Cybersecurity researchers have detailed the varied measures ransomware actors have taken to obscure their true id on-line in addition to the internet hosting location of their internet server infrastructure.
“Most ransomware operators use internet hosting suppliers outdoors their nation of origin (akin to Sweden, Germany, and Singapore) to host their ransomware operations websites,” Cisco Talos researcher Paul Eubanks said. “They use VPS hop-points as a proxy to conceal their true location once they join to their ransomware internet infrastructure for distant administration duties.”
Also outstanding are the usage of the TOR community and DNS proxy registration providers to present an added layer of anonymity for his or her unlawful operations.
But by benefiting from the risk actors’ operational safety missteps and different methods, the cybersecurity agency disclosed final week that it was in a position to determine TOR hidden providers hosted on public IP addresses, a few of that are beforehand unknown infrastructure related to DarkAngels, Snatch, Quantum, and Nokoyawa ransomware teams.
While ransomware teams are identified to rely on the darkish internet to conceal their illicit actions starting from leaking stolen information to negotiating funds with victims, Talos disclosed that it was in a position to determine “public IP addresses internet hosting the identical risk actor infrastructure as these on the darkish internet.”
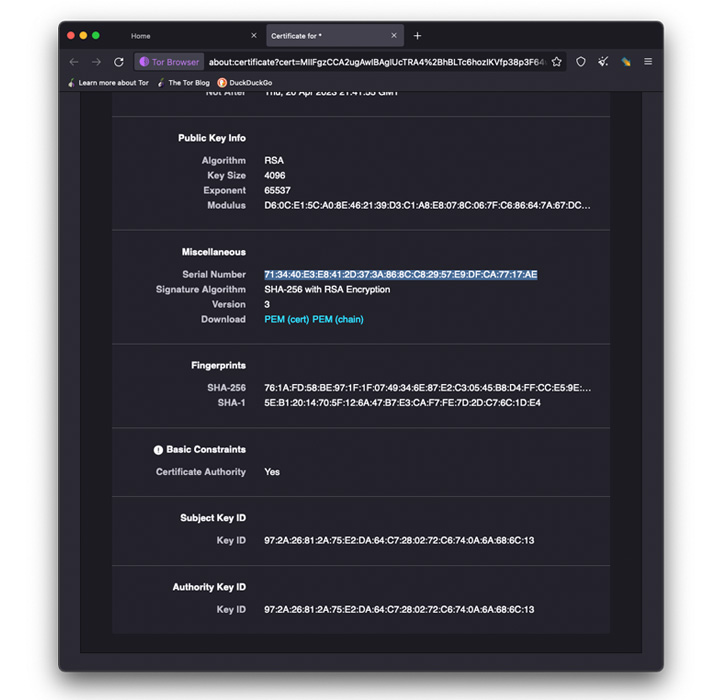
“The strategies we used to determine the general public web IPs concerned matching risk actors’ [self-signed] TLS certificate serial numbers and web page components with these listed on the general public web,” Eubanks stated.
Besides TLS certificates matching, a second technique employed to uncover the adversaries’ clear internet infrastructures entailed checking the favicons related to the darknet web sites towards the general public web utilizing internet crawlers like Shodan.
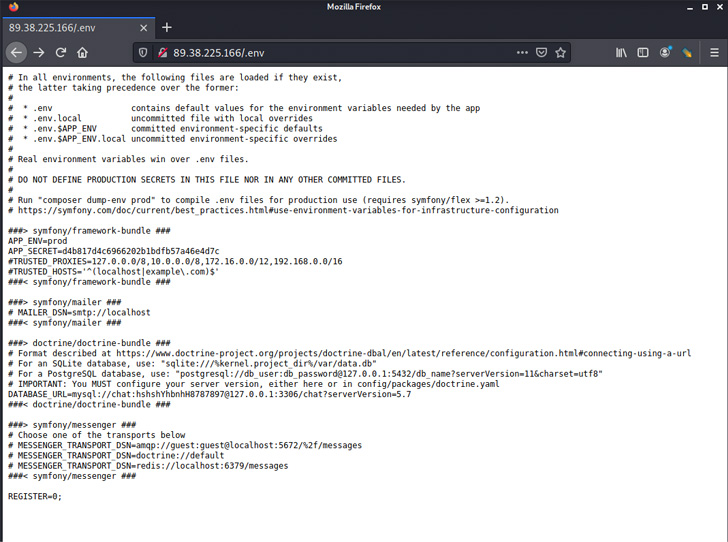
In the case of Nokoyawa, a brand new Windows ransomware pressure that appeared earlier this 12 months and shares substantial code similarities with Karma, the positioning hosted on the TOR hidden service was discovered to harbor a listing traversal flaw that enabled the researchers to entry the “/var/log/auth.log” file used to seize person logins.
The findings display that not solely are the felony actors’ leak websites accessible for any person on the web, different infrastructure parts, together with figuring out server information, have been left uncovered, successfully making it attainable to get hold of the login places used to administer the ransomware servers.
Further evaluation of the profitable root person logins confirmed that they originated from two IP addresses 5.230.29[.]12 and 176.119.0[.]195, the previous of which belongs to GHOSTnet GmbH, a internet hosting supplier that gives Virtual Private Server (VPS) providers.
“176.119.0[.]195 nonetheless belongs to AS58271 which is listed beneath the identify Tyatkova Oksana Valerievna,” Eubanks famous. “It’s attainable the operator forgot to use the German-based VPS for obfuscation and logged right into a session with this internet server immediately from their true location at 176.119.0[.]195.”
LockBit provides a bug bounty program to its revamped RaaS operation
The growth comes because the operators of the rising Black Basta ransomware expanded its assault arsenal by utilizing QakBot for preliminary entry and lateral motion, and benefiting from the PrintNightmare vulnerability (CVE-2021-34527) to conduct privileged file operations.
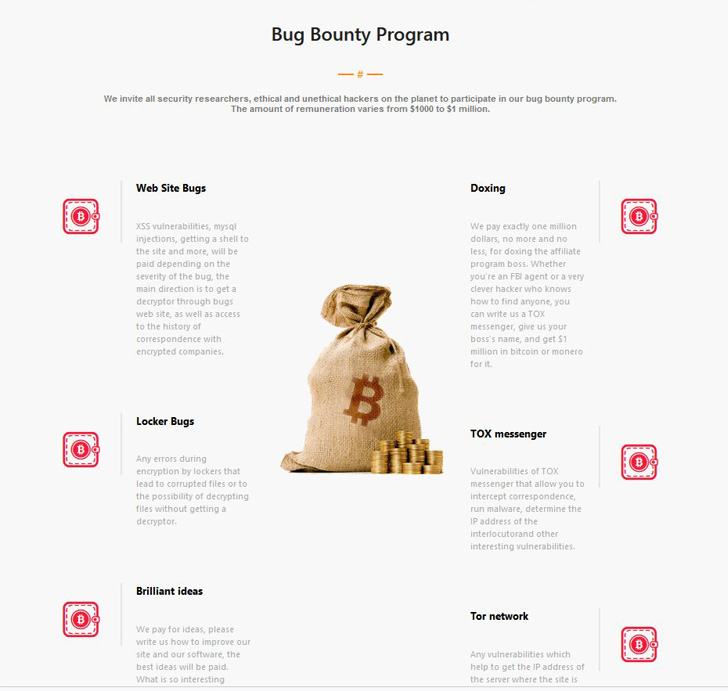
What’s extra, the LockBit ransomware gang final week announced the discharge of LockBit 3.0 with the message “Make Ransomware Great Again!,” as well as to launching their very own Bug Bounty program, providing rewards ranging between $1,000 and $1 million for figuring out safety flaws and “sensible concepts” to enhance its software program.
“The launch of LockBit 3.0 with the introduction of a bug bounty program is a proper invitation to cybercriminals to assist help the group in its quest to stay on the prime,” Satnam Narang, senior employees analysis engineer at Tenable, stated in an announcement shared with The Hacker News.
“A key focus of the bug bounty program are defensive measures: Preventing safety researchers and regulation enforcement from discovering bugs in its leak websites or ransomware, figuring out ways in which members together with the associates program boss could possibly be doxed, in addition to discovering bugs throughout the messaging software program utilized by the group for inner communications and the Tor community itself.”
“The risk of being doxed or recognized indicators that regulation enforcement efforts are clearly an amazing concern for teams like LockBit. Finally, the group is planning to provide Zcash as a fee choice, which is important, as Zcash is tougher to hint than Bitcoin, making it tougher for researchers to preserve tabs on the group’s exercise.”
https://thehackernews.com/2022/07/researchers-share-techniques-to-uncover.html