Zero-Trust has emerged as a number one safety framework in in the present day’s extraordinarily risk-laden IT surroundings. However, efforts to implement zero-trust are thwarted by one of many oldest and most entrenched Internet applied sciences of all of them … e mail.
Never earlier than has group cyber-security been extra challenged. Companies are beneath steady assault and, by almost all measures, are usually not doing effectively regardless of elevated investments in defending their networks and data. Core causes for the deterioration stem from the mixed results of widespread enterprise digitization, the rise of worker work from everywhere, and the elevated sophistication of assaults. So dire has the cyber-security state of affairs change into that it’s only prudent to assume breach, the group is overrun, and nothing will be trusted. As a consequence, “zero-trust” methodology has taken the entrance stage as an enterprise safety framework.
“The foremost idea behind the zero-trust safety mannequin is “by no means belief, all the time confirm,” which implies that gadgets shouldn’t be trusted by default, even when they’re linked to a permissioned community reminiscent of a company LAN and even when they have been beforehand verified.” — Wikipedia
As organizations undertake zero-trust, they put robust identification and authentication into place at each doable entry level — cloud companies, doc scanners, consumer gadgets, and so forth. Yet regardless of the widest nets forged by zero-trust implementors, a big entry level is commonly neglected. This entry level, maybe the most important of all of them, can compromise the perfect well-laid zero-trust plans — the entry level is e mail.
A “Total Trust” system hiding within the open of each group
Born fifty years in the past in a less complicated, extra trusting Internet, e mail is a ubiquitous artifact of a bygone period. Although authentication is required to entry an e mail account, a important safety hole exists between the e-mail message and its attachments. Access to an e mail message routinely grants entry to all file attachments. This hole creates a safety gap that may by no means be addressed with single-sign-on, USB dongles, biometric controls, or the rest. Email is a “total-trust” system with profoundly detrimental implications that proceed to undermine all efforts at cyber-security.

Let’s take a look at what slips by way of the message-attachment safety hole. Here are some concrete and visual methods during which e mail’s “Total Trust” paradigm undermines organizational safety:
Internal breaches – e mail servers, archives, and consumer e mail purchasers
The news cycle is rife with tales of e mail system breaches. The whole belief embedded in e mail’s design is one issue that makes these occasions so damaging. This design permits a foul actor full entry to all of the content material in an e mail when an e mail server or account is breached. Once the adversary has gained entry to the messages, whole belief is granted, and nothing stands in the way in which to the wealthy treasure trove of delicate file attachments.

External breaches – emails despatched exterior the group
Every e mail that’s despatched is an act of whole blind belief. The message and any information shared externally by way of e mail are despatched completely exterior the management of the sender and the sender’s group. Standard e mail gives no visibility, monitoring, or safety for itself or its file attachments. Not solely is belief implicit when e mail is distributed, however e mail’s structure creates full copies of itself throughout supply, dramatically rising delicate content material publicity. The duplicity of e mail and the penchant of senders to repeat a number of recipients makes e mail one of many most significant contributors to data sprawl.
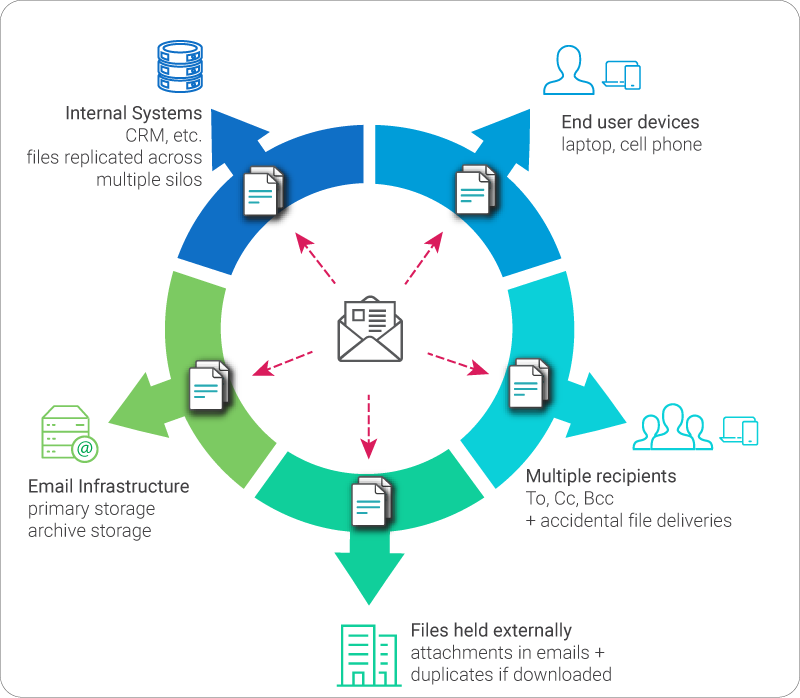
Inbound Threats – emails getting into the group
One of essentially the most important threats to organizations is weaponized (malicious) information. Here once more, the whole belief between the e-mail message and its attachments implies that an attacker want solely ship an e mail with an attachment. Wherever a message is acquired, usually nothing stands between the recipient and their opening an contaminated file attachment instantly on their system. We should do not forget that even options that assure 99% effectiveness in screening harmful information imply a 100% probability of a profitable assault!

The Challenge and Solution
The inheritance and adherence to the e-mail and its antiquated belief mannequin wreaks havoc in in the present day’s risk surroundings. Email is deeply entrenched and demanding to the mission of almost each group. Given agency and long-held consumer habits, even essentially the most minor modifications to how e mail is used may cause painful disruption. But persevering with with the established order means dwelling with a excessive diploma of danger.
Fortunately, applied sciences exist to soundly share content material internally and externally in ways in which present robust authentication, governance, and monitoring. Enterprise cloud storage companies, reminiscent of Box, DropBox, Egnyte, Sharepoint Online, OneDrive for Business, and Google Drive, supply organizations a prepared file-sharing different to e mail attachments. These companies have been designed from inception to share content material securely by way of URL hyperlinks with security measures like multi-factor authentication, self-expiration, obtain limits, and extra. Furthermore, modern applied sciences exist to routinely convert attachments into safe cloud storage hyperlinks. These services enable customers to proceed to make use of e mail as they all the time have, but afford organizations the safety they want.
Cloud Storage for Secure File Sharing
Let’s see how the three e mail attachment danger situations offered above look when utilizing cloud storage hyperlinks.
Internal breaches when utilizing cloud storage hyperlinks
When utilizing cloud storage hyperlinks, no information are embedded in e mail messages. Unlike e mail attachments, cloud storage hyperlinks can require authentication. Technologies exist to make sure that all file attachments in internally saved emails (e.g., on servers or consumer e mail purchasers) are saved securely in cloud storage behind firm access-only authentication. In this situation, a breached e mail server or e mail account doesn’t grant implicit entry to information.

External breaches when utilizing cloud storage hyperlinks
The most pronounced distinction between sharing information with cloud storage hyperlinks versus e mail attachments is when sharing externally. Emails blindly belief the recipient with the content material despatched. In distinction, sending cloud storage hyperlinks retains the file in possession of the sender whereas permitting the sender to require authentication, auto-expire hyperlinks, observe, and revoke entry.

Inbound Threats when utilizing cloud storage hyperlinks
Services exist that extract inbound e mail attachments and add them into the safe cloud earlier than supply to customers. Once uploaded, many cloud storage companies do extra scanning for malware. When messages are delivered to customers, e mail attachments are solely accessible by way of cloud storage hyperlinks that require customers to soundly preview content material earlier than downloading. Given the variety of recipients who’re not directly copied in messages (e.g., in Cc), it is a surprisingly efficient danger discount technique since, for a lot of of those customers, content material want solely be seen, not downloaded.

Time for Change
As evolution mandates, we should adapt or die. Today firms function in an surroundings that was inconceivable when the primary e mail was despatched. Email has change into a foundational expertise that helps bind the world collectively. However, it additionally represents one of many best dangers to organizations globally. Fortunately, the whole lot it must evolve is inside straightforward attain!
https://medium.datadriveninvestor.com/you-cant-implement-zero-trust-without-addressing-this-ce35fdd4f97




:max_bytes(150000):strip_icc()/HowtoSpecifyaPreferredSMTPServerforaMacOSXMailAccount2016-01-04-568a7f403df78ccc153b7b78.png)
