Email threats have risen in recent years, and hundreds of thousands of users have had their computers infected by these attacks. With a lot of malware concentrated on exploiting email functions, it can be easy to become one yourself.
You need the right security system to guard against these email security threats.
What are Email Threats?
According to email threats definition, an “email threat” refers to the use of email as a medium for posing online threats.
Cybercriminals utilize different tactics and activities to jeopardize the security, integrity, and privacy of email communications which are known as email security threats or email-based threats. These threats can take various forms and can cause harm to individuals, organizations, businesses, and governments alike.
Understanding the Frequency and Types of Email Threats
Email threats are common and often difficult to detect. Cybercriminals use email to send malware, phishing scams, and other malicious content.
In Q1 2023, the most prominent form of email threat was credential theft, although it saw a steady decline from late 2022. The steep increase was due to the Microsoft 365 phishing attack, responsible for 41% of such incidents and a significant quarterly rise of 10%, according to Fortra’s data.
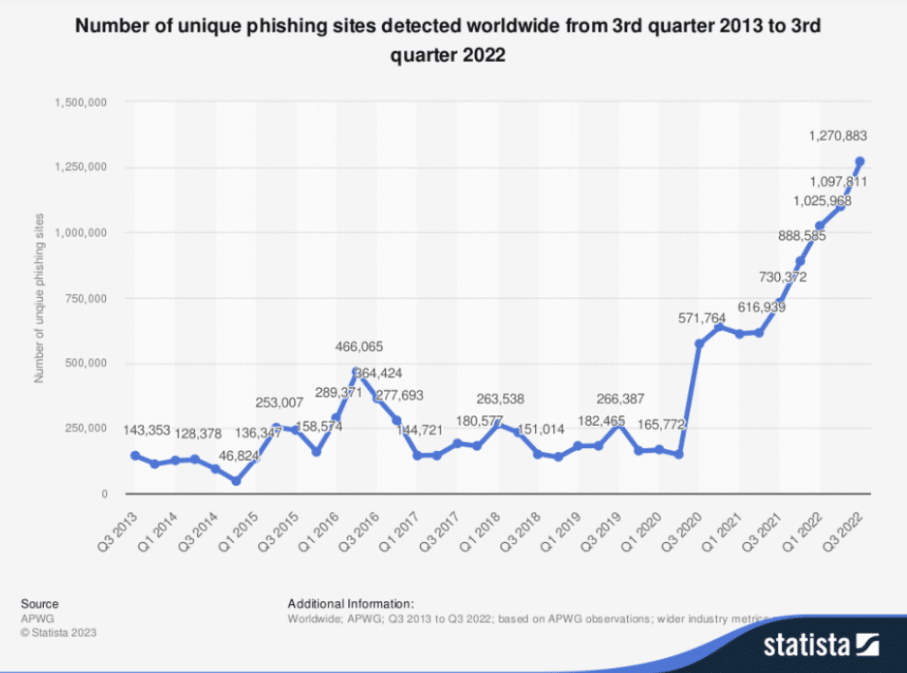
According to data from the Anti-Phishing Working Group (AWPG) posted on Statista, the number of distinct phishing sites discovered globally increased from 1.097 million to 1.270 million between the third quarters of 2021 and 2022.
Email-based threats come in many forms, and they’re constantly evolving. Here are some of the most common types of email threats:
- Spear Phishing: Targeted phishing attacks customized to a specific individual or organization, often leveraging personal information for deception.
- Whaling: Similar to spear phishing, but directed at high-profile individuals like executives or CEOs.
- Business Email Compromise (BEC): Impersonation of high-level executives to manipulate employees into conducting unauthorized transactions.
- Ransomware: Malicious software that encrypts a victim’s files, demanding payment (ransom) for decryption.
- Zero-Day Exploits: Attacks that target software vulnerabilities unknown to the vendor, providing no time for patch development.
- Credential Harvesting: Attempts to steal usernames and passwords, often through fake login pages or social engineering.
- Malware Distribution: Sending malicious attachments or links that lead to malware downloads, like trojans or keyloggers.
- Spoofing: Manipulating email headers or domains to appear as though the email is from a legitimate source.
- Pharming: Redirecting users to malicious websites, even if they enter the correct web address.
- Man-in-the-Middle Attacks (MITM): Intercepting and altering communications between two parties, often to steal information.
Comprehensive Email Security Measures: Safeguarding Your Communication
Email vulnerabilities and threats can be a headache for security teams, but several ways to protect your organization from email-based attacks and malicious content exist.
Here are some of the most effective security measures you can use to keep your organization safe:
Guard Your Authentication with DMARC, SPF, and DKIM
DMARC is an email authentication standard that helps to protect your brand from phishing attacks.
The method uses a TXT record to publish a policy that lets other receivers know how to handle emails from your domain. If an email fails the DMARC check, it’s likely fraudulent and should be flagged as such by the receiver.
SPF (Sender Policy Framework) is another standard for email authentication. It checks if an incoming message comes from a valid sender IP address for that sender’s domain. If not, it’s likely fraudulent and should be flagged by the receiver.
DKIM (DomainKeys Identified Mail) is another type of email authentication method that uses a private key to digitally sign all outgoing messages with a signature that the receiver can verify on reception using the public key included in their DNS records.
Boost Brand Trust Using BIMI (Brand Indicators for Message Identification)
BIMI (Brand Indicators for Message Identification) enables companies to use their branding in email campaigns while protecting them from phishing attacks.
The service allows companies to include the company logo, colors, and other identifiers in messages sent through their domain without exposing sensitive information to hackers or spammers who might try to mimic them.
Elevate Security with Microsoft 365
Microsoft 365 excels in email threat prevention. Its Advanced Threat Protection thwarts advanced threats like phishing and malware, while Exchange Online Protection blocks basic spam and malware.
Keep Messages Private with Encryption and TLS
Before exchanging data, TLS/SSL uses certificates to establish a secure connection between entities such as an email server and a client application.
If a certificate isn’t valid or the connection is intercepted by a third party, TLS/SSL will automatically terminate the connection without alerting either side.
Strengthen Protection: Secure Email and Cloud Gateway
One of the best ways to avoid email threats is by strengthening protection on your endpoints and networks with a cloud gateway.
It prevents malware infections and protects sensitive data from being exfiltrated from your network by blocking all malicious content from entering or leaving your network through email gateways or web applications.
Maintain Compliance: Email Archiving and Organization
It’s important to ensure that you have a comprehensive compliance solution like GDPR, HIPAA, and PCI DSS that ensures compliance with industry regulations and protection against cyber threats like ransomware attacks and phishing scams.
Use Email Sandboxing for Threat Detection
Email sandboxes isolate suspicious files and attachments from your network, allowing you to identify malware without putting your entire network at risk.
This lets you quickly detect threats without disrupting business operations or slowing productivity.
Final Words
The growth of online businesses and web-based services has added a new element to the threat environment.
For the most part, businesses have stayed on top of these threats by using effective countermeasures and incident response plans.
Sending sensitive information via email is no doubt convenient, but if done improperly could lead to major security issues.
However, email threats continue to rise in volume and complexity. Fortunately, more businesses are moving towards some effective methods to combat this growing threat.
The best way to avoid the many dangers of using email as a go-between for sensitive information would be to use an encrypted connection with a reputable, trusted provider.

*** This is a Security Bloggers Network syndicated blog from PowerDMARC authored by Ahona Rudra. Read the original post at: https://powerdmarc.com/protect-against-email-threats/
https://securityboulevard.com/2023/08/guarding-against-email-threats-effective-prevention-strategies/




:max_bytes(150000):strip_icc()/registration-3938434_1280-e2aa7e5d57264ae19b69027f14c85c2f.jpg)


