Microsoft recently introduced a new version of Outlook on Windows PCs. It was designed to replace the aging Windows Mail and the classic Outlook, so it introduces a slick new design and significantly tighter cloud integrations while combining your email and calendar into one app. It also introduces new generative AI features, including writing assists and “other advanced AI features.”
However, the app also introduces some serious privacy concerns. Based on research from the German blog heise.de, which we’ve been able to reproduce at XDA, it appears that the new Outlook app is far more tightly integrated with the cloud than a user might expect, opening up the scope of potential Microsoft data collection. This represents a significant privacy issue, so there are a lot of questions Microsoft needs to answer about user expectations.
What you can expect from the new Outlook
Email is still email, right?
The new version of Outlook has been available since early September and introduces a range of new features. The app already includes new Copilot AI features, and Microsoft has stated that it intends for the new version of Outlook to replace the existing Outlook app within two years. The company has also announced a broader list of upcoming features, which will likely be announced in the coming months (particularly around AI capabilities). The new app also has a fresh UI, bringing it more in line with Microsoft’s cloud versions of office apps, as well as tighter integration with other Office services such as Calendar and Word.
The new version of Outlook is available on the Microsoft Store now as Outlook for Windows. Once installed, the app in the start menu as Outlook (new).
The new Outlook has problematic behavior
You may not realize what you’re signing up for
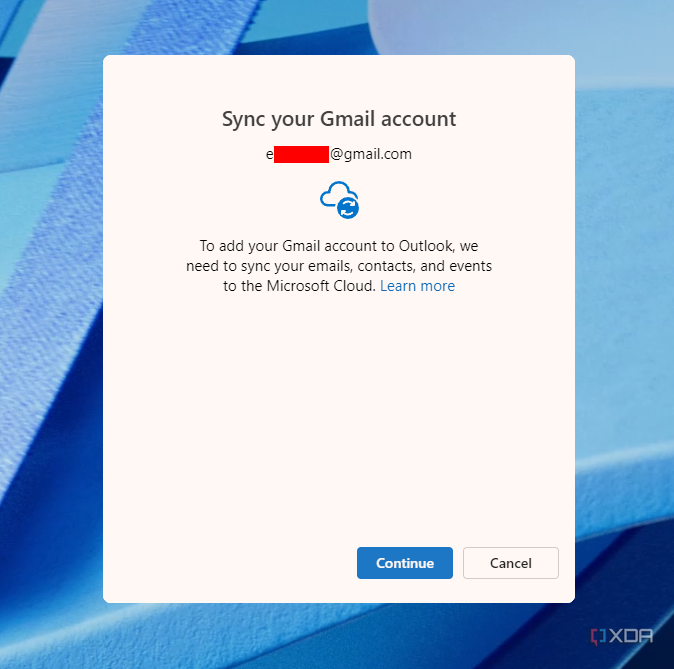
When opening the new Outlook client for the first time, the user is asked to log in much like any other email client. If you enter an email address with a common provider, like Gmail or iCloud, the client will use an Oauth2 workflow to authenticate with your browser. If you enter a third-party domain, you’ll be prompted for an IMAP password (if supported). This is all very normal for an email client.
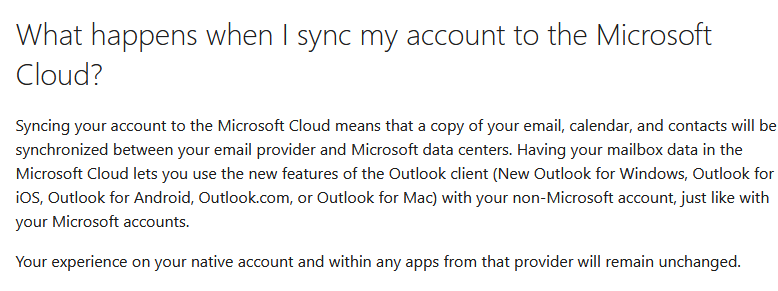
However, once you’re authenticated, you’re presented with an innocuous window informing you that to use the new version of Outlook, Microsoft will need to sync your emails, events, and contacts to Microsoft Cloud. A cancel option is available, but there’s no option to refuse and continue using your client. A support link is provided with some more information, which explains that the access enables features such as mail search, a focused inbox, or recurring meetings, but makes no clear statement of the limits of this data collection.
Source: Microsoft
From this warning, a user might reasonably assume that the email client they’re logging into will continue acting as an email client and that the client might send some limited data for processing in the cloud. However, that’s not the case. Instead of your email client authenticating, your credentials are passed to the Microsoft cloud, which authenticates on your behalf. From this point, all processing (including the fetching of your emails) is handled in the cloud. We could not observe any traffic traveling directly from the client to our email provider.
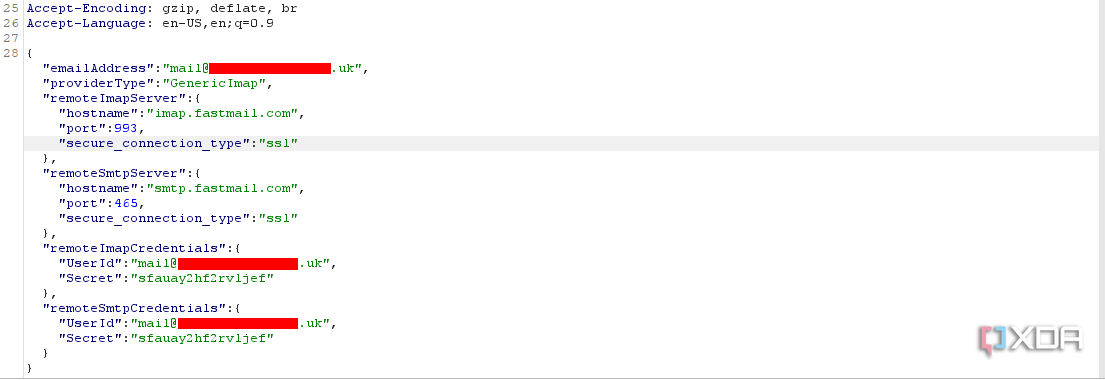
This is true of both OAuth and IMAP workflows but is most visible when authenticating with a third-party IMAP server. In this case, the Outlook client takes the IMAP credentials provided by your email provider to access the application and transfers them directly to Microsoft’s cloud over TLS. We could reproduce this by setting up a transparent man-in-the-middle proxy between the internet and the Outlook Client to intercept encrypted traffic. In the screenshot below, our app password generated from a third-party email provider is shared and stored directly with Microsoft’s servers. The response to this request is an access and refresh token that’s used to maintain a persistent authenticated session with Microsoft’s servers.
Is it an email client or not?
Outlook (new) does less locally than you might think
The email provider we’re using for this example records the IP address and access time of each new login. If the Outlook client was communicating directly with our mail server (i.e. acting like a client should), then the IP address the email provider records should be the same as the computer we’re running Outlook on. In each case we tried this, no connection was recorded from our home IP address. Instead, the initial IMAP/SMTP connections came from a 52.x.x.x IP address. A quick WHOIS lookup shows that this IP address is registered with Microsoft. This would demonstrate that the Outlook “client” is nothing of the sort, acting entirely as a wrapper around Microsoft’s cloud services and that our local client has never actually logged in at all.
The Outlook “client” is nothing of the sort, acting entirely as a wrapper around Microsoft’s cloud services.
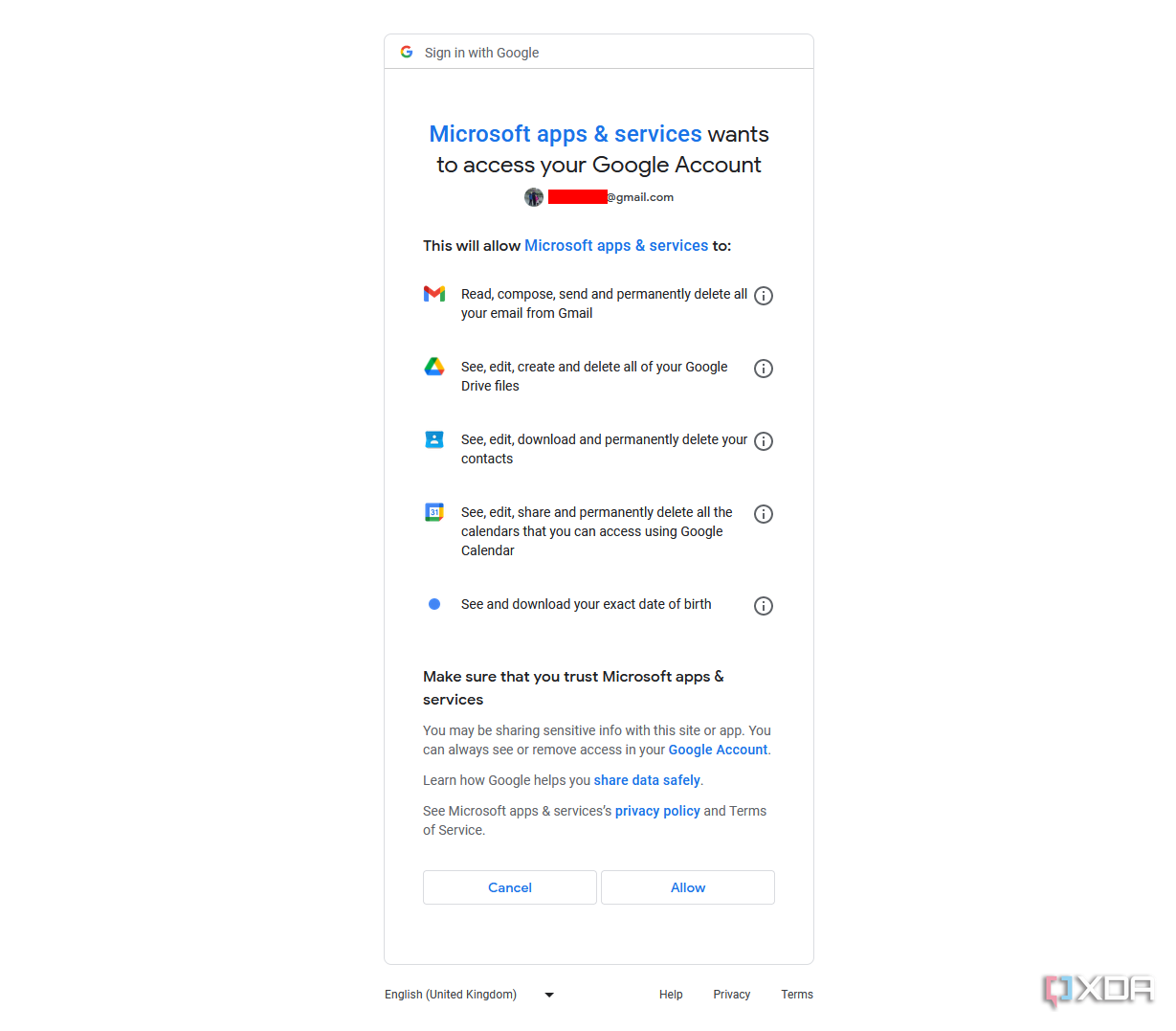
There is a clear problem for the user here. By simply signing in to the new Outlook client, a user has effectively provided the Microsoft Cloud with blanket and unrestricted access to their entire email account. Microsoft’s only mention of privacy on the linked support page is a set of links to its privacy statement and service agreements, both of which allow for blanket access to your data for improving Microsoft products and services. At least when authenticating with OAuth2, most email providers offer some kind of privacy summary (similar to the example from Google below). When authenticating with IMAP, a user is normally given even less warning, with most email providers assuming that email “clients” are at least acting as clients, not gateways to the cloud. It’s also important to note that there’s no obvious way to decline this cloud integration when logging into any email account or use the client in a mode with some AI features disabled.
The offloading of the client functionality of email to the cloud also removes the ability for security engineers or researchers to easily inspect what the client is doing. It’s possible to track the requests made on your data from Microsoft (albeit tricky, as a user would need to run their own email server with access to its logs), but this doesn’t allow for any indication as to how much additional processing, if any, is taking place. It’s also important to remember that this access is ongoing. It’s no longer possible to stop Microsoft’s access to your emails by simply closing Outlook. Users may log in to Outlook on their desktop to test it out, decide they don’t like it, and simply stop using it without signing out. Until the user does sign out (or revokes the session elsewhere), Microsoft will retain ongoing access to their data.
Dangerous precedents for data
Shoehorning data collection into local clients may be a step too far
Data collection is, ultimately, something we’re all accustomed to, whether we like it or not. However, the lack of transparent disclosure here from Microsoft and the piggybacking of desktop apps to get users’ data into the cloud are concerning. Microsoft’s subtly accepted licensing agreements allow almost unlimited data collection for the improvement or creation of new Microsoft tools, including using your email data to train generative AI or other tools.
It’s not made clear at any point that the Outlook desktop app will be acting as a wrapper around exclusively cloud services or what the limits and circumstances are under which Microsoft will access your data in the cloud. Given the scope of Microsoft’s push into new cloud-based AI integrations and the lack of assurance otherwise, it’s reasonable to assume Microsoft may be using this kind of data for training or testing purposes.
The lack of transparent disclosure here from Microsoft and the piggybacking of desktop apps to get users’ data into the cloud are concerning.
This may also be a serious problem for businesses. A corporate end user could unwittingly provide Microsoft access to large volumes of business or commercially sensitive data, possibly in breach of regulatory or security requirements. If this data was then used to train generative AIs or other machine learning models that are publicly released, it’s possible that some aspects of that data could be surfaced for anyone to access. This is an extreme scenario, but it’s clear where concerns might lie.
Whether you’re a power user in business, a systems administrator overseeing a network, or an end user looking for a new email client, it’s important to know the privacy implications of signing in with Outlook. Microsoft, while offering a disclosure that it will sync data to the cloud, is taking far greater liberties than a user would reasonably expect with the extent of their access and the client’s role at all.
https://www.xda-developers.com/privacy-implications-new-microsoft-outlook/