OpenSMTPD has been discovered weak to yet one more essential vulnerability that would permit distant attackers to take full management over e mail servers working BSD or Linux working methods.
OpenSMTPD, also called OpenBSD SMTP Server, is an open-source implementation of the Simple Mail Transfer Protocol (SMTP) to ship messages on an area machine or to relay them to different SMTP servers.
It was initially developed as a part of the OpenBSD mission however now comes pre-installed on many UNIX-based methods.
Discovered by consultants at Qualys Research Labs, who additionally reported a similar RCE flaw within the e mail server software final month, the newest out-of-bounds learn problem, tracked as CVE-2020-8794, resides in a part of the OpenSMTPD’s client-side code that was launched almost 5 years in the past.
Just just like the earlier problem, which attackers began exploiting in the wild only a day after its public disclosure, the brand new OpenSMTPD flaw may additionally let distant hackers execute arbitrary instructions on the weak servers with privileges of both root or any non-root person.
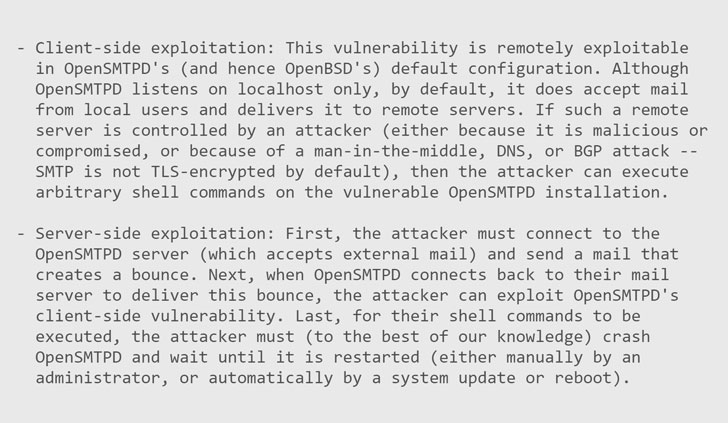
As described within the screenshot of the advisory, the flaw could be exploited by an area or distant attacker in two methods by sending specifically crafted SMTP messages, one works within the default configuration, and the second leverages e mail bounce mechanism.
“We developed a easy exploit for this vulnerability and efficiently examined it in opposition to OpenBSD 6.6 (the present launch), OpenBSD 5.9 (the primary weak launch), Debian 10 (steady), Debian 11 (testing), and Fedora 31,” the advisory says.
“We examined our exploit in opposition to the current modifications in OpenSMTPD 6.6.3p1, and our outcomes are: if the “mbox” methodology is used for native supply (the default in OpenBSD -current), then arbitrary command execution as root remains to be doable; in any other case (if the “maildir” methodology is used, for instance), arbitrary command execution as any non-root person is feasible.”
However, the Qualys group has determined to withhold the exploitation particulars and exploit code till twenty sixth February, giving weak OpenSMTPD’s customers a two-day window to patch their methods.
If you are additionally working BSD or Linux servers with a weak model of the OpenSMTPD, you are suggested to obtain OpenSMTPD 6.6.4p1 and apply the patch as quickly as doable.
https://thehackernews.com/2020/02/opensmtpd-email-vulnerability.html