Distributed denial of service (DDoS), like many other cybersecurity buzz words, is a high-level common description of multiple attacks, which hide many variations underneath. Most cyber-attacks are used for data breaching, either to steal or to damage content (data) such as credit card data theft or encryption for ransomware. DDoS, on the other hand, can’t be used for such objectives because it’s a more primitive method of attack. Its main purpose is to slow down or entirely cut out a specific service.
As a common DDoS use case example, imagine two gamers playing an online game using a shared gaming server. While one of the two players is winning, the other sends a UDP flood, multiple UDP packets generated at high volume to a specific destination, towards the gaming server, resulting in a server slow-down or interrupting the ability to play.
DDoS attacks are commonly used against gaming, gambling, government and military public sites, universities, financial institutions and large retail sites. For each situation, the reason for the attack might be different, as an example:
- In gambling or gaming, a DDoS attack can affect the user experience, which could lead to a competitive company to gain new customers.
- With government online services, an enemy country can initiate a DDoS attack for either propaganda reasons or for denying essential services to citizens.
There are several approaches to protecting against DDoS attacks. The most common are on-premises, scrubbing centers and cloud-based. The ultimate goal is to eliminate an attack as near as possible to the originating location, keeping in mind that the side effect of a DDoS attack includes the slowing down of intermediate networks (which carries over to the victim site). However, in most cases it is nearly impossible to deploy DDoS protection near the source given the following:
- An attack can be generated from multiple locations
- Little control of remote networks that may be managed by a random service provider
- Spoofed attacks that are hiding the attack origin
Analyzing the different DDoS protection approaches, it is easy to identify the pros and of each. Therefore, it is recommended to understand both the type of protected service as well as the types of attacks that are expected to be used against that specific service. Below is a short description of the three approaches, including the pros and cons:
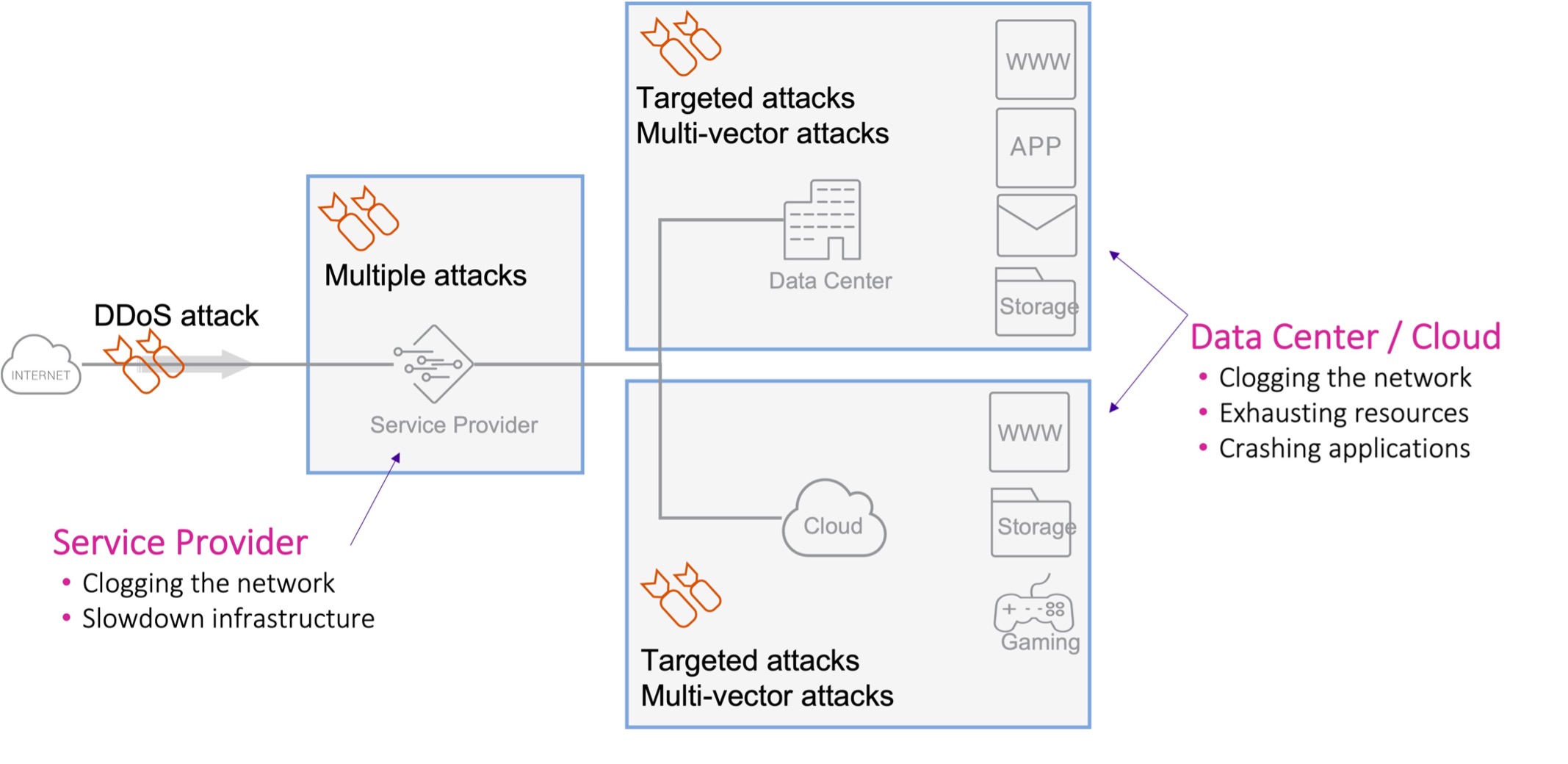
Figure 1: Attack propagation diagram.
DDoS scrubbing centers are a common solution for DDoS protection offered by many service providers for enterprises. This solution excels in mitigating high-volume attacks (volumetric DDoS) and can stop attacks before reaching the customer data center. This results in protection of both the service and the infrastructures. While scrubbing is provided as near as possible to the source, it is based on asymmetric protection, meaning that it can only see the traffic arriving from the client to the service, which limits the traffic visibility and might result in less accurate mitigation filters. This approach is optimal for mitigating network transport DDoS attacks, known as Layer 3 to Layer 4 DDoS attacks such as SYN flood, UDP amplification etc.
An On-premises DDoS protection solution is installed at the last mile, commonly in symmetric mode, meaning it can see both directions of the traffic, which enables additional capabilities such as stateful protection. This allows the DDoS protection solution to mitigate attacks all the way up to the application level, known as Layer 7. In most cases, it is not recommended to use the on-premises approach on its own as major DDoS attacks might overflow the incoming links from the service provider to the data center. Therefore, it is commonly used as a last resort for attacks that managed to bypass the service provider protection.
Cloud DDoS protection service is last. Now, first, note that cloud offerings usually span beyond just a DDoS protection solution. They are often a complete cyber protection and content delivery service, mainly focusing on web services protection and delivery. Most of these solutions are operating as a distributed service based on multiple cloud data centers across the globe, which can become very useful for attack mitigation. Imagine an attack that has been generated from multiple locations, with a cloud service, the attack will be spread across multiple cloud sites. Each will manage a small portion of the attack, which might even not even qualify it as a DDoS attack at all anymore.
It is important to note that in addition to the three approaches above, most service providers are deploying an additional DDoS mitigation solution to protect their own networks from DDoS attacks, as this network is one of the most precious assets they own.
The conclusion here is that for each type of service or for each customer type, a DDoS mitigation solution needs to be adjusted to the specific conditions.
A10 Networks is a leader in DDoS protection solutions, based on its unique DDoS mitigation approach with machine learning, ultra-low latency and mitigation auto-scaling. A10 Thunder® Threat Protection System (TPS) is used by many tier-1 service providers as well as gaming, finance, and government services.
More information on the solutions offered by A10 Networks can be found here.
*** This is a Security Bloggers Network syndicated blog from A10 Networks Blog: Cyber Security authored by A10 Networks. Read the original post at: https://www.a10networks.com/blog/understanding-ddos-containing-ddos/
https://securityboulevard.com/2023/04/understanding-ddos-containing-ddos/