- Friday
- April 26th, 2024
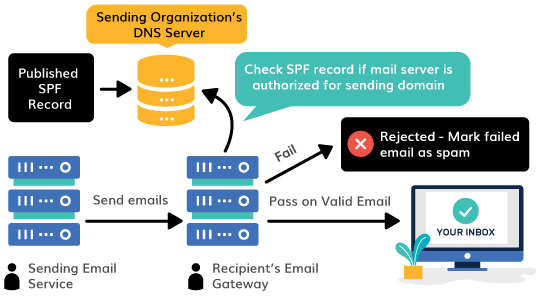
SPF (Sender Policy Framework) is an email authentication protocol designed to detect email spoofing and prevent unauthorized senders from sending messages on behalf of a particular domain. SPF email records help maintain a list of verified senders for your domain...

Can you defend against email threats better than the security companies? How well do the main email platforms handle threats? Is it worth paying for additional email security from a third-party specialist? Or could you create your own secure email...

It’s not sensible to check DMARC vs. DKIM. They’re each authentication protocols used to validate emails, prevent spoofing, and safeguard your e-mail area. But that’s the place the similarities finish. While each protocols use public key cryptography, every makes use...
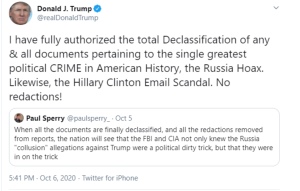
Former President Trump lately urged that the sitting President merely must “assume” one thing is declassified to be able to declassify it. Is there a cascade of more and more formal methods to declassify? Perhaps: Think the knowledge is declassified...

WordPress is, at its core, an online utility, and similar to each different internet utility, it requires and makes use of a labyrinth of folders and recordsdata to work. These recordsdata and folders embody all the pieces from entry controls...

× SUBSCRIBE TO OUR BLOG Get our new blogs delivered straight to your inbox. Subscribe THANKS FOR SIGNING UP! We’ll be certain that to share the most effective supplies crafted for you! 12 minutes learn Written by Serkan Özal...
