Encryption is all over the place on-line; it’s the method and applied sciences that allow you to securely log into your e mail and make on-line purchases
What varieties of info are you sending in emails or through web site connections? What are you storing in your firm servers? Inquiring minds wish to know — specifically, cybercriminals.
Data from Orca Security exhibits that greater than one-third (36%) of organizations don’t trouble encrypting the delicate knowledge they retailer within the cloud. This consists of knowledge corresponding to mental property to prospects or workers’ personally identifiable info (PII).
We’ve seen a number of cases of safety points this 12 months involving unencrypted knowledge:
One technique to battle again in opposition to cybercriminals is to make use of encryption to safe your knowledge. But what’s encryption? I imply, what does encryption imply, each within the sense of what it does and the way it secures your knowledge and communications?
Let’s hash it out.
What Does Encryption Mean? A Quick Data Encryption Definition & Meaning
Encryption is the method of taking plaintext knowledge and reworking it into one thing random and unreadable. Why? It’s a technique to secretly share info by proscribing entry to it. This means, solely your meant recipient (i.e., whoever you wish to learn the message) can entry it and nobody else can.
Encryption entails utilizing two particular varieties of cryptographic instruments:
- Encryption algorithms (which want to satisfy particular cryptographic safety requirements)
- Encryption key (which must be securely generated)
Looks easy sufficient, proper? Appearances could be deceiving. The means cryptographic processes work within the background is much more difficult than the way it seems on the floor. When you encrypt a message on the web, you’re utilizing a particular string of randomized knowledge referred to as a cryptographic key. Keys can both be a set of two distinctive keys (uneven keys), or a single key (symmetric key) that encrypts and decrypts knowledge. We’ll converse extra on uneven and symmetric key encryption a bit of later.
When utilized, the important thing disguises your message by turning it into gibberish. This ensures that solely the one that holds a corresponding secret key (i.e., your meant recipient) can learn the message by means of a course of referred to as decryption.
The following illustration exhibits a primary overview of what the method seems like when sending a safe, encrypted message:
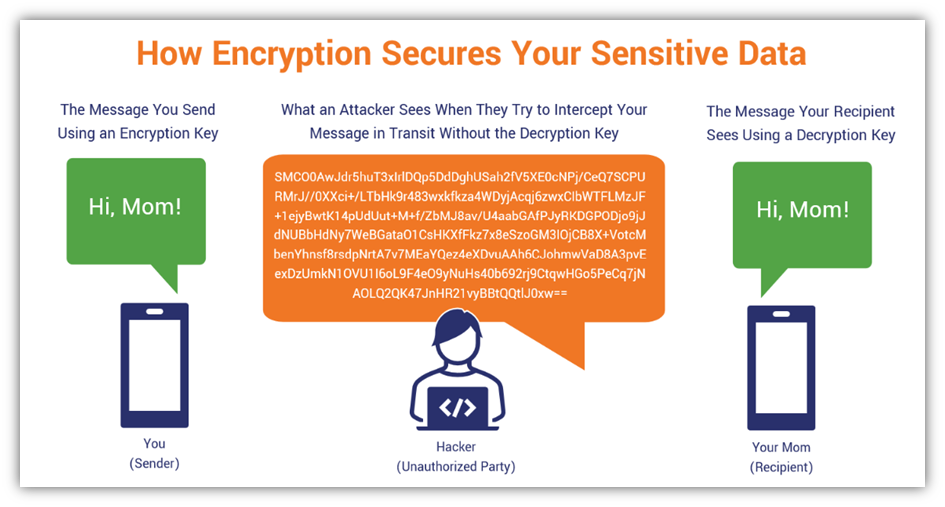
So, how are you aware if a web site is utilizing a safe connection? It’s bought a bit of padlock icon or one other safety indicator displaying within the browser’s URL bar:

We’ll delve extra into that in simply one other minute or two. But first, there’s one vital factor we wish to contact on earlier than shifting on to speaking about what encryption does…
Secure ≠ Safe
When folks see the padlock icon of their browser, they usually assume it means the web site they’re utilizing is protected. That’s not essentially true. You can nonetheless have a web site that makes use of a safe connection nevertheless it’s not protected as a result of the positioning is managed by a number of cybercriminals. This is why we at all times inform folks {that a} safe web site isn’t essentially a protected web site.
The means to assist prospects make sure that they’re connecting to your legit web site is so as to add digital identification to the equation. Your digital identification is like your passport; it’s a verifiable means for individuals who don’t know you to really feel assured doing enterprise with you. This is as a result of you may have a trusted third get together (a certificate authority) vouching that you just’re genuine — that you just actually are (insert your organization’s identify right here).
You can add digital identification by putting in a website security certificate, or what’s in any other case referred to as an SSL/TLS certificate, in your server. This will allow knowledge to transmit utilizing the safe HTTPS (hypertext transport protocol safe) protocol as an alternative of the insecure HTTP.
Here’s a fast instance of what an prolonged validation (EV) SSL/TLS certificates seems like in Google Chrome:
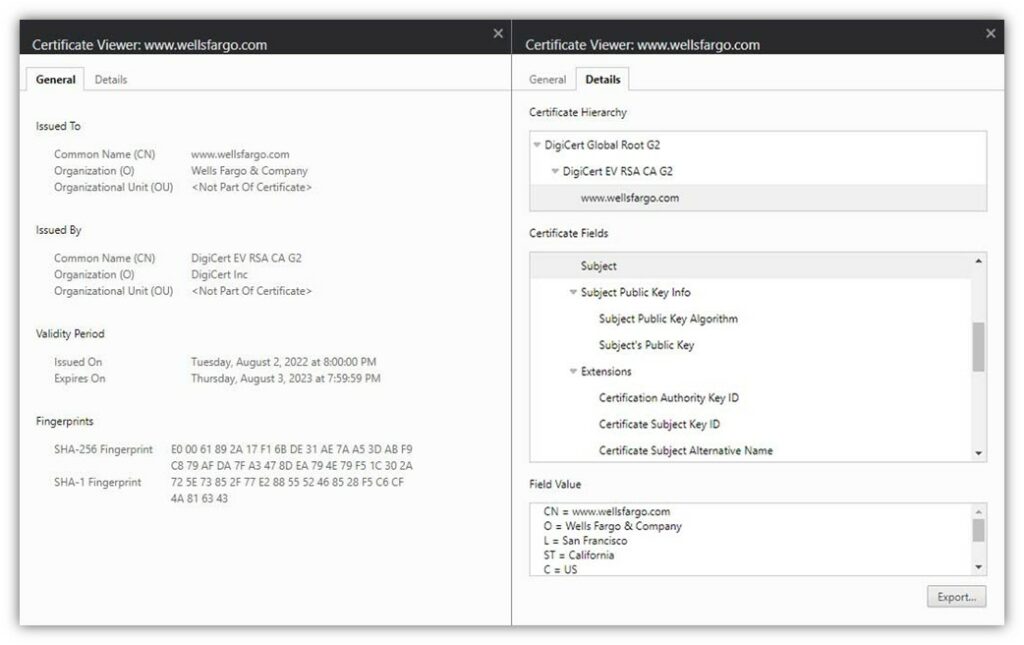
SSL/TLS certificates are available in three validation ranges: domain validation (DV), organization validation (OV), and extended validation. They rank from lowest to highest in phrases of the digital identification assurance they provide (therefore why EV certificates are typically referred to as excessive assurance certificates).
Why You Need to Secure Your Data
There are a number of the reason why your group must safe your knowledge and communication channels:
- You’re required to take action for compliance. Depending in your business or geographic area, it’s possible that there’s not less than one data security regulation or law in place that requires you to safe your knowledge utilizing encryption.
- You wish to defend your fame. The significance of your model and fame can’t be overstated. Not encrypting your knowledge is a surefire technique to get your self some undesirable publicity. If you don’t safe your knowledge, it’s possible only a matter of time earlier than it falls into cybercriminals’ arms.
- Customer belief issues to you. Encrypting your knowledge goes a great distance in serving to you develop relationships with prospects. If they know that you just do all you’ll be able to to maintain their knowledge protected, they’ll be extra prone to wish to do enterprise with you. If you don’t and let or not it’s recognized that you just’ve had a cybersecurity incident, practically one-third say they won’t do business with you.
- Fines, penalties, and lawsuits don’t attraction to you. Don’t spend cash on fines, penalties, and legal professionals in the event you don’t must. You can keep away from many conditions the place you’d face these items by securing your delicate knowledge.
- It’s the proper factor to do. There’s one thing to be stated for simply doing the proper factor as a result of it’s the proper factor to do. Protecting the information that individuals and different organizations have entrusted you to guard positively matches into that class.
Encryption Secures Your Sensitive Transmitting and/or Resting Data
Encryption can be utilized to encrypt the whole lot from knowledge sitting in your databases to the information that streams from the IoT gadgets in your community. Without encryption, daily can be open season in your most delicate knowledge. This is why organizations ought to use encryption to guard delicate knowledge always.
Protecting Data in Transit from Man-in-the-Middle Attackers
Data in transit encryption can be utilized to safe your knowledge whereas it’s shifting between endpoints. A nice instance of in-transit knowledge encryption could be seen when your prospects’ browsers ship info to your internet server. This is called in-transit knowledge encryption, which protects you from interception assaults (i.e., man-in-the-middle attacks).
Good examples of this are safe SSL/TLS web site connections. If you don’t safe your web site utilizing an SSL/TLS certificates, cybercriminals might merely wait in your prospects to log in to your web site and steal their credentials. They do that by intercepting the information, putting themselves within the center of your connection so all knowledge flows between the shopper and the server by means of them.
Not solely does this spell dangerous information in your prospects, nevertheless it’ll be dangerous information for you since they’ll now not belief you to guard their knowledge.
Keeping Your At-Rest Data Safe On Your Servers
If your knowledge is sitting in your server, that mechanically means it’s protected from attackers, proper? Not essentially.Data at relaxation encryption performs an vital position in protecting the information sitting in your databases, inboxes, and different vital repositories safe. For instance, if somebody hacks your e mail server, any unencrypted messages are in danger of compromise.
Encrypted Data Is Meant to Be Decrypted…
Yes, you learn that accurately: Encryption is called a two-way operate as a result of encrypted knowledge is supposed to be decrypted by somebody who has the suitable key. When you encrypt one thing, you could use a key to decrypt that knowledge. In uneven encryption, you may have two separate keys and every key performs a separate operate (one encrypts, one decrypts). In symmetric encryption, it’s a single key that performs each capabilities.
It’s vital to notice that encryption algorithms differ from hash ciphers. While encryption ciphers are supposed to be reversed, hash algorithms are designed to function one-way capabilities. Their ensuing strings of knowledge are not meant to be reverse-engineered [and, frankly, it’s too impractical to try to do so]). And as an alternative of getting used to encrypt knowledge, they’re used as knowledge integrity mechanisms to show that knowledge hasn’t been altered because it was digitally signed.
Encryption is a means for 2 events to speak securely. Historically, this meant two events must meet head to head to securely alternate keys. They’d use the identical key to encrypt and decrypt info. This is an instance of a sort of encryption referred to as symmetric encryption. Also referred to as personal key cryptography, this strategy entails utilizing a single key to scramble and unscramble your messages.
Here’s a primary take a look at how encryption and decryption work utilizing symmetric (matching) keys:
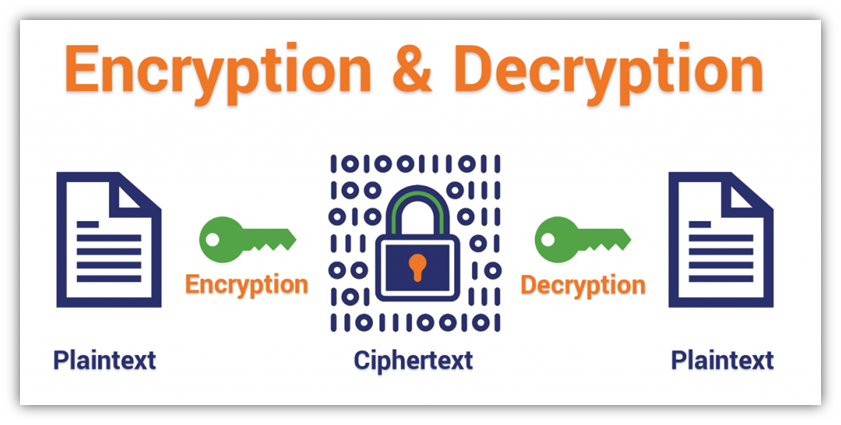
Of course, the encryption ciphers we use to speak over the web are much more advanced than the easy instance we’ve supplied above. However, the graphic provides you the essential concept of the ideas of encryption and decryption.
Symmetric Encryption Has Been the Go-To Method Throughout History
Symmetric encryption is nothing new; it’s been round for 1000’s of years, courting again to not less than historical Egypt. It’s the outdated, trusted conflict horse of cryptography and it’s had many reinventions over its lifetime.
When I used to be a child, I had out-of-state cousins who would come to go to my household. My cousins and I might alternate handwritten letters, and one of my cousins used to put in writing temporary messages in ciphertext. It was a primary shift cipher (AKA a Caesar cipher), that means that you just simply shift a letter by a number of characters within the alphabet. The quantity of actions is set by a secret key that solely we’d know. (This means, her siblings and mine couldn’t learn our messages.)
For instance, if we used a key of 6, then “a” would change into “g” and so forth. So, if the cousin wrote the phrase “seaside” and used a key of 6, then it will change into “hkgin.” Because we each had data of the important thing, this can be a primary instance of the way it seems once you use symmetric encryption.
Traditional (Symmetric) Encryption Can’t Stand on Its Own in an Internet World
We dwell in a time when the web has change into integral to companies. This invention is a double-edged sword; it’s nice as a result of firms can have interaction in distant, near-instantaneous communications. But that additionally signifies that nobody desires to hop on a aircraft and fly midway all over the world each time they should do a transaction.
But why would you could do that? Because the web is inherently insecure. It’s an open public community that sends plaintext knowledge, that means that your delicate info could be intercepted by dangerous guys who can use it to hold out every kind of evil (knowledge theft, identification theft, fraudulent transactions — the listing goes on). This is why business specialists needed to provide you with a means for folks to speak securely with out having to first meet as much as alternate symmetric encryption keys.
Why Asymmetric Encryption Is Essential to Secure Online Communications
In a nutshell, asymmetric encryption (i.e., public key encryption) allows folks to speak remotely with out having to satisfy up in particular person. This kind of encryption makes use of a pair of distinctive (however mathematically associated) keys to hold out the encryption and decryption processes.
People name it by totally different names, however this kind of encryption boils all the way down to the next breakdown:
- The sending get together encrypts the message utilizing their public key.
- The receiving get together decrypts the message utilizing the corresponding (separate) secret key.
What this does is allow you to speak knowledge in open channels (public and insecure networks), corresponding to on the Internet. Here’s a take a look at how this course of works from a bit of extra technical perspective:

Think of the final time you made a web based buy. When establishing the web site connection, your browser reached out to the web site’s server. The two events exchanged some key info (actually and figuratively talking) that they used to alternate a session key. This secret is what they then used the remainder of the session to speak as a result of it required fewer assets than an uneven connection.
Asymmetric vs Symmetric Encryption: Is One Better Than the Other?
It’s not a lot a query of which one is best; asymmetric and symmetric encryption each play vital roles in securing on-line knowledge and communications. Quite frankly, you want each to attain safe web site connections:
- You use uneven encryption to securely alternate key-related info
- You use that shared key info to create a safe symmetric session that can be utilized to speak the remainder of the session
You use uneven first as a result of it’s a safe technique to share your symmetric keys on the (insecure) web. But uneven algorithms require loads of assets, that means they’re not nice at scale (i.e., enterprises dealing with huge visitors). So, the smarter concept can be to make use of uneven algorithms at the start after which swap to symmetric algorithms which can be much less taxing at scale.
The More Important Considerations Are Key Security and Certificate Management
The encryption algorithms you employ are solely nearly as good because the safety you employ to guard your cryptographic keys. If even one of your cryptographic keys will get uncovered, then you definately’re in for a world of harm as a result of it signifies that each bit of knowledge that key encrypted is now in danger of compromise. For instance, this may very well be the case in the event you didn’t use algorithms that enabled perfect forward secrecy.
Furthermore, you additionally have to fastidiously observe and handle all of the certificates in your setting. If even one certificates expires and remains to be used in your web site, for instance, then it means:
- Users see ugly “not safe” warning messages in your web site
- All knowledge that transmits to your web site is insecure
Final Thoughts on What Encryption Means
As you’ll be able to see, answering the query “what’s encryption?” within the easiest phrases isn’t at all times straightforward, however we gave it our greatest shot. (It’s straightforward to overthink issues.) Hopefully, you’ve discovered this text each informative and helpful as you go about your day. The huge takeaways we would like you to go away with embrace the next:
- Encryption is a standard cryptographic course of for disguising or concealing knowledge
- Encryption secures your knowledge each in transit (suppose SSL/TLS) and at relaxation (suppose of emails in your server)
- It could be carried out utilizing distinctive keys (symmetric encryption) or equivalent key pairs (symmetric encryption)
- For encryption to work, you will need to fastidiously handle your certificates and keys
https://information.google.com/__i/rss/rd/articles/CBMiNGh0dHBzOi8vd3d3LnRoZXNzbHN0b3JlLmNvbS9ibG9nL3doYXQtaXMtZW5jcnlwdGlvbi_SAQA?oc=5






