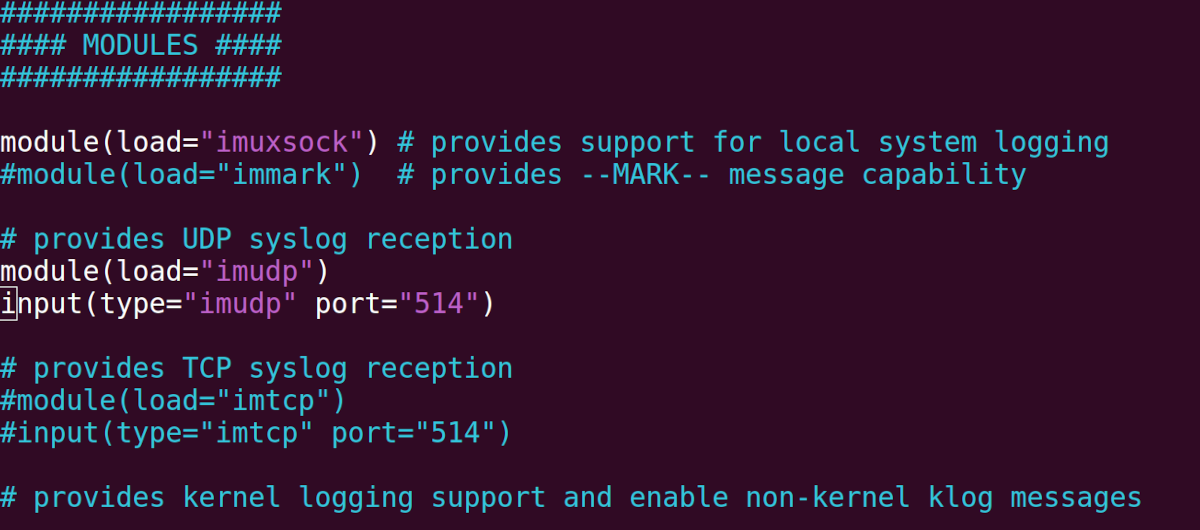
If you like to use UDP, search for and uncomment the next strains by eradicating the main Pound (#) image previous the strains. You can discover these strains underneath the modules part of the config file.
module(load="imudp")
enter(sort="imudp" port="514")If you like to use TCP, then uncomment the next strains by eradicating the main Pound (#) image positioned initially of the strains:
module(load="imtcp")
enter(sort="imtcp" port="514")The following determine exhibits the rsyslog configuration file configured to use UDP communication:
Next, configure the placement the place rsyslog will retailer your logs. For higher group, it is best to categorize incoming logs by their origin. Define a template in your rsyslog config file by including the next strains:
$template remote-incoming-logs, "/var/log/distant/%HOSTNAME%".log
*.* ?remote-incoming-logsThe aforementioned strains command rsyslog to retailer the logs within the folder /var/log/distant/hostname, the place hostname is the title of the distant consumer that’s sending log messages to the log host.
Now, save the adjustments you’ve got made. If you’re utilizing Vim, here is how to save and quit a file.
Finally, restart the rsyslog companies for the adjustments you’ve got made to take impact.
sudo systemctl restart rsyslogStep 3: Configuring Your Firewall
If your firewall is enabled, be sure that the port you’ve configured above is ready to talk with the skin world. You’ll want to edit your firewall guidelines to permit incoming logs.
For Debian-based distros, merely use the UFW instrument, to allow both the UDP or TCP switch protocol.
If you’re utilizing UDP, run the next command, the place 514 is the configured port quantity:
sudo ufw 514/udpIf you’re utilizing TCP on port 514, merely run:
sudo ufw 514/tcpOn Fedora, you should utilize firewall-cmd to obtain related outcomes.
firewall-cmd --zone=zone --add-port=514/udpFor Red Hat Linux, open the iptables file positioned at /and so forth/sysconfig/iptables utilizing your textual content editor of selection, and add the next rule:
-A INPUT -m state --state NEW -m udp -p udp --dport 514 -j ACCEPTRestart the iptables service for the adjustments to take impact.
service iptables restartStep 4: Configuring the Logging Client
The consumer is the machine that sends its logs to a distant or centralized log host server. Open the rsyslog config file positioned at /and so forth/rsyslog.conf:
sudo vim /and so forth/rsyslog.confAdd the next line if you’re utilizing UDP, the place 192.168.12.123 is the IP tackle of the distant server, you may be writing your logs to:
*.* @192.168.12.123:514If you’re utilizing TCP, add the next line as a substitute. Note that the road has two @ symbols.
*.* @@192.168.12.123:514
Save your adjustments and restart the rsyslog service on the consumer with the command:
sudo systemctl restart rsyslogStep 5: Viewing the Log Messages on the Server
You can use SSH to log in to your distant server and think about the logs despatched from the consumer servers. In this case, rsyslog is configured in order that it shops the consumer logs within the /var/log/distant listing of the distant server.
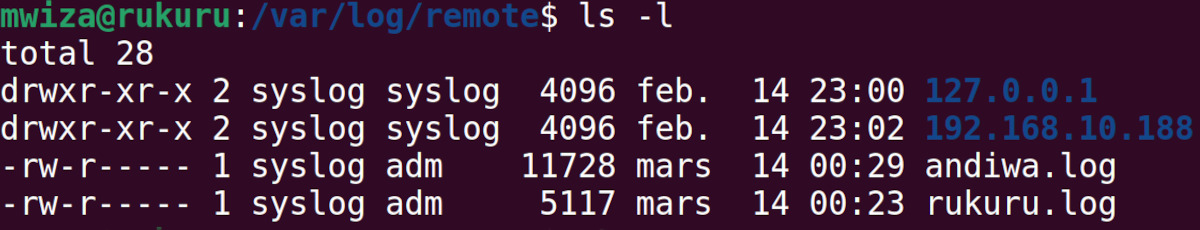
cd /var/logs/distantThen checklist the contents of the listing utilizing the ls command:
ls -lAs you may see within the output, the listing incorporates log messages for the distant servers named andiwa and rukuru. Their log information are named andiwa.log and rukuru.log respectively.
You can then have a look at the log information utilizing a textual content editor or with Linux file viewing tools akin to cat or much less.
Remote Logging Gives You More Control
This information has checked out how to arrange a distant logging server (log host) on Linux.
A log host affords you higher group and management when it comes to logging. Even in situations the place a system is broken or inaccessible, you may nonetheless view its logs from the log host and determine what went incorrect.
Read Next
About The Author
https://www.makeuseof.com/set-up-linux-remote-logging-using-rsyslog/