Source: Unsplash
Iranian cybercrime group, MuddyWater, used professional corporations’ emails in phishing assaults, Deep Instinct reported of their latest weblog, New MuddyWater Threat: Old Kitten; New Tricks. The attackers tried to set up malicious distant administration software program on recipients’ methods by sending spam hyperlinks as HTML attachments—a tactic to evade e mail safety options.
Since 2017, the group has focused personal and authorities organizations in varied sectors throughout Europe, North America, the Middle East, Asia, and Africa. But the group switches modus operandi for every assault to conceal its signature.
However, all their actions focus on phishing assaults. They use e mail and remote administration tools to scam businesses and people. This time, MuddyWater used Syncro—a distant administration device for Managed Service Providers (MSPs). But of their earlier operations, they relied on RemoteUtilities and ScreenConnect.
Sending Spam as HTML Attachments to Evade Detection
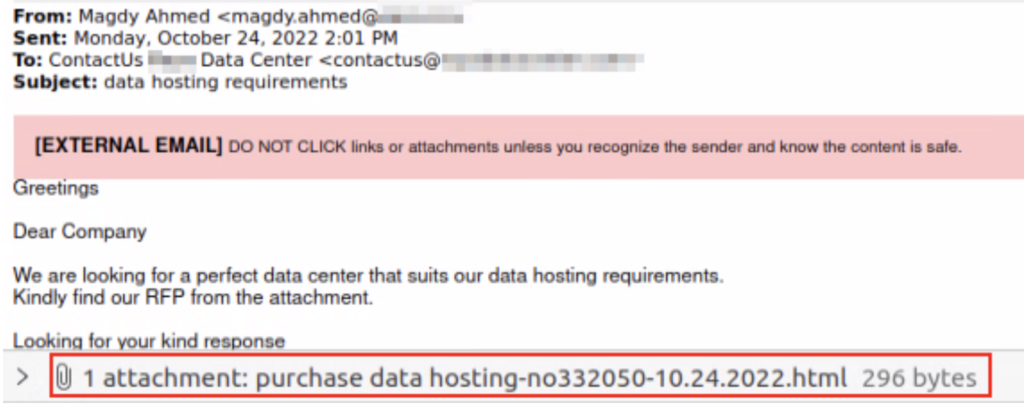
Source: Deep Instinct
Spam hyperlinks despatched as HTML attachments are harmful for 2 causes. First, corporations typically overlook HTML attachments of their phishing consciousness coaching as a result of they aren’t archived or executable recordsdata. And second, although email filtering and scanning solutions can detect spam HTML attachments, blocking requires extra safety checks. Few corporations usually take these additional steps. Knowing this, MuddyWater selected to ship the spam hyperlinks as HTML attachments as an alternative of within the e mail physique, as is the apply in typical phishing assaults.
Researching MuddyWater’s phishing assaults, investigators have discovered OneDrive archives containing Syncro MSI installers as locations of the HTML hyperlinks. MuddyWater cybercriminals used the identical tactic to spam contacts within the insurance coverage area from the e-mail tackle of a trusted Israeli firm in hospitality. And on one other event, they used a professional Egyptian internet hosting firm’s tackle to e mail one other Egyptian internet hosting firm. In doing so, they had been banking on unsuspecting staff clicking on the attachments, trusting the mail’s obvious supply.
No matter how elaborate the setup, all phishing scams depend on the recipient inside a community to click on on a hyperlink that downloads or runs an executable file. Investigators don’t but know whether or not MuddyWater has entry to just one e mail account or the entire e mail server of the businesses whose addresses it used.
Syncro—A Popular Choice for Cybercriminals
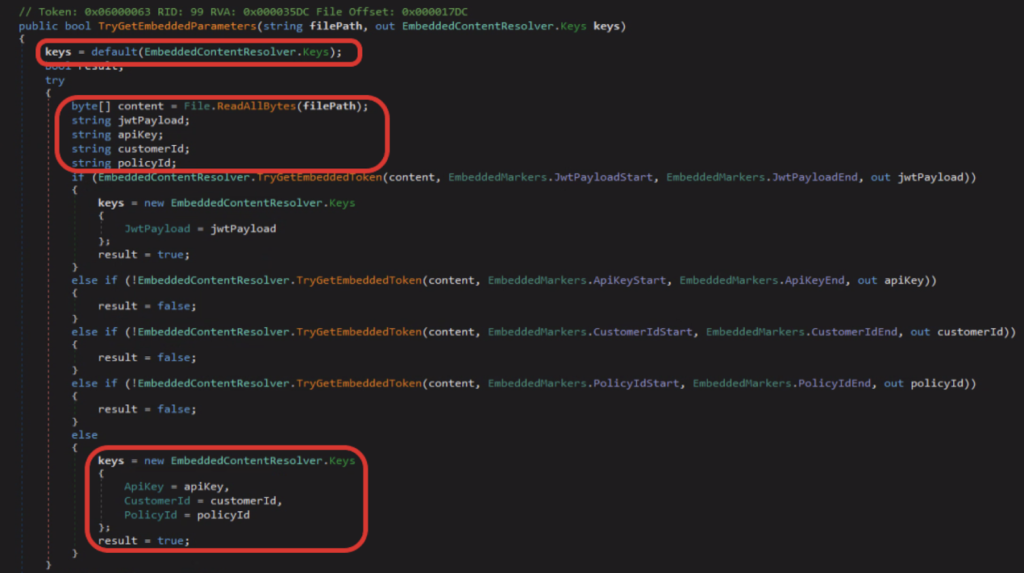
Source: Deep Instinct
So, what occurs when a consumer clicks on the Syncro installer hyperlink? Cybercriminals get distant entry to the machine. Syncro is a favourite amongst cybercriminals for distant machine management. Plus, it even provides a free 21-day trial. “Syncro supplies an agent for MSPs to handle any gadget that has Syncro put in with the custom-made supplied MSI file that features the customerID,” the Deep Instinct weblog learn.
With its GUI, Syncro permits cybercriminals to management computer systems as soon as recipients unknowingly set up the distant file. It doesn’t cease there, although. It additionally offers cybercriminals SYSTEM privileges, distant desktop entry, full file system entry, duties, and providers supervisor. These privileges permit cybercriminals to inflict severe harm on customers and companies. As the report states, a menace actor with distant entry by way of Syncro has near-limitless choices, as seen in BatLoader and LunaMoth operations.
LunaMoth used Syncro to steal company knowledge after which demanded ransom. On the opposite hand, Batloader mimicked search engine outcomes for skilled functions like Zoom, TeamViewer, and Microsoft Visual Studio. Using a visitors route system (TDS), attackers obtained customers to click on on malicious functions within the outcomes. Once clicked, the hyperlink executed a professional Windows DLL with a malicious VBScript to change Microsoft Defender settings.
Staying Safe from Phishing Attacks

Source: Deep Instinct
The enterprise e mail compromise (BEC) stays an environment friendly manner for cybercriminals to take down networks. Cybercriminals exploit staff’ lack of expertise about scams. Managers and homeowners can ship staff updates on cybersecurity tendencies and practices to guarantee they continue to be knowledgeable.
To restrict their vulnerability, corporations can put money into worker consciousness. Additionally, they have to arrange preventive measures, together with:
- Ensuring all emails are encrypted
- Turning on superior spam filtering and malware detection
- Using an e mail toolkit with anti-phishing expertise
- Preventing community customers from putting in any unverified executable file
- Blocking staff from accessing third-party e mail functions
- Ensuring staff have 2FA for his or her day by day e mail sign-in
- Encouraging staff to arrange a robust password for his or her e mail
- Archiving and deleting emails inside acceptable timeframes
- Ensuring staff change their passwords recurrently
- Enforcing and updating a strong email security policy
These measures will scale back spam, which is able to save corporations from phishing operations. Besides, decreasing spam additionally will increase worker productiveness and improves server load.
MuddyWater compromised firm e mail accounts using legitimate, free tools and services like Syncro and OneDrive. It did this by taking pains to construct a reputable facade, figuring out that the extra actual their spam emails appeared, the extra possible the e-mail recipient was to open hyperlinks or attachments.
Yet, their assaults failed as a result of poor phrase alternative within the e mail’s physique raised suspicion. Usually, obtrusive grammatical errors are a giveaway of spam content material—even when the supply’s e mail tackle seems professional.
Nonetheless, what’s most alarming is the benefit with which menace actors executed these assaults. Success would have put them in charge of the corporate or government-owned machines.
The room for error is small in these instances. And it solely takes one negligent worker or government to open a spam hyperlink to let in dangerous actors. For cybercriminals, it doesn’t matter if they’ve distant entry to one machine or a number of. All that issues to them is getting in.
https://information.google.com/__i/rss/rd/articles/CBMiRWh0dHBzOi8vdGVjaGdlbml4LmNvbS9waGlzaGluZy1hdHRhY2tzLXVzZS1sZWdpdGltYXRlLWNvbXBhbnktZW1haWxzL9IBAA?oc=5

![Top 6 Server Management Software and Tools Compared [2023]](https://ta-relay-public-files-prod.s3.us-east-2.amazonaws.com/icp/product_images/23db1d70048ad120d46c9ea0e43f22e5.png)



:max_bytes(150000):strip_icc()/registration-3938434_1280-e2aa7e5d57264ae19b69027f14c85c2f.jpg)
