A Linux variant of a backdoor often known as SideWalk was used to focus on a Hong Kong college in February 2021, underscoring the cross-platform talents of the implant.
Slovak cybersecurity agency ESET, which detected the malware within the college’s community, attributed the backdoor to a nation-state actor dubbed SparklingGoblin. The unnamed college is claimed to have been already focused by the group in May 2020 in the course of the student protests.
“The group repeatedly focused this group over a protracted interval of time, efficiently compromising a number of key servers, together with a print server, an electronic mail server, and a server used to handle scholar schedules and course registrations,” ESET said in a report shared with The Hacker News.
SparklingGoblin is the identify given to a Chinese superior persistent menace (APT) group with connections to the Winnti umbrella (aka APT41, Barium, Earth Baku, or Wicked Panda). It’s primarily identified for its assaults focusing on varied entities in East and Southeast Asia not less than since 2019, with a particular give attention to the educational sector.
In August 2021, ESET unearthed a brand new piece of customized Windows malware codenamed SideWalk (aka ScrambleCross) that was completely leveraged by the actor to strike an unnamed laptop retail firm based mostly within the U.S.
Subsequent findings from Symantec, half of Broadcom software program, have linked the use of SideWalk to an espionage assault group it tracks underneath the moniker Grayfly, whereas stating the malware’s similarities to that of Crosswalk.
“SparklingGoblin’s Tactics, Techniques and Procedures (TTPs) partially overlap with APT41 TTPs,” Mathieu Tartare, malware researcher at ESET, advised The Hacker News. “Grayfly’s definition given by Symantec appears to (not less than partially) overlap with SparklingGoblin.”
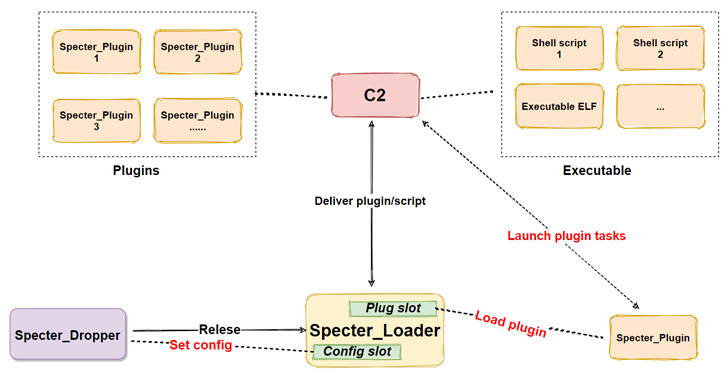
The newest analysis from ESET dives into SideWalk’s Linux counterpart (initially known as StageClient in July 2021), with the evaluation additionally uncovering that Specter RAT, a Linux botnet that got here to mild in September 2020, is in actual fact an early Linux variant of SideWalk as properly.
Aside from a number of code similarities between the SideWalk Linux and varied SparklingGoblin instruments, one of the Linux samples has been discovered utilizing a command-and-control tackle (66.42.103[.]222) that was previously used by SparklingGoblin.
Other commonalities embody the use of the identical bespoke ChaCha20 implementation, a number of threads to execute one explicit process, ChaCha20 algorithm for decrypting its configuration, and an an identical dead drop resolver payload.
Despite these overlaps, there are some important adjustments, essentially the most notable being the swap from C to C++, addition of new built-in modules to execute scheduled duties and collect system info, and adjustments to 4 instructions that aren’t dealt with within the Linux model.
“Since we now have seen the Linux variant solely as soon as in our telemetry (deployed at a Hong Kong college in February 2021) one can think about the Linux variant to be much less prevalent — however we even have much less visibility on Linux techniques which may clarify this,” Tartare stated.
“On the opposite hand, the Specter Linux variant is used towards IP cameras and NVR and DVR units (on which we now have no visibility) and is mass unfold by exploiting a vulnerability on such units.”
https://thehackernews.com/2022/09/sparklinggoblin-apt-hackers-using-new.html