During a group dinner in a small city in Norway in 2015, at a global convention for investigative journalists, a Ukrainian reporter informed me that he used each Gmail and Mail.ru, Russia’s hottest e-mail supplier. “Every time I write an e-mail,” he mentioned, “I’ve to resolve if I need Obama to learn it, or if I need Putin to learn it.”
It could also be hyperbolic to counsel that world leaders personally comb by way of particular person e-mail accounts, however the reporter’s level stands: When you employ companies like Gmail, Mail.ru, Facebook, Dropbox, Slack, or every other website that shops your information, they are going to hand your personal info to governments when compelled to take action and in some circumstances, merely when requested. Last year, the Supreme Court dominated that the federal government normally wants a warrant to entry personal information held by third-party firms. But even with new authorized safety, e-mail stays all too simple for governments to quietly receive. Many firms, like Facebook, have shared private info much more broadly, with personal entities. When your private information is saved on a firm’s servers, as with the e-mail in your Gmail account, there aren’t any technical limitations to the host firm sharing it when it sees match.
Google supplied personal info to authorities businesses world wide greater than 60,000 instances in 2017, usually turning over information from a number of Google accounts without delay, in keeping with its transparency report. And that doesn’t embody over 100,000 Google accounts from which the corporate gave information in response to secret orders from the Foreign Intelligence Surveillance Court, a U.S. nationwide safety tribunal whose conferences and selections are stored from the general public. Mail.ru doesn’t present a transparency report, however the state of affairs is little doubt a lot worse in Russia: All Russian web firms are required to retain information they acquire about their customers and at hand it to FSB, a Russian spy company, if requested.
Google gave information from over 100,000 accounts in response to secret nationwide safety orders — in a single 12 months.
If you need an e-mail account that’s really personal, one answer is to run your personal e-mail server from your home. This approach, if governments wish to secretly ask your e-mail supplier for a copy of your inbox, they’ll should ask you.
Until now, this hasn’t been a viable choice for most individuals: Not solely would you want an additional pc to behave as a house e-mail server, however you’d additionally want sufficient system administration expertise to put in, configure, and safe this server. In addition, you’d have to take care of complications associated to your broadband web supplier; such suppliers sometimes attempt to block e-mail servers by interfering with connections to a specific networking channel, port 25, related to mail supply. After you solved that drawback, you’d have to configure your router to ahead inbound e-mail deliveries to your server. Then you’d have to register a area identify the place your e-mail tackle will reside, after which level that area to your e-mail server utilizing a system generally known as DNS. This is difficult by the truth that most residential web addresses change on a common foundation. And as a lot work as it’s to initially arrange this house e-mail server, it’s much more work to keep up it over time — to promptly set up safety updates, arrange monitoring so that you’ll be notified when one thing breaks, block spam, and keep away from getting your server added to spam block lists.
With the discharge of Helm, that has modified. Helm is a triangle-shaped private server that may host e-mail (by yourself customized area identify), contacts, calendar, and a file server, and is about as simple to arrange as a new smartphone. For being principally a subtle product for internet hosting your most personal information — the place there are a lot of alternatives to screw up — Helm’s technical decisions and enterprise mannequin are surprisingly well-thought-out. All you want is web entry at your property and an iPhone or Android telephone to configure it.
The greatest hurdle potential customers will face, I believe, is the value: You should drop $500 to purchase Helm to get began, after which pay a $100 per 12 months subscription to proceed utilizing its cloud gateway and encrypted backup elements.
I’ve been internet hosting my private e-mail, [email protected], on a Helm machine plugged into my router in my front room for a number of months now. Here are a few of the issues I’ve realized, beginning with what it’s like to modify to Helm, then an evaluation of Helm safety, a comparability to Gmail, a nitty-gritty examination of how Helm works technically, a look to the way forward for Helm, and a few essential caveats in regards to the product and the insurance policies and realities round it.
Photo: Micah Lee/The Intercept
Switching to Helm
The first step to switching to Helm is selecting out the area identify you wish to use on your new private e-mail tackle — in my case, micahflee.com. After ordering my Helm, I acquired easy directions on the way to proceed.
Properly configuring a area identify for an e-mail server is difficult, and misconfigurations may cause different e-mail servers to suspect that you simply’re operating a spam operation. To keep away from this, and to make it less complicated for customers, Helm handles the DNS on your area identify for you. If you ever want replace your area identify’s DNS data, you are able to do it from the Helm cellular app.
If you don’t already personal a area identify, you will get one whereas shopping for your Helm; all of the charges related to shopping for and renewing the area identify are included within the value. If you do already personal a area, you’ll have to log in to your registrar’s web site and replace your area to level to DNS servers that Helm controls; Helm will deal with the remaining. If you host a web site in your area identify — like I do with micahflee.com — you’ll additionally have to let Helm find out about it first. (Helm helps a number of domains, however this characteristic was added after I attempted the product.)
The subsequent step is ready for the Helm machine to ship to your home. Once mine arrived, I had it up and operating in about 10 minutes, with an extra hour and a half emigrate all of my e-mail from my outdated supplier into my Helm.
Following the directions, I plugged the Helm machine into a energy outlet in my front room, subsequent to my Wi-Fi router. I linked the Helm to the router utilizing the ethernet cable (you too can join your Helm to your router over Wi-Fi, however ethernet is extra dependable, quicker, and safer). And I put in the Helm mobile app on my Android telephone, turned on Bluetooth, and paired with the Helm.
A fast observe in regards to the Android app: When I first opened the Helm app, it requested for permission to make use of my location. “This is an unlucky requirement from Android since our app makes use of Bluetooth to pair with the Helm,” Helm CEO Giri Sreenivas informed me. Apparently, Android apps can’t have Bluetooth permission with out additionally requesting location companies permission. “We don’t observe or retailer any location info.” The iOS app doesn’t have this difficulty.

Screenshot from Helm’s Android app after pairing over Bluetooth with my Helm machine.
Screenshot: The Intercept
The subsequent web page asks on your activation code, which I already had in an e-mail from Helm. After typing it in, the Helm app walked me by way of creating an administrator username and password for my area, micahflee.com.

Setting up the administrator account.
Screenshot: The Intercept
After creating an account, the app prompts you to insert the “restoration key” into the Helm machine. This is a part of Helm’s technique to be sure you can entry your information in case of catastrophe — like when you spill soda throughout your Helm or your home burns down. If you ever want to revive your encrypted backups to a new Helm machine, you’ll both want your logged-in telephone or this restoration key. And when you get a new telephone, you’ll want this restoration key to log in to the Helm app as your administrator consumer once more.

Saving the restoration key.
Screenshot: The Intercept

Saving the restoration key.
Photo: Micah Lee/The Intercept
After getting your restoration key squared away, put it in a protected location the place you gained’t lose it. I counsel a protected, when you’ve got one, or a locked drawer.
The subsequent step is to configure e-mail in your units, like your telephone and laptop computer. Each machine will get its personal distinctive, unguessable password to login to your e-mail. Unlike many e-mail companies, Helm doesn’t help internet mail — you should use a customary e-mail shopper, just like the one constructed into your telephone or laptop computer’s working system, or like Mozilla Thunderbird.
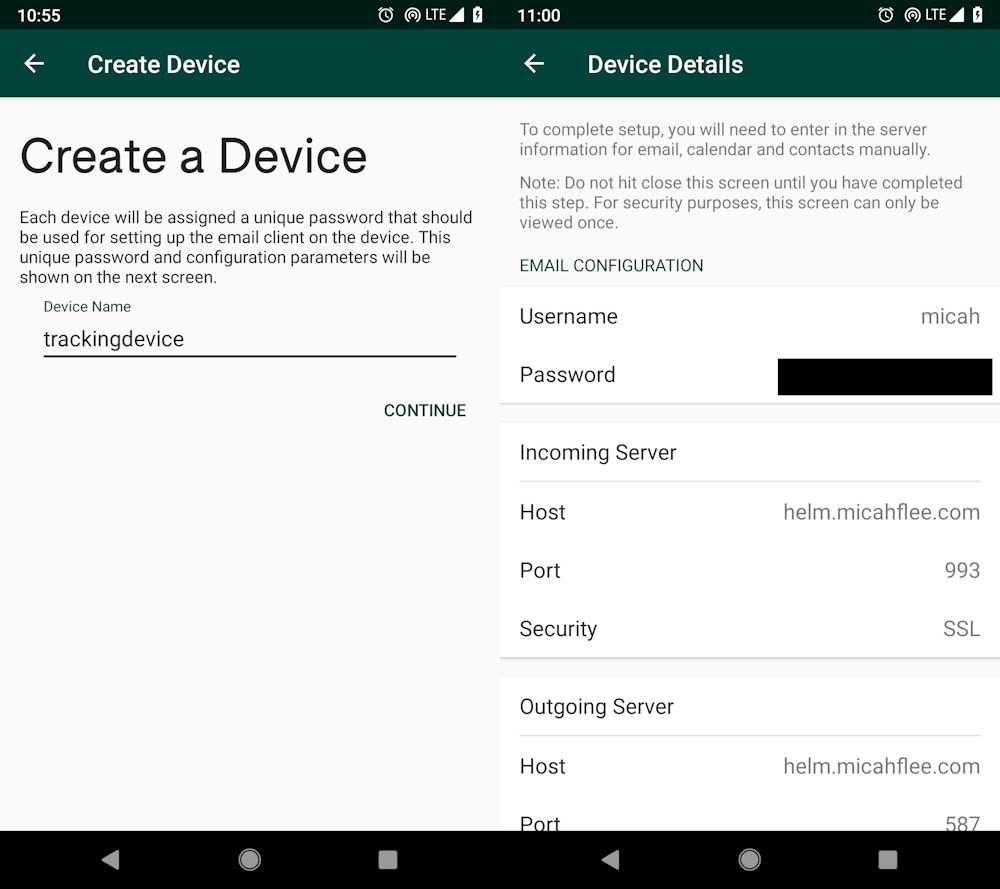
Adding a new machine to my Helm account.
Screenshot: The Intercept
After I arrange Thunderbird to hook up with my new house e-mail server, I used to be offered with an empty inbox. About one minute later, I acquired my first e-mail to my house e-mail server. As quickly as I activated my Helm machine, incoming e-mail for micahflee.com stopped getting delivered to my outdated supplier and began getting delivered to my Helm.
The subsequent step is importing your outdated e-mail. Before going into how I did that, right here is a fast apart: I used Gmail a decade in the past. But as a privateness advocate, I used to be keenly conscious that Google had entry to all my e-mail and couldn’t be relied on to guard it from authorities requests. This anxiousness was heightened in 2013, across the time that National Security Agency contractor Edward Snowden blew the whistle on the NSA’s overreach, revealing, amongst different issues, that the company had “direct access” to the servers of main U.S. firms, together with Google, by way of a mass surveillance program generally known as PRISM.
So I went trying to find an e-mail supplier I felt I may belief extra. Since then, I’ve hosted my e-mail with a handful of small entities that, whereas missing Google’s large engineering, safety, and usefulness assets, I judged had been more likely to guard my e-mail from authorities requests primarily based on their privateness insurance policies and, in some circumstances, conversations with workers at these suppliers. These included Riseup, a tech collective that hosts communication instruments for activists; Electric Embers, a tiny Bay Area work-owned cooperative; ProtonMail, a Swiss-based encrypted e-mail supplier; and Soverin, a tiny privacy-focused e-mail supplier primarily based out of Amsterdam. (Unlike most e-mail suppliers, Riseup and ProtonMail retailer your e-mail encrypted to your password, however there’s nonetheless a lot of data they might present to a authorities if compelled, together with all of your e-mail metadata.)
Back within the Helm app, I began the method of importing my e-mail from Soverin. I selected to import from Soverin’s IMAP server, so I needed to provide an IMAP hostname, in addition to my Soverin username and password. The course of is even less complicated when you’re switching from Gmail or Yahoo Mail.
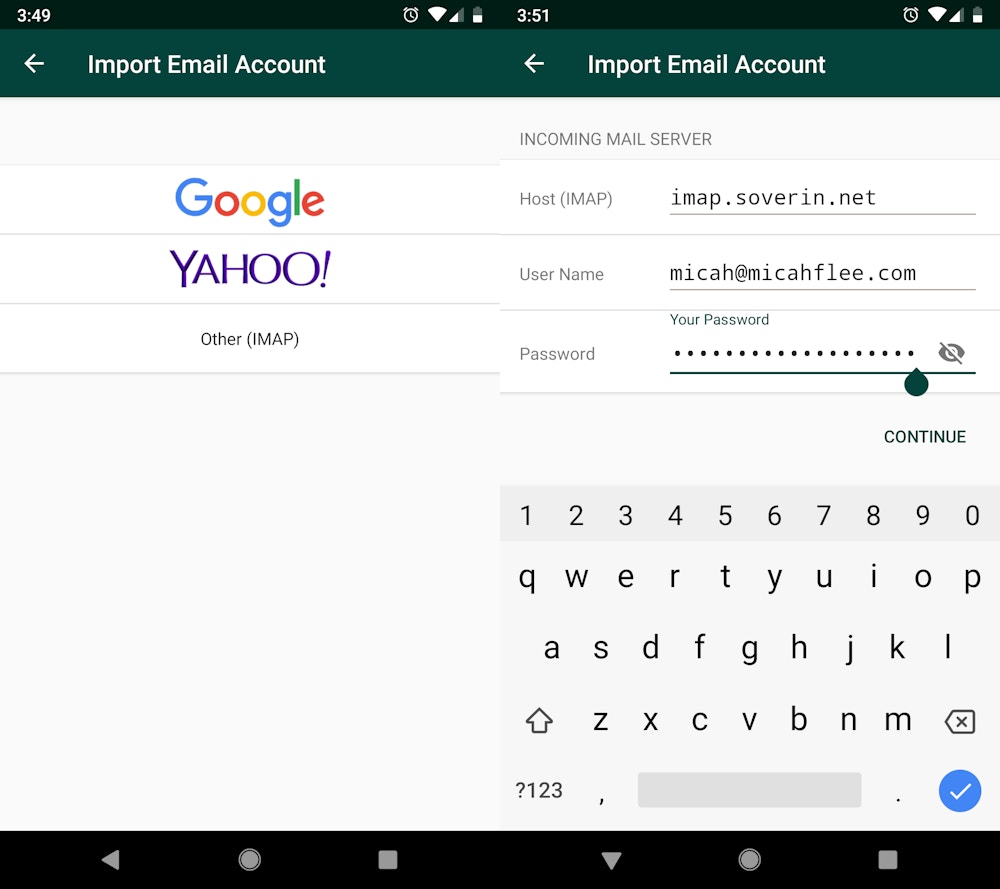
Importing e-mail from my outdated supplier to my Helm.
Screenshot: The Intercept
It took about an hour and a half to obtain the entire emails from my outdated supplier. When it was finished, I logged into my Soverin account and deleted all of my e-mail from its server. At this level, I used to be efficiently self-hosting my e-mail from my home! (If you’re altering e-mail addresses whereas switching to Helm, like when you’re switching from a gmail.com tackle to a customized area identify, you’ll additionally wish to configure your outdated e-mail account to ahead emails to your new tackle and arrange an auto-responder message that tells individuals who e-mail you that you simply’re utilizing a new e-mail tackle.)
Importing e-mail out of your outdated supplier into Helm is straightforward and easy. But contacts and calendar, alternatively, are fairly a bit extra difficult (after a lot troubleshooting, I ended up including each my new and outdated contacts and calendar accounts to Evolution, a Linux-only e-mail app, then exported information from my outdated accounts and imported it into my new accounts). I’d like to see future variations of Helm make migrating your contacts and calendar simply so simple as it’s emigrate your e-mail.
How Secure Is Helm Against Hackers?
When you speak in regards to the safety of an e-mail server, you’re actually speaking about two separate issues: The safety of particular person consumer accounts and the safety of the technical infrastructure itself, which incorporates server software program decisions, system hardening, monitoring, intrusion detection, incident response, and the operational and endpoint safety of system directors.
I imagine that Helm’s technical infrastructure is well-engineered from a safety potential. It makes use of greatest practices (I am going into larger element within the “below the hood” part under), I don’t see any apparent flaws, and, although I haven’t made a thorough comparability, it seems to supply related safety as most small, well-run e-mail suppliers. Basically, the one attackers who can get in are these armed with costly zero-day exploits — exploits that depend on bugs that the software-makers themselves don’t even know exist and thus haven’t been in a position to launch safety updates for. An attacker would want to seek out a zero day for software program Helm is thought to run, like Dovecot, the open-source e-mail server. The overwhelming majority of attackers will stay locked out.
That mentioned, there are some safety tradeoffs concerned with utilizing Helm and a few areas by which the system’s safety might be improved.
If somebody does handle to hack your Helm, you in all probability gained’t discover, sadly. Sreenivas informed me that Helm doesn’t have an intrusion detection system at the moment. “We plan to summarize failed makes an attempt in a weekly digest e-mail,” he informed me, “however alerting on precise intrusion is one thing we haven’t outlined but.”
Additionally, operating a house server will increase the chance to your property community. If somebody efficiently hacks your Helm, they might pivot from it, probing laptops, smartphones, and different units in your home for weaknesses. But I don’t suppose that is a lot riskier than connecting your laptop computer or smartphone to a public Wi-Fi community, the place anybody else on the community may attempt attacking your machine.
Individual Helm e-mail accounts are safer than particular person Gmail accounts.
Also, whereas Helm’s infrastructure is fairly good, you’ll get extra sturdy safety protections from a main enterprise like Google, which has a team devoted to looking, and fixing, zero-day exploits and warns you when state-sponsored hackers attempt to compromise your account.
Unlike Google, nevertheless, Helm won’t ever share your emails with anybody or scan them to focus on ads at you, as a result of it can’t. By design, the Helm firm merely doesn’t have entry to your e-mail. So whereas Helm might be not as safe as Gmail, it’s vastly extra personal.
What’s extra, particular person Helm e-mail accounts are safer than particular person Gmail accounts, I’d argue. Unlike with Google, and most different web-based companies, hackers can’t use spearphishing to compromise your Helm account. It’s potential to lock down your Google account to defend towards spearphishing, however accounts aren’t locked down by default, and including safety measures like 2-Step Verification, which I like to recommend each Google consumer allow, make it extra annoying to make use of on a each day foundation.
Before I am going into how Helm account safety works, first let me describe how spearphishing works. One of essentially the most consequential e-mail hacks in current historical past occurred towards a Gmail account in March 2016. Officers working for GRU, Russia’s army intelligence company, despatched the next e-mail to Hillary Clinton’s 2016 presidential marketing campaign chair John Podesta.

A reconstruction of the spearphishing e-mail that GRU officer used to compromise John Podesta’s Gmail account.
Image: Courtesy of Matt Tait
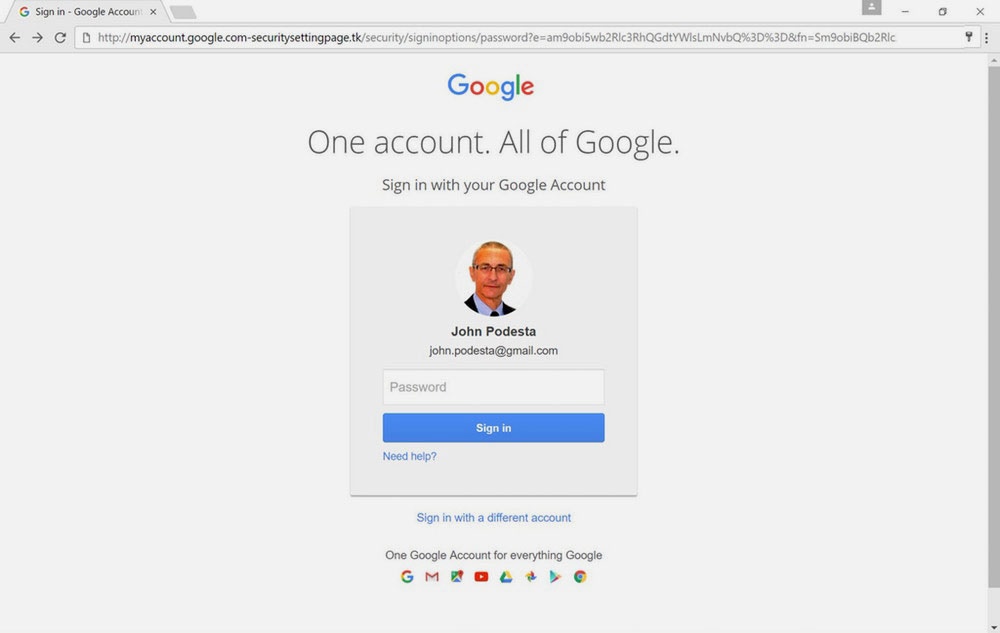
A reconstruction of what the spearphishing web site that was used to steal Podesta’s Gmail password looked like.
Image: Courtesy of Matt Tait
In distinction, right here’s how Helm safety works. Managing your Helm account and units is finished completely by way of the cellular app and initially requires what the corporate calls “proximity-based” authentication: To affiliate your smartphone with the Helm, you want your username and password, and also you additionally have to bodily be in the identical room because the Helm so you’ll be able to pair with it over Bluetooth, which can create a shared authentication token between the Helm and the smartphone. So even when you use a weak password, or reuse the identical password for Helm that has appeared in a information breach, attackers can’t log in to your account with out getting bodily shut sufficient to your Helm to pair with it. Once you log in to the app, you keep logged in and customarily gained’t have to log in once more except you get a new telephone. This means you don’t want to be in the identical room because the Helm merely to entry your e-mail, calendar, or different companies.
(Proximity-based authentication has its downsides: If you wish to give a pal who lives in one other a part of the world a consumer account hosted in your Helm, they’ll want to come back go to you in individual to login to their account for the primary time, and once more each time they swap telephones.)
After logging into your account, you’ll be able to add and delete units that you simply’ll use to entry your e-mail. Each of those units has a safe, distinctive machine password corresponding to “3mdxmh23kzjkv6hs.” For instance, the password I take advantage of on my telephone is completely different than the one I take advantage of on my laptop computer. If I get a new telephone, I’ll delete the machine identify related to it (“trackingdevice”), revoking entry from my outdated telephone, and I’ll add a machine for my new telephone, which can have its personal distinctive identify and password.
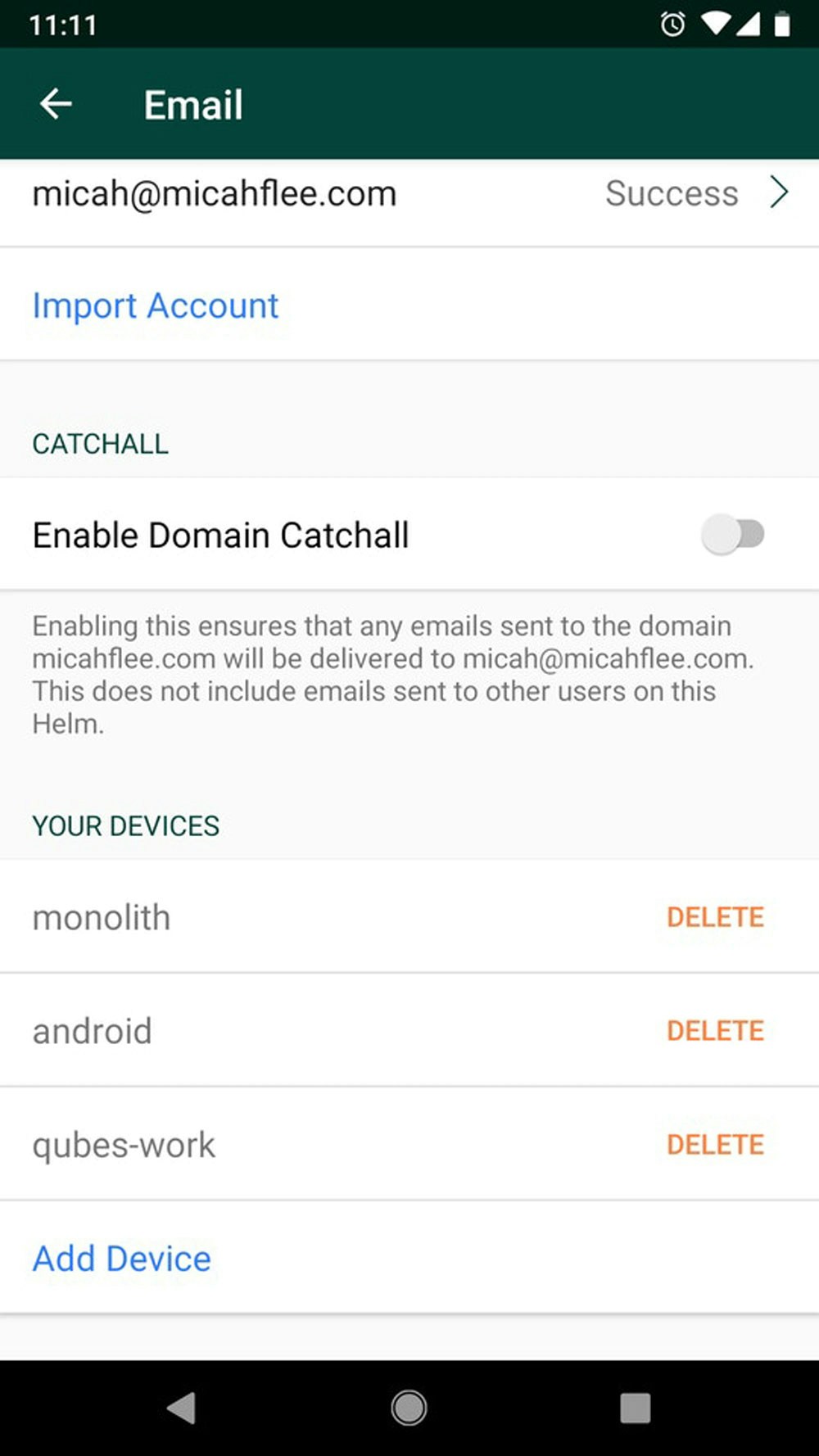
Managing my e-mail account within the Helm cellular app.
Screenshot: The Intercept
All of this collectively implies that Helm is immune from spearphishing. If GRU hackers went after a Helm consumer with the identical approach they used towards Podesta, it wouldn’t work. They may ship a spearphishing e-mail, maybe disguised as official communication from the Helm firm, with a hyperlink they trick the consumer into clicking. But there’s no login web page on Helm’s web site for them to mimic — you host your e-mail from the Helm machine in your home, not from Helm’s web site, in spite of everything. And that machine additionally lacks a login web page. If an attacker made up a login web page anyway, and even when the Helm consumer typed their username and password into it (regardless that Helm customers by no means do that, in contrast to with Google the place customers log in on a regular basis), the Helm account remains to be protected by proximity-based authentication.
If resourced hackers, like GRU officers, actually wished entry to your e-mail, their greatest wager is to both compromise the Helm machine itself, or compromise considered one of your units that you simply’ve approved to examine your e-mail. This is certainly potential, nevertheless it’s a a lot increased bar than compromising a single account, particularly when you maintain your units up to date (you don’t want to fret in regards to the Helm machine, which mechanically updates itself).
Your User Experience Could Change
If you’re accustomed to Gmail, switching to Helm may take some getting used to. Here are a few variations to count on.
Helm doesn’t have any internet mail interface. This is undoubtedly a good factor for safety — it protects you from spearphishing assaults, it lets you strictly management which units have entry to your e-mail, and it makes it less complicated to encrypt your e-mail with PGP, when you’re that kind of nerd. It additionally implies that you’ll have to make use of an e-mail shopper with a consumer interface completely completely different from Gmail’s; Thunderbird isn’t as fairly or simple to make use of, for instance. And lastly, you’ll be able to’t examine your e-mail on another person’s pc — you’ll be able to solely log in on units that you simply’ve added to your Helm account utilizing the cellular app. This may be inconvenient, nevertheless it, too, is sweet on your e-mail safety. You don’t know what adware is operating on different folks’s computer systems, and also you don’t have to fret about forgetting to log off.
If GRU hackers went after a Helm consumer with the identical approach they used towards Podesta, it wouldn’t work.
I get a lot of e-mail, together with all types of e-mail notifications, and I’m subscribed to a number of mailing lists. To maintain issues organized, I mechanically filter incoming emails into their very own folders. At the second, Helm doesn’t help server-side filters, so if you wish to filter your e-mail, it’s worthwhile to do it from considered one of your e-mail shoppers. For instance, as a software program developer, I get a lot of GitHub e-mail notifications that I need filtered into my “github” folder, so I arrange an e-mail filter in Thunderbird that does this, and it really works nice. But as a result of it’s a Thunderbird filter, after I examine my e-mail on my telephone, new GitHub emails seem in my inbox and don’t get moved to my “github” folder till the following time I open Thunderbird. It’s not a massive deal, however it could be good for Helm to help server-side filters sooner or later.
Finally, there may be the battle towards spam. Gmail is great at recognizing and blocking spam as a result of they use the personal emails of their 1.5 billion users to create an extremely correct mannequin of what spam seems like. Helm’s spam filtering isn’t dangerous, however chances are high extra spam will get by way of than you’re used to, a minimum of to start with. Every time you mark e-mail as spam in your e-mail shopper, Helm’s spam filtering will be taught from this and get higher at recognizing it, all whereas not sharing the contents of your e-mail with any third events.
How Helm Works Under the Hood
Helm contains completely different elements: the cellular app, the restoration key, the gateway server within the cloud, and, most significantly, the Helm machine itself, which shops your entire information on its 128GB solid-state exhausting disk. Since I’m trusting Helm with internet hosting my very own e-mail, I put effort into studying precisely the way it works. This part dives fairly deep into the weeds and makes use of tech jargon with out all the time explaining what it means. Feel free to skip forward if this isn’t your factor.
The Helm Device
The Helm machine is a pc operating Linux, the favored open-source working system. It doesn’t have a microphone, and it’s utterly silent; as a substitute of cooling with a loud fan, it dissipates warmth by way of its aluminum base. And in comparison with a typical house Linux server, it’s fairly a bit more durable to hack because of {hardware} and software program hardening tips.
First, Helm makes use of a system referred to as full-disk encryption to guard information saved on its native drive, making certain that individuals with bodily entry to the machine, like a burglar, can’t extract any personal info from it, since every thing on the drive could be indecipherable to the attacker. As with iPhone {hardware}, Helm has a “Secure Enclave” constructed into its processor — principally, a tiny, separate pc designed to be impenetrable and that manages encryption keys, tightly limiting in what circumstances, and by what software program, the keys could also be used to unlock saved information. And safe boot is enabled, that means that an attacker can’t create malware to intercept encryption keys by impersonating the working system as Helm begins up (a tactic categorized as a kind of “evil maid“ attack). (If you need to run unauthorized bootloader code by yourself Helm, try the reverse engineering part under.)
Once the Helm machine is booted, the following safety trick is that it shops information used besides the system on what is named a read-only root filesystem, the place information can’t be modified. If your Helm will get compromised, this makes it harder for malware to switch any core working system information or to outlive a reboot. The server can also be filled with confirmed open-source software program for operating e-mail, contacts, calendar, file internet hosting, and consumer administration companies — these embody Postfix, Dovecot, OpenDMARK, Apple’s Darwin Calendar and Contact Server, Nextcloud, OpenLDAP, and extra — and every service is remoted in its personal Docker container (a kind of digital jail enforced by software program). In one other safety win, Helm mechanically retains this big selection of software program up to date to be able to eradicate vulnerabilities as they’re found.
Finally, whenever you configure your Helm for the primary time, it mechanically permits a kind of encryption generally known as TLS. TLS is commonly used to encrypt internet site visitors, however additionally it is used to permit e-mail shoppers to attach securely and privately over the web to your e-mail server, which in my case, has the hostname of helm.micahflee.com. Helm will get a trusted TLS certificates utilizing a fashionable nonprofit service generally known as Let’s Encrypt.
But, wait, how do connections to your hostname find yourself making it to your Helm machine in your front room?
Gateway within the Cloud
Each Helm machine makes a persistent, encrypted community connection to a devoted gateway server hosted on Amazon’s platform for making low-cost, digital web servers, generally known as Elastic Compute Cloud, or EC2. Unlike most residential web connections, that are periodically assigned new IP addresses, EC2 offers gateways with static IP addresses and not one of the complications — blocked mail supply ports, router reconfiguration — that make it exhausting to host an e-mail server at house. Your Helm server, linked to your property community, connects to the gateway utilizing the identical expertise you may use to entry your employer’s workplace community from house: a digital personal community, or VPN. The gateway’s goal is to ahead encrypted site visitors, together with e-mail supply connections, by way of the VPN tunnel to the Helm machine in your home. This structure explains why, when you search for the IP tackle of my public e-mail server, helm.micahflee.com, it resolves to the placement of my gateway in an Amazon information middle, not of my house.
For instance, I configured the e-mail app on my telephone to hook up with helm.micahflee.com, encrypted with TLS. Each time my e-mail app checks for brand new messages, it connects over the web to the gateway, which then forwards this encrypted site visitors over the VPN tunnel to the Helm machine in my home. In different phrases, the connection between my telephone and my Helm machine is end-to-end encrypted. Similarly, when there’s an incoming e-mail, the connection between the distant e-mail server and the Helm machine can also be end-to-end encrypted, however forwarded over the gateway.
So, whereas each Amazon and Helm (the corporate) have the technical skill to spy on this server, this spying can’t reveal my emails or my e-mail metadata — all they will see is encrypted site visitors. The exception to that is if I’m emailing with somebody utilizing a grossly insecure e-mail server that doesn’t help TLS encryption. In this case, Amazon and Helm, and each router that forwards emails to and from that server throughout the web, can spy on them. “Over 92% of e-mail site visitors is over TLS globally,” Sreenivas wrote in a weblog submit explaining how Helm’s networking works, “and we can have an choice for Helm prospects to require all e-mail be transmitted over TLS with the consequence that insecure transmission of emails will probably be rejected.”
Encrypted Backups and Recovering From Disaster
As mentioned beforehand, Helm protects all its information utilizing full-disk encryption with a key saved within the Secure Enclave. In addition, it encrypts all personal information, together with emails, contacts, calendar occasions, and information, a second time utilizing a separate key referred to as the “restoration key.” When you authenticate as a Helm administrator utilizing the cellular app, a copy of this restoration key will get copied to your telephone. (Once in your telephone, to offer extra safety, it’s saved in a personal space that isn’t included in telephone backups.) And through the Helm setup course of, you additionally copy this key onto the bodily key-shaped USB machine (this USB machine is designed solely to retailer the restoration key; it doesn’t work like a regular USB drive). Having a number of backups of the restoration key, in your telephone and on the key-shaped USB machine, forestall a “single level of failure,” Sreenivas informed me. Also, you’ll want to make use of the USB restoration key whenever you login because the administrator consumer on the cellular app — for instance, the following time you get a new telephone.
Both Amazon and Helm have the flexibility to spy in your gateway — however all they will see is encrypted site visitors.
On the Helm machine, the personal information is saved in its personal filesystem, encrypted utilizing dm-crypt, an encryption system supplied by Linux. The Helm then makes use of an open-source system generally known as duplicity to often add incremental, encrypted backups to Helm’s servers. (This backup service, along with DNS internet hosting and your Helm’s gateway server, are what the $100 per 12 months subscription goes towards.) While the Helm firm has entry to your backups, they don’t have entry to the restoration key wanted to entry any of the info locked inside. Only you do, in your Helm machine, your telephone, and your key-shaped USB machine.
If your Helm breaks, is stolen, or is in any other case destroyed in a catastrophe, you will get a new Helm machine and restore the backup. But to do that, you’ll want both your telephone (logged in because the administrator consumer) or your key-shaped USB machine. If you don’t have both of those, you’re out of luck, and there’s nothing the Helm firm can do that can assist you. Such is the value of utilizing encryption and having management over your personal keys.
The Mobile App
The remaining part is the cellular app, obtainable for Android and iOS. As mentioned above, that is the only interface for configuring your Helm. Every consumer who has an account on the Helm makes use of the cellular app to log in utilizing their username and password, in addition to Bluetooth pairing for proximity-based authentication. Once logged in, customers can add new units, which create distinctive machine passwords, in addition to delete units to revoke entry. As an administrator, you too can use the cellular app to handle the DNS in your area identify and add new accounts.
Email Is Only the Beginning
One of the issues I’m most enthusiastic about as a Helm consumer is that, over time, Helm plans so as to add new companies to their plug-and-play house server past e-mail, contacts, calendar, and information.
In reality, help for a house file server that lets you sync information between your units, share information with different customers, and privately again up pictures out of your telephone — powered by the open-source Nextcloud venture — is a new characteristic I haven’t totally explored but.
“We are engaged on a VPN service that runs off your Helm, which we plan to attach with an ad-blocker,” Sreenivas informed me. This would permit you to securely join into your property community from anyplace, making it safer to make use of public Wi-Fi networks and permitting you to entry companies like Netflix, which usually block VPNs.
Helm additionally plans on constructing a password supervisor that syncs your password database to the machine, in addition to a personal “household chat and messaging” service. New companies will seem in updates and gained’t price something additional, Sreenivas mentioned. Instead they are going to all be coated within the $100 per 12 months subscription payment.
How Helm Restricts Your Use of Your Server
While Helm is powered by open-source software program, and the corporate has proven a dedication to transparency in regards to the internal workings of its product, it’s essential to do not forget that Helm is an investor-funded startup, and the Helm product is proprietary. Unlike a house Linux server, you’ll be able to’t log in to it with software program like SSH, set up software program packages (like, say, a internet server), or tweak configuration information. You can’t examine its supply code or set up Helm’s customized working system on a pc of your selection, like you would with an open-source working system corresponding to Ubuntu. With this in thoughts, right here’s what I realized from reviewing the legalese I needed to comply with to turn out to be a Helm consumer.
The very first thing that stood out within the privateness coverage is that, like Google, Mail.ru, and all different firms in every single place on the earth, Helm should adjust to lawful authorities requests for information. “We might disclose your info if required to take action by legislation, in response to a court docket order, judicial or different authorities subpoena or warrant,” the privateness coverage reads.
So if Helm acquired a information request, what info would they hand over? Sreenivas mentioned the corporate will return buyer info, together with the shopper’s identify, billing tackle, delivery tackle, e-mail tackle, area identify, and their DNS data; machine info, together with the serial quantity, software program model, which companies are enabled, and a few diagnostic info just like the working temperature of the shopper’s Helm machine; and any emails or chats with buyer help. They won’t, nevertheless, be capable of return any information that’s saved on the Helm, corresponding to your personal e-mail, contact listing, calendar occasions, or information. Sreenivas additionally informed me that Helm will publish a transparency report about what number of information requests the corporate receives and can alert its prospects if it receives a request for consumer information, as long as the corporate isn’t prohibited from doing so with a gag order.
Next, Helm can’t assure your safety. “Please remember that no safety measures are excellent or impenetrable,” the privateness coverage states. “We can’t and don’t assure that your info won’t be accessed, considered, disclosed, altered, or destroyed by breach of any of our bodily, technical, or managerial safeguards.” This is true of Gmail too — simply ask John Podesta. This can also be true of every thing else that depends on pc safety. Perfect pc safety is a fable, and firms that declare their merchandise are “hacker-proof” are mendacity to you.
But the factor that stood out to me in Helm’s phrases and situations as most worrisome is that this passage, forbidding customers to reverse engineer their Helm units: “Buyer acknowledges that the Product bought by Seller hereunder incorporates and embodies commerce secrets and techniques belonging to Seller and Buyer shall not reverse engineer any merchandise bought hereunder.”
This is a ban on reverse engineering, stopping a kind of shut examination of pc {hardware} and code that may assist uncover defects and add new performance. Such bans are deeply problematic. Sreenivas outlined some plans to mitigate the ban, however in the meanwhile, these are merely guarantees.
Reverse engineering bans like Helm’s have traditionally been abused by firms.
Reverse engineering bans have traditionally been abused by firms desirous to prevent safety researchers from publicizing safety flaws of their merchandise. “We wish to encourage safety researchers to have interaction with us, so they are going to be granted an exception,” Sreenivas informed me. In addition, Helm presents a bug bounty program by which safety researchers can report vulnerabilities they uncover and obtain a bounty of as much as $20,000.
The different approach bans on reverse engineering have been abused is by going after “jailbreak” communities. You spent $500 in your Helm machine, so what if you wish to hack it your self to run customized software program? Sreenivas mentioned that the corporate plans to make it simple for customers to do that by together with “successfully an unlock for a developer mode.” This looks like a cheap compromise to me and is just like how developer mode in Google’s Chromebooks works, permitting customers who need full management over their Helms to have it, however on the expense of safety.
Even Though Helm Can’t Access Your Data, You Still Need to Trust It
If it had been malicious, there are a few ways in which the Helm firm itself may launch an assault towards your Helm machine. Helm controls the DNS of your customized area identify and your gateway server, which implies, if it had been so inclined, it has the ability it must conduct a man-in-the-middle assault towards your e-mail service, by which the corporate would spy on your entire e-mail site visitors by impersonating your Helm. The firm additionally controls the updates that your Helm machine receives, so it’s inside its energy to slide into one of many updates a backdoor — a strategy to surreptitiously log into your Helm machine whereas it’s operating, entry your information, and set up different software program.
However, I don’t discover this very more likely to happen. Not solely would it not be towards Helm’s personal pursuits — the corporate’s total enterprise mannequin is predicated round designing a product by which it doesn’t have entry to your emails — an assault like this may finally knock your e-mail privateness right down to the extent of Gmail and Mail.ru, which already has all of this entry. They wouldn’t be capable of learn any emails encrypted with PGP, for instance. And moreover, Helm is way from the one firm it’s worthwhile to belief to not be malicious. If your area identify registrar had been malicious, they might additionally carry out a related man-in-the-middle assault towards your mail server. And the makers of any software program — from Microsoft Word to “Fortnite” — may slip a backdoor into an replace with out you realizing. So, whereas it’s one thing to think about, I’m not almost as fearful about this risk when in comparison with the threats posed by hackers and legal professionals.
Helm will do a higher job at securing your property e-mail server than any lone particular person may — myself included — with the potential exception of a gifted DevOps engineer who does this work professionally. And by design, Helm protects your information from the rather more severe threats of your e-mail supplier pilfering by way of your inbox, utilizing it to focus on adverts towards you, and sending copies of your e-mail to cops or spies who ask for it with out your data or consent.
Update, May 3: My clarification of proximity-based authentication has been modified to make clear that it’s worthwhile to be bodily close to the Helm to create a consumer account. It is technically potential to present a distant individual an e-mail tackle in your Helm, however you’ll have full entry to their account, which most individuals wouldn’t need.

![Top 6 Server Management Software and Tools Compared [2023]](https://ta-relay-public-files-prod.s3.us-east-2.amazonaws.com/icp/product_images/23db1d70048ad120d46c9ea0e43f22e5.png)



:max_bytes(150000):strip_icc()/registration-3938434_1280-e2aa7e5d57264ae19b69027f14c85c2f.jpg)
