- Tuesday
- July 1st, 2025

After the recent series of technical Best Current Operational Practices (BCOP) documents that we initiated and co-authored, it’s time for new one. This time on how to run an incoming email server on IPv6 and survive! Back in 2010 we...

With the festive season fast approaching, online retailers everywhere will be busily preparing themselves to meet the bulk demands of customers but another community is also waiting in the wings. The festive season is a primetime for nefarious cyber criminals...

Authenticity is hard to come by on the internet, and nowhere is that more apparent than with emails. A message which appears to come from your bank, your healthcare provider, or your ISP often turns out to be an attempt...

Exploring ways to protect customer information is crucial for small businesses. Whenever a customer entrusts you with their private data for transactions or other services, it’s not just a transaction—it’s a commitment to their privacy and safety.In today’s digital age,...

In 2023, cyberattacks rose 7% and this includes retail cyber threats. You’re wrong if you think online threats are confined to ransomware attacks. Retail cyber threats are numerous, from altering gift cards to deceiving self-checkout systems through swapping barcodes. It...
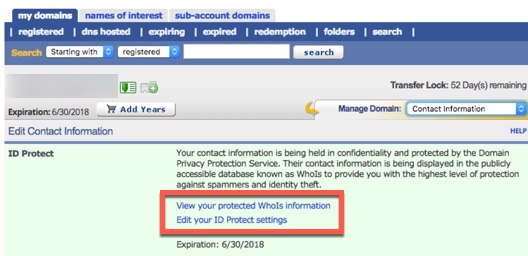
ID Protect (domain privacy) is typically added or not added through eNomCentral when a web hosting reseller registers a domain. Changes to the ID Protect settings are made through the eNomCentral account interface. Follow the steps to learn more about...

Distributed Denial of Service (DDoS) has been a plague on the Internet for decades. DDoS is a cyberattack that overwhelms servers or users with voluminous traffic or requests, affecting performance and user experience. While several mitigation techniques exist to protect servers...

Details Published: Thursday, 22 December 2022 09:13 It’s well-known that e mail is among the most essential assault vectors for company programs, however how do you retain up with assault developments? Mike Puglia presents some recommendation…Since e mail was first...

Twitter is in chaos. Elon Musk, its new proprietor, has decimated its employees and this week gave these remaining an ultimatum — work grueling hours and be “extraordinarily hardcore ” or go away. Hundreds selected the latter and headed for...
 Loading posts...
Loading posts...  All posts loaded
All posts loaded
No more posts

