- Friday
- April 19th, 2024

Remote working has elevated organizational publicity to cybersecurity threats. In flip, this has modified how incident response (IR) groups are ready to reply to potential safety incidents. IR groups don't all the time rush to a crime scene, however managing...

f11photo/Shutterstock.com CES is thought for kicking off yearly with new and innovative products. Unfortunately, on account of present circumstances, many firms decided not to attend CES 2022 in person, however that didn’t cease them from unveiling some of essentially the...
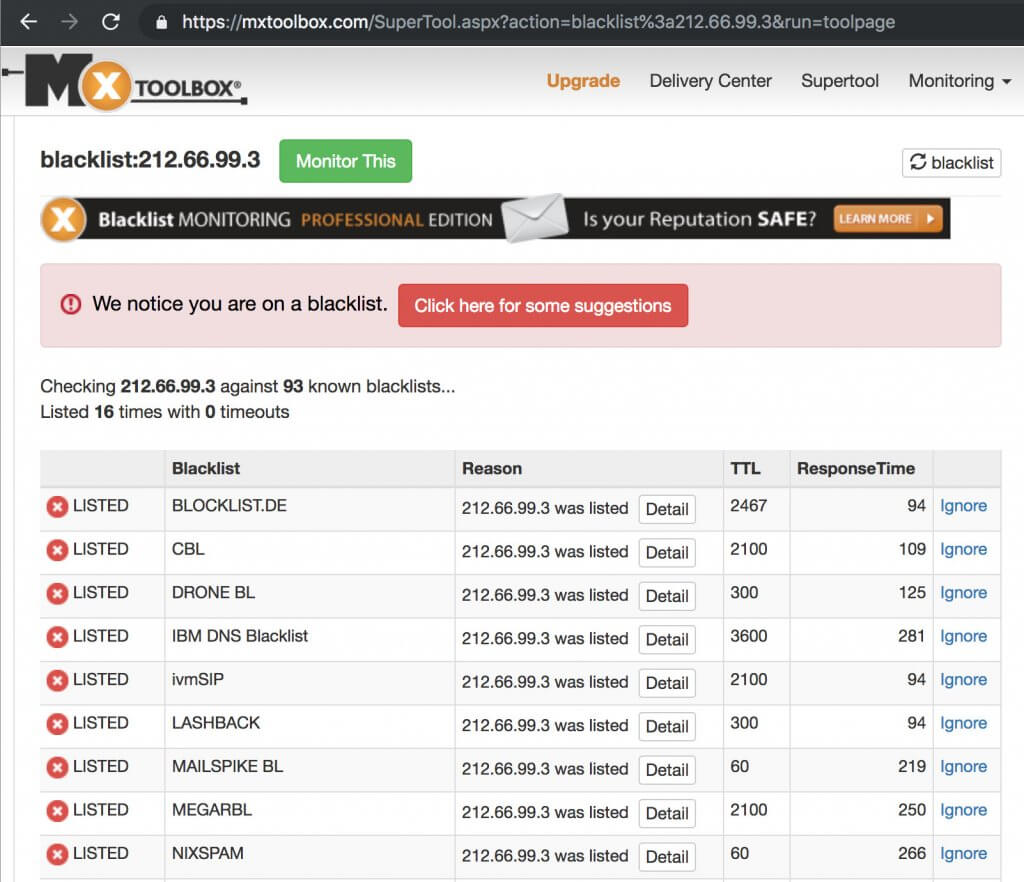
This is a multi-part article. In Part 1., we revealed how big law firms in Australia are susceptible to direct email spool attacks and what the implications had been. In a nutshell, we discovered that the e-mail safety resolution at one-third of...

