Whether you’re a software program creator or gross sales supervisor, digital signatures are important to the safety and authenticity of your knowledge. Here are a number of of the ways in which you should utilize digital signature certificates to improve belief in your group
We stay in a world the place you actually have to query every part: is that this e mail out of your boss respectable? Is the software program replace you need to set up genuine, or is it a trojan that’s ready to infect your machine? When you log in to your favourite eCommerce web site, how have you learnt it’s respectable?
A digital signature certificates may maintain the reply in all of these instances. These tiny knowledge recordsdata assist your net or e mail consumer confirm that the file or different social gathering you’re connecting to is reliable and genuine. This approach, you don’t inadvertently share your delicate login data or different knowledge with cybercriminals.
But how will you use digital signature certificates to your benefit? We’ll go over all of that in simply a few moments. But first, we expect it could profit our newer readers to briefly recap what a digital signature is and why you want a digital signature certificates to create it.
Let’s hash it out.
Note: If you’re already properly acquainted with digital signatures and digital signature certificates, soar forward to our checklist of digital signature certificate use cases.
What Is a Digital Signature? A Quick Recap
Digital signatures, additionally referred to as public key signatures, are a cryptographic methodology of exhibiting who created a digital asset and making certain the merchandise hasn’t been modified by one other social gathering. Examples of such belongings embody emails, PDFs, Word recordsdata, software program utility codes, and so forth. Applications ceaselessly use visible marks of some type (e.g., a ribbon mark in Microsoft Outlook) to signify digital signatures.
These signatures are trusted since you want to have a particular file referred to as a digital signature certificates so as to signal them digitally. But earlier than you may get this digital certificates, a publicly trusted third social gathering (referred to as a certificate authority or CA) has to fastidiously vet your identification. Once you obtain and begin utilizing your digital signature certificates, it proves that no matter you signal is genuine as a result of it was created and signed by you, and your identification has been validated.
Digital signatures are a sort of electronic signature. But not like common digital signatures, which typically look related to handwritten signatures, digital signatures won’t look something like conventional signatures. Here are a few fast examples to showcase the distinction between digital and digital signatures:
How Digital Signatures Are Created
To create a digital signature, you first want to have a digital certificates in hand. A digital certificates is a small knowledge file that incorporates verified, figuring out details about you or your group. (This is the primary data that shows to customers.) But that’s not all that’s required. Without getting too technical, digital signatures are created by making use of two cryptographic instruments to the information you want to defend:
- A particular cryptographic perform (referred to as a hash function or hash algorithm) — This creates a hash worth (a mishmash of letters and characters) of a mounted size, which masks the true measurement of the enter and ensures the integrity of the information.
- A non-public key, which encrypts the hash worth — When the recipient receives or downloads the file, they’ll decrypt it utilizing the signer’s public key. This key ensures solely the meant person can learn the information.
Digital Signatures Enable You to Prove You and Your Files Are Legitimate
A digital signature validates your identification to different events and ties it to no matter you’ve created and signed. The vital takeaway right here is that digital signatures supply two key qualities that you just gained’t discover in common digital signatures:
- Authentication — This means you possibly can show that you just or one thing you created is respectable.
- Non-Repudiation — This ensures recipients that you just, and solely you, created or signed the merchandise in query; that an imposter didn’t fraudulently make it.
Historically, in case you needed to show that you just’re the respectable signer of a doc, you’d have to meet up with a public notary to have them observe you signing it. This course of required offering the notary with verifiable proof of identification — that is sometimes some type of ID from a trusted entity (i.e., your driver’s license or ID issued by your state or nation’s authorities).
This is ok in case you’re bodily situated in the identical space the place it’s simple to meet up to perform this course of. But what in case you’re attempting to do enterprise with somebody overseas? Meeting up face-to-face then turns into a lot extra difficult and dear.
So, the place do you discover digital signatures? All over the place, truthfully. You’ll discover digital signatures utilized in every part from web site connections to doc signing.
You Need a Digital Signature Certificate to Use Your Digital Signature
Digital signatures are sometimes saved in particular recordsdata generally known as digital certificates. For the sake of this text, we’ll name them digital signature certificates. Digital signature certificates are small digital recordsdata that allow you to use these signatures on-line.
A number of examples of these digital signature certificates embody:
Of course, there’s one other sort of digital certificates that makes use of digital signatures: an SSL/TLS certificates. This file is what permits you to show that your web site is respectable as a result of it’s been signed off on by a trusted CA (like DigiCert or Sectigo). But we’ll speak extra about that in a little bit.
Okay, now that we’ve got all of that out of the way in which, let’s soar proper to what you want to learn about how you should utilize every of these digital signature certificates…
5 Digital Signature Certificate Use Cases For Your Business
For just about all of our readers, you’re doubtless already utilizing digital signature certificates in a method or one other (you simply won’t realize it). However, there could also be some use instances that you just’re not as aware of or aren’t certain how to implement inside your IT atmosphere. We’re right here to discover these and extra:
1. You Need a Way to Show Your Microsoft Office and PDF Files Are Authentic
Nowadays, you virtually can’t do something inside what you are promoting with out utilizing Word, Excel, or PDF recordsdata. Of course, you’d like to assume that somebody will ship you solely respectable recordsdata through e mail. However, the fact isn’t as fairly. While it could be true, say, 90% of the time, the remaining proportion is sufficient to crack these rose-colored glasses.
As current cyber security statistics and cyber crime statistics present, the risk panorama continues to change. New risk actors seemingly arrive on the scene nearly day by day and assault strategies evolve with them. For instance, SonicWall reports the prevalence of malicious Microsoft Office recordsdata decreased 64% in 2021; malicious PDFs, then again, elevated 52%.
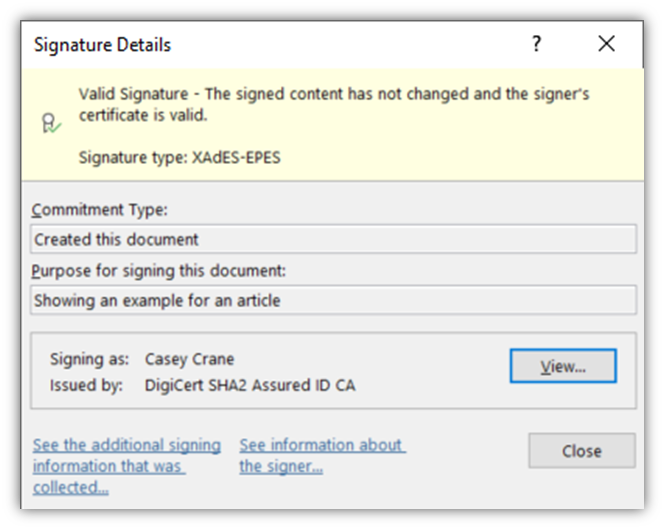
So, how will you present customers that your paperwork and recordsdata are respectable? Digitally signal them first utilizing a doc signing certificates. For instance, that is what it seems to be like while you signal a Word doc utilizing a doc signing certificates:
Here’s what it seems to be like while you signal an Adobe PDF file with an relevant digital signature certificates:

2. You Want to Eliminate Warning Messages When Users Download Your Software
SonicWall’s 2022 Cyber Threat Report knowledge reveals that malicious executables represented a whopping 30.27% of the cybersecurity firm’s malicious file detections. As such, as a software program developer or writer, you want to have a approach to present that:
- Your software program is genuine,
- It’s truly from you, and
- No one’s modified it.
You can do that utilizing a code signing certificates. These certificates are sometimes provided with two choices of validation ranges: organizational (i.e., customary) and prolonged. (Note: Some certificates authorities supply particular person validation as properly.) When you utilize this sort of digital signature certificates to signal your software program, you connect your group’s verified data to the file regardless of the validation sort you select.
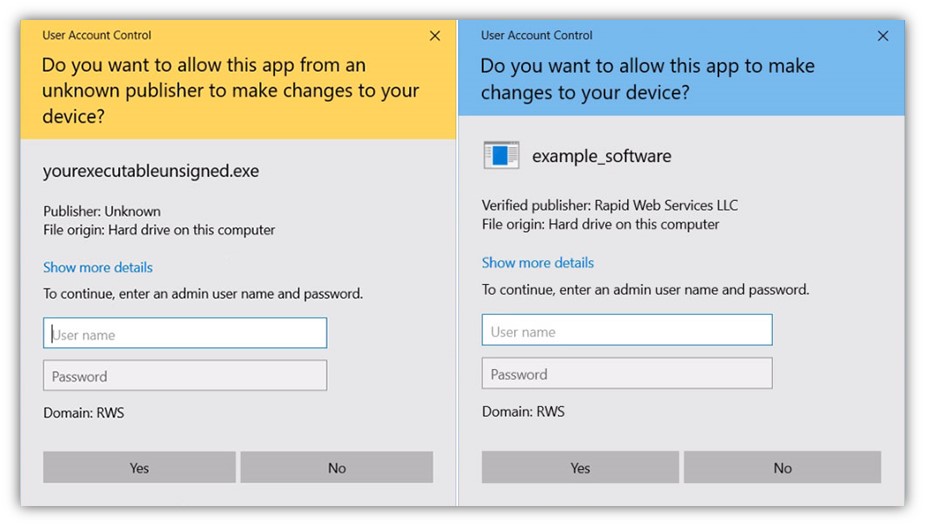
Both varieties of certificates are trusted routinely by browsers and working programs. The massive distinction between the 2 validation ranges is that Windows Defender SmartScreen requires an EV certificates in case you don’t need an unsightly warning message to pop up:
3. You Want to Give Customers and Prospects a Reason to Trust Your Website
Trust is tough to earn but fragile as glass. Once you earn your clients’ belief, you want to do every part attainable to defend it. Having a approach to show that your web site — your model’s digital illustration — is respectable is important to that mission.
Every time you go to your favourite web site, the server sends your browser a file (i.e., an SSL/TLS certificates) containing essential figuring out knowledge that proves you’re connecting to the suitable server. This website security certificate is issued and digitally signed by a publicly trusted entity generally known as a certificates authority (CA). The CA’s trusted root
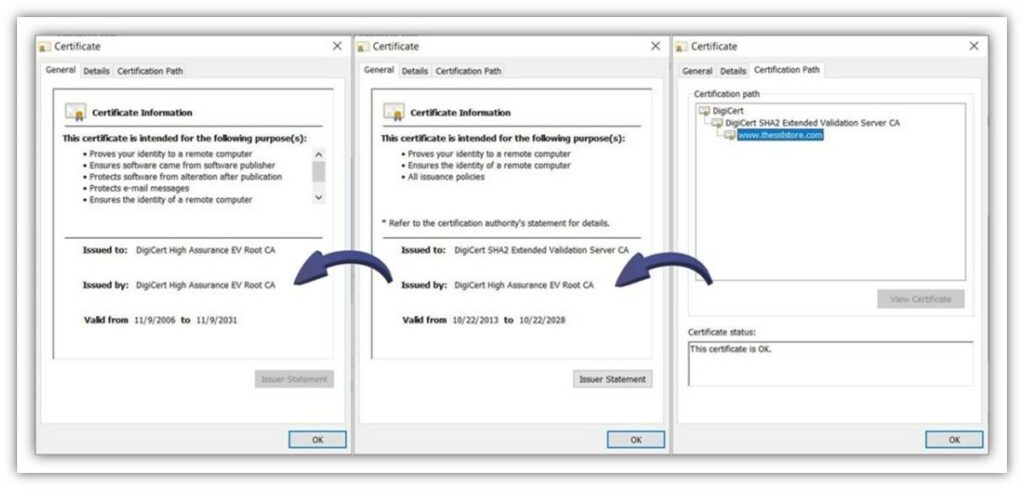
The CA’s digital signature signifies that this globally trusted entity is vouching for you, saying that you just’ve, primarily, been vetted and are trusted. Having such a approach to show your group’s authenticity is especially essential when you think about current data from Bolster reveals that their programs detected practically 10.7 million phishing and rip-off pages in 2021 alone. To put this in additional relatable phrases, it means Bolster’s staff detected a mean of 29,190 fraudulent pages on daily basis all year long.
Want your genuine web site to stand out from the ocean of fraudsters’ websites? Then slap your vetted and validated identification on it by putting in an SSL/TLS certificates instantly. In addition to asserting your digital identification, SSL/TLS certificates allow customers to talk securely along with your web site. If you put in an prolonged validation (EV) code signing certificates, then you definitely take your digital identification to one other degree by displaying your verified firm data upfront. This approach, customers don’t have to dig round your certificates data to discover the small print.
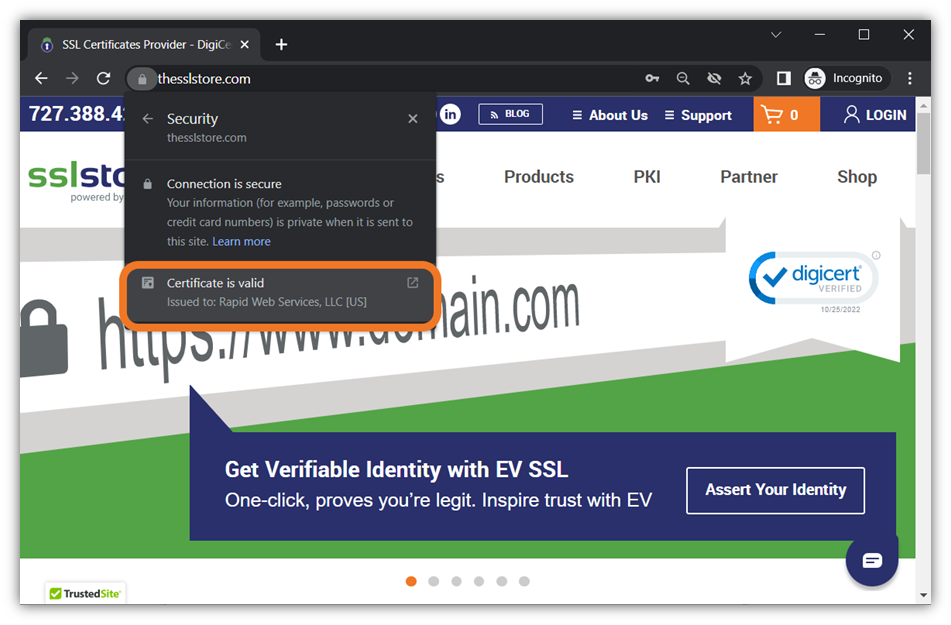
4. You Need to Prove to Recipients That Your Email Communications Are Authentic
Phishing is one of the highest cyber assault strategies utilized by cybercriminals. Verizon’s 2022 Data Breach Investigations Report (DBIR) knowledge reveals that e mail is one of the 2 main assault vectors utilized in recognized knowledge breaches. Furthermore, their report signifies that 75% of the malware the median group acquired in 2021 got here through e mail.
Sure, you possibly can — and will — practice your workers to acknowledge the threats related to phishing assaults and social engineering. But it doesn’t harm to add one other extra technical layer of safety to the equation; that is the place digital signature certificates for e mail come into play.
These certificates are generally known as e mail signing certificates or S/MIME (single/multi-purpose web mail extension) certificates. They enable you to connect your digital signature to messages so your recipients can affirm they got here from you. These certificates supply the additional advantage of enabling you to encrypt your emails as properly. This helps to present end-to-end encryption by securing the emails earlier than they depart your e mail server.
Here’s a fast have a look at what a digitally signed e mail seems to be like to your recipient:
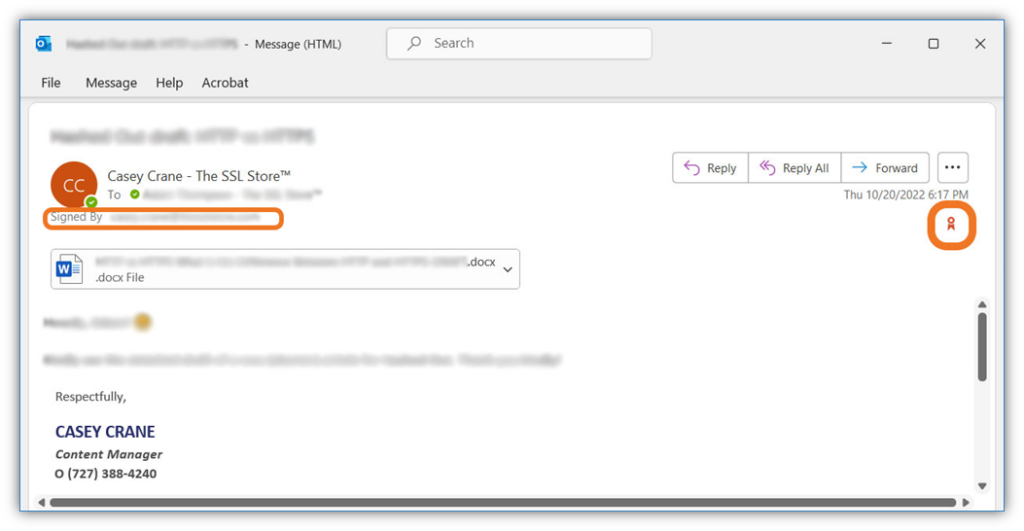
5. You Want to Authenticate Without the Risks Associated with Traditional Passwords
There’s no such factor as a good authentication methodology; an enterprising cybercriminal will inevitably discover a approach to authenticate as you (fraudulently) in the event that they’re really motivated. But the objective is to make your self as troublesome a goal as attainable; this manner, 99% of cybercriminals will quit and transfer on to the following goal. Make your self one of the hardest-to-reach fruits on the tree as a substitute of one of the easy-to-steal, low-hanging fruits.
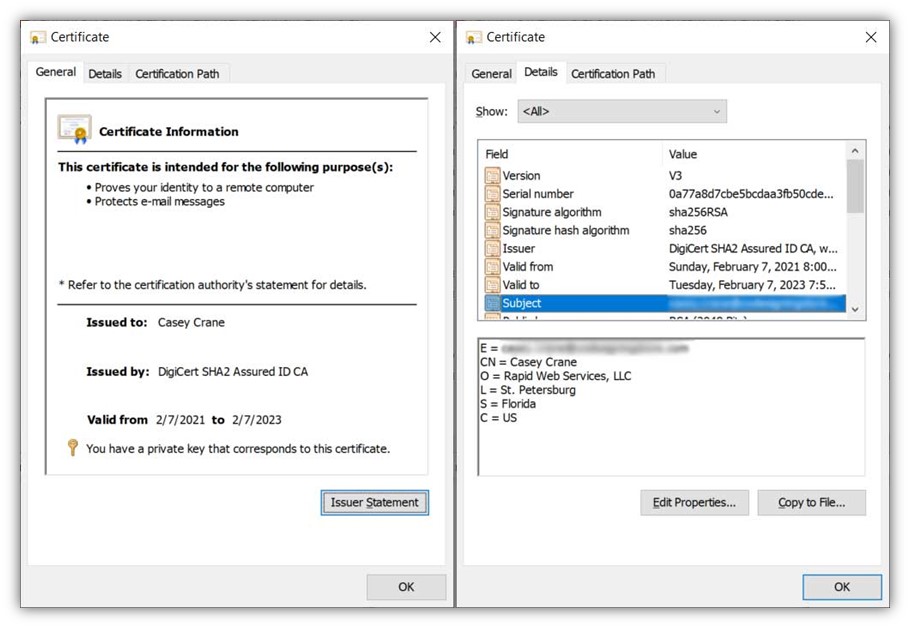
This is the place a sort of digital signature certificates, generally known as a consumer authentication certificates, can turn out to be useful. A consumer authentication certificates permits you to authenticate with out having to sort in a username or password. Instead, you may have a PKI certificates put in in your machine, enabling you to authenticate routinely.
Why is that this mandatory? ForgeRock reports that fifty% of cyber assaults they studied had been due to unauthorized entry by varied account compromises. Of course, there are various methods accounts can turn into compromised. One of the most typical strategies is phishing, which entails an attacker stealing a person’s login data utilizing social engineering techniques.
Using PKI-based authentication as a substitute of a username-password mixture means you not have a password that may be phished or stolen through malware. You merely go to the net app or system you may have permission to entry, and the authentication “magic” occurs on the backend routinely. No muss, no fuss.
Final Takeaways on Digital Signature Certificates
It’s now extra vital than ever to safe your group’s digital identification and knowledge. Choosing to use a digital signature certificates to safe your digital belongings is the distinction between sending or receiving authenticated communications or recordsdata as a substitute of unauthenticated (and doubtlessly harmful) ones.
To get a digital signature certificates in your web site, emails, paperwork, or software program:
- Evaluate what you want to safe and authenticate.
- Go to your favourite CA or approved reseller’s web site.
- Choose the certificates(s) based mostly on the kind(s) of protection and validation sort.
- Purchase your certificates(s).
- Generate a certificates signing request (CSR) for area validation (DV) and group validation (OV) certificates, if relevant.
- Provide the CA with the mandatory organizational data to full validation.
- Collect your digital signature certificates and set up it in your server, machine, or consumer.
- Start utilizing your certificates instantly!
https://information.google.com/__i/rss/rd/articles/CBMiTWh0dHBzOi8vd3d3LnRoZXNzbHN0b3JlLmNvbS9ibG9nL3doZW4tdG8tdXNlLWEtZGlnaXRhbC1zaWduYXR1cmUtY2VydGlmaWNhdGUv0gEA?oc=5

![Top 6 Server Management Software and Tools Compared [2023]](https://ta-relay-public-files-prod.s3.us-east-2.amazonaws.com/icp/product_images/23db1d70048ad120d46c9ea0e43f22e5.png)



:max_bytes(150000):strip_icc()/registration-3938434_1280-e2aa7e5d57264ae19b69027f14c85c2f.jpg)
