Numerous malicious entities spoof their e mail to cover their identification and check out to rip-off your organization. Email spoofing isn’t subtle. It additionally doesn’t want high-end cybercriminals. That stated, it’s nonetheless annoying and exhausting to keep away from in case you don’t have good options.
Currently, cybercriminals try e mail spoofing in 4 methods:
- Different nation extension
- Discreet misspell
- Misleading area title
- Hacked sender tackle
Cybersecurity workers worldwide attempt to hunt these assaults repeatedly. This is as a result of e mail spoofing might be harmful. It can harm you, and in addition harm the area or assumed area it’s coming from.
To make sure you’re completely protected from these assaults, you’ll want a mix of software program options that can filter 90% of spoofing assaults. You’ll additionally want some easy cybersecurity guidelines for individuals who will learn emails. In this text, I’ll information you to be taught all about e mail spoofing. I’ll miss on the variable coding stuff and solely deal with what you would possibly expertise as a enterprise. Later on, I’ll contact on how one can defend your self, how e mail spoofing works, forms of worker coaching, and at last some third-party software program to make your life simpler on this regard. Let’s begin with the definition of e mail spoofing first.
What Is Email Spoofing?
In quick, e mail spoofing is when cybercriminals forge the tackle they ship the e-mail from. This can relate to the sender’s title and even the metadata behind the e-mail. It is usually a technically subtle assault the place cybercriminals hack and use an e mail server for this function. It will also be a low-tech rip-off the place cybercriminals use an tackle that solely seems to be like what you’d anticipate.
In most circumstances, cybercriminals use e mail spoofing for phishing, the place they’ll attempt to steal your organization knowledge and entry to your inside community. Here, the cybercriminal will ship both hyperlinks or executable information by way of e mail from an tackle that the corporate server and workers would belief.
Next, I’ll undergo how every of the 4 widespread e mail spoofing assaults works and how one can acknowledge them throughout regular operations.
How Does Email Spoofing Work?
The thought behind spoofing assaults is sort of easy. The malicious entity on-line will use the pretend tackle to idiot you into freely giving your vital knowledge. This malicious entity could be both a human cybercriminal or a malicious AI mail server.
To do that, they’ll want to surpass 2 hurdles.
- The software program filtering emails with any malicious code or stopping emails that aren’t allowlisted. Companies utilizing this sort of software program will cease all, however probably the most subtle spoofing assaults from ever reaching their inbox.
- The individual really studying the e-mail. The kind, wording, and hyperlinks want to look natural and related to one thing they’d anticipate from the assumed supply. For instance, no person will consider that somebody from Google despatched them an e mail to say they’re strapped for money.
Let’s see subsequent how cybercriminals can bypass the two points I mentioned above.
4 Tactics to Achieve Email Spoofing
To obtain e mail spoofing, cybercriminals have 4 techniques to use and bypass any hurdles. I’ll now go from probably the most primary ones to probably the most subtle ones, every requiring extra superior safety than the final.
1. Misleading Domain Name
In many circumstances, it’s inconceivable to make an identical area to the one whose identification the cybercriminal desires to assume. That’s why they’ll fall on very determined techniques of utilizing deceptive domains to prop up their rip-off.
For occasion, let’s say your organization is named ExampleCompany and you’ve got an organization web site at examplecompany.com. Here, the one method to obtain an e mail from this area is for somebody to have entry to your server or administrator credentials. That means you’re already hacked!
Cybercriminals can’t use this area although, in order that they’ll purchase an elongated kind like internalexamplecompany.com and ship emails from [email protected]
Cybercriminals received’t ship plenty of emails from this tackle, and it’s not bought by your organization. Thus, it’ll be utterly official for the server to push this e mail by way of.
Pro Tip
- Ensure your e mail server flags all emails coming from exterior of the corporate or that aren’t straight whitelisted. This will stop nearly all of those scams from working.

2. Different Country Extension
This possibility is a little more superior, as cybercriminals want to cover their WHOIS protocol that might present their data. That stated, it’s usually attainable to use pretend data with some area retailers. It’s additionally attainable to purchase the identical one as your organization however with a distinct extension.
The most typical nation extension for this function is the Adriatic nation of Montenegro which has a useful extension of ‘’me’’. Then, the pretend area in our operating instance can be examplecompany.me which would appear like one thing inside. United States extensions (us) are additionally fairly frequent.
In many circumstances, your server will even acknowledge this as an exterior message. If the cybercriminal can connect the brand new area to your personal as a reroute, then it’s attainable to bypass this hurdle. That’s why the corporate must also purchase all attainable nation extensions underneath their area title.
Pro Tip
- Buy out all area title nation extensions on your firm. Most sellers will promote them in bulk for under cents per yr, making this a straightforward answer to this drawback.
3. Discreet Misspell
When attacking corporations, a discreet misspelling assault could be very uncommon. That’s as a result of it at all times seems as an exterior tackle. In most circumstances, cybercriminals will use it in opposition to people. That’s why you need to stop it, as this assault can tarnish your organization’s title.
To make these assaults, cybercriminals will make an identical area title to one that you just acknowledge. In our case, that might be exampleconpany.com. Most folks will miss that one ‘n’ changing the ‘m’ because the thoughts will go by way of this e mail in a short time.
These scams have been frequent for some time with cybercriminals utilizing domains like goggle or facebouk to rip-off folks. While they’re humorous when you realize what to search for, they’re additionally tough to spot while you’re in a rush.
Pro Tip
- Find the entire variations of your organization area title and purchase them as nicely. In most circumstances, it’ll even help your website positioning and visitors. If you may’t purchase the area, blocklist it internally.
4. Hacked Sender Address
This is by far probably the most difficult method to do e mail spoofing. It requires an current cybersecurity breach with what’s nonetheless thought-about a trusted server. Opportunities like this have turn into more and more uncommon with present zero-hour cybersecurity options. However, you must nonetheless have protocols in place to know if that is taking place.
Here, the SMTP protocol of the sufferer has been compromised. Then, you’ll obtain emails as in the event that they had been from that sender. If they’re allowlisted, this can present them as protected and trusted. This makes this assault one of the vital problematic.
Sadly, hacked sender addresses don’t have any technical options. You can nonetheless keep away from them although typically with some worker guidelines on your workers.
Pro Tip
- Only click on on hyperlinks and disclose data in a thread e mail you’ve began. If you get a request for vital knowledge, escalate an issue and make somebody ship that tackle an e mail reaffirming the request.
Now, I’ll talk about probably the most frequent motive for e mail spoofing: e mail phishing. I’ll record the forms of e mail phishing, how they’ll look, and the way to defend your organization from them.
What Is Email Phishing?
Phishing emails are nothing greater than scams the place folks attempt to cover hyperlinks and executable information in one thing you would possibly overlook and belief. They appear to be common emails and can normally spell some type of urgency.
| Your pc is underneath menace proper now. If you need to defend your self with only one click on, comply with the LINK HERE. |
That stated, in contrast to us, they received’t attempt to push you to subscribe to a publication that truly has some helpful data. Cybercriminals will attempt to get your emails, passwords, and different personal data to rob you. Otherwise, they could steal your identification, so another person can rob you.
In conclusion, phishing emails are very harmful. That’s particularly in corporations receiving dozens or a whole bunch of emails per individual daily. Now, let’s be taught in regards to the forms of e mail phishing.
4 Types of Email Phishing
In many circumstances, phishing assaults will border on foolish. We all know the “Nigerian Prince” rip-off. They solid a large internet, so everybody would in all probability discover them on a primary learn.
Some methods will goal your organization way more exactly although. The scammer would possibly know the title and place of the individual tasked with studying the e-mail. After that, the scammer makes use of a phishing e mail to trick the worker into considering they’re their boss.
Phishing is available in 4 differing types. Each of those may have its personal particular strategy. Still, take be aware that approaches right here have few technical necessities. They additionally fall into the storytelling artwork kind by the scammer, not strictly coding prowess by the hacker.
1. Tech Support Phishing Scams
Many corporations depend on their tech assist to have their techniques working and the whole lot working. Some techies are additionally very sociable. Chances are, they converse very straight if any points resurface. Cybercriminals know this and can attempt to exploit it.
Here’s an instance of what a TS phishing e mail would possibly appear to be:
| SECURITY NOTICE
Hi, Dan right here from tech assist. I’ve seen that your passwords are compromised. You’ve in all probability clicked on one thing improper. Be cautious subsequent time. Click right here to verify your identification – LINK |
Now, relying on the scale of the corporate, you may clearly see that this e mail is a rip-off. For one, you realize that you just don’t have tech assist. Additionally, that individual might be sitting 10 toes from you. That stated, in a big firm, you could be in a rush to remedy this earlier than your superiors discover out. As a outcome, you fall for it.
To stop this, all workers in your organization want to understand how to discover rip-off emails. Alternatively, you might want a rule for workers to reply to emails like this with a request that the answer is finished in individual. Your workers must also CC their supervisor within the thread.
2. Clone Phishing Scams
Copying an inside e mail with out ample data is difficult. That’s why most cybercriminals use your organization’s exterior connections to rip-off you. Clone phishing is making an attempt to copy the look and type of an official e mail from corporations like PayPal, Google, Amazon, or related giants you’d acknowledge.
The thought behind that is that you just received’t look intently on the area title. You’ll additionally disregard that it’s coming exterior of your organization as anticipated. Once you click on, you’ll execute the file. After that, you’ve despatched knowledge robotically or entered new data on a pretend internet web page.
Still, you may simply stop this with lively allowlists. That stated, even in case you haven’t but made these lists, you may merely escalate every of those cases and solely reply to the thread emails your organization has began.
3. Spear Phishing Scams
Spear phishing is the place issues get difficult. Like any good rip-off, this one collects knowledge about what you are promoting beforehand. After that, it tries to leverage that data in opposition to you. These assaults are technically related to others, however they’re extra exact and harmful due to the data collected by the hackers.
In quick, the scammers will discover out who works within the firm, who would in all probability learn the e-mail despatched, or which sort of particular software program and companies the enterprise might use. They’ll then make a custom-made phishing e mail concentrating on the individual behind the display straight.
Aside from allowlisting and software program options which may cease this e mail from even reaching your inbox, the one method to stop this rip-off is to have open communication inside the corporate. 9 out of 10 scams like this occur because the folks studying and responding to emails are afraid to escalate the problem.

4. Whale Phishing Scams
This is among the most troublesome varieties. It can also occur if a senior in some firm has been hacked privately. Unless you might have open communication within the firm, this rip-off will normally take maintain earlier than you discover it.
With whale phishing, cybercriminals will assume the identification of a few of the senior companions within the firm just like the CEO or CFO. They’ll then request firm data from lower-rank workers.
The e mail despatched will stress the urgency of the data. If mixed with spear-phishing, it may well additionally refer to the person who ought to give the data straight.
In this case, workers must be clearly instructed to request data from the official CEO e mail from inside the corporate. They must also embrace their supervisor and different larger companions within the dialog. Otherwise, these workers shall be pressed to share the data with cybercriminals.
These forms of emails have possibilities to go by way of regardless of one of the best software program. If you additionally don’t have a superb, open, and relaxed firm tradition, the common habits of the CEO could be the downfall of the entire enterprise.
Next, I’ll undergo the technical methods to defend your mail server.
How to Protect Your Business from Email Spoofing
When studying about e mail spoofing prevention and phishing talks, you’ll hear rather a lot about coaching and worker competency too. That’s as a result of that is the final line of protection after software program can not do something. That stated, good software program prevents 90% of e mail spoofing assaults.
At the second, each mail server ought to have 4 protocols to cease the spoofed emails from reaching your inbox. Free e mail operators like Gmail and Microsoft Outlook may have most of those choices enabled by default. It’s nonetheless higher although to calibrate your mail server additional and make allowlist/blocklist tables. Let’s now uncover the 4 protocols:
1. Sender Policy Framework (SPF)
An SPF document is one thing your organization wants to have apart out of your mail server. It’s a small piece of code to verify that an e mail despatched together with your area title is distributed straight out of your mail server. That method, you may stop your organization from turning into a supply of a spoofing marketing campaign.
As an e mail recipient, together with the SPF checker in your inbox, will make any e mail despatched from anyplace except for the actual sender ”gentle up”. In most circumstances, they’ll have a pink and yellow banner over and on prime of the e-mail. This is to warn the reader to watch out.
2. Domain Keys Identified Mail (DKIM)
This protocol does robotically what I additionally proposed you do manually with suspicious emails. Namely, it’ll create P2P encryption to check if the e-mail sender is the actual sender. If the server is spoofed, it received’t acknowledge the code and the sending of the e-mail will fail.
This is a good software if the cybercriminal has in some way managed to piggyback on the server with out getting administrative entry. In these circumstances, the straightforward encryption will utterly sever the cybercriminal’s capability to ship spoofed emails.
3. Reporting & Conformance (DMARC)
DMARC works on prime of the SPF and DKIM community. It makes one thing akin to an inventory that authenticates all domains on the community. Once it has a website within the record, it’ll check if that area is used elsewhere, making a type of passive safety for each senders and recipients.
This community additionally retains an inventory of all fraudulent or spam domains, stopping additional misuse or scams at a later date. Although it’s extraordinarily onerous to take away a website or e mail from the community, you may flag and take away it out of your inbox in the event that they actively use this service.
4. Secure/Multipurpose Internet Mail Extensions (S/MIME)
This protocol is primarily based on the MIME normal that has been round for nearly three many years. It’s a easy normal that encrypts messages and offers them a selected hierarchy. That method you may monitor them.
While its unique function is to guarantee the right individual receives an e mail, its utility has been confirmed with stopping spoofed emails from being despatched as nicely. This particularly works to stop whale phishing because it’s attainable to use it to manage hierarchies inside the corporate.
I can go into extra technical element, however something greater than this can stop to be related to what you are promoting. Next, I’ll deal with what your workers can do to keep away from e mail spoofing as a lot as attainable.

How Employees Can Avoid Email Spoofing
It’s significantly better to cease e mail spoofing on the technical facet. However, in case you can’t do this, you could additionally make sure you restrict its destructive results. You can do that by way of inside worker protocols and coaching.
The most vital half right here is nice firm tradition and communication. Most inside errors come as a result of the folks within the area don’t understand how to overtly report to their managers.
If you remedy this, the whole lot else is only a ”high quality of life” enchancment and your organization shall be roughly immune to scams. If you’re nonetheless in your method to reaching that time although, listed below are some fast options to provide help to keep away from scams.
1. Use Throwaway Accounts
When making use of to companies that you just want however don’t essentially belief, it’s finest to use the accounts as soon as after which archive them. You ought to retailer the password together with your IT tech’s password supervisor. Finally, solely give entry to a couple of key workers.
Through this strategy, even when the exterior service you utilize is compromised, nobody within the firm can entry the emails despatched from them.
If no person reads the emails, then cybercriminals have nobody to rip-off.
2. Avoid Unknown Emails
Stranger/hazard is an effective maxim no matter your age. The finest method to keep away from suspicious emails is to not discuss to strangers. Especially in corporations the place e mail communication exterior of the community isn’t frequent, this may be one of the best ways to defend your self from threat.
The situation arises if plenty of outbound e mail visitors is a part of common enterprise. In these circumstances, you could have a low tolerance for escalations the place workers ought to share any suspicious e mail with the supervisor and IT tech simply in case.
Even right here, workers ought to control any e mail requesting anybody to share private data, both from the shoppers or the corporate. They ought to then instantly escalate to somebody who is aware of the protocol in-depth and might handle it.
3. Notify the Sender
Start a separate e mail chain with the sender asking in the event that they did in truth request that data. If cybercriminals spoofed your e mail tackle, the sender will know nothing about that dialog. You’ll then alert them to the actual fact that they could be compromised.
If this can be a enterprise contact, a provider, or a buyer, you may also contact them by way of phone to examine in the event that they’re those requesting one thing by way of e mail.
Take be aware that in case you use the e-mail route, you shouldn’t copy and paste the e-mail. Type it out from reminiscence as an alternative. In that case, you’ll want to look rigorously in case you’re sending an e mail to Google or Goggle.
4. Don’t Click on Links
Most fashionable e mail operators block any hyperlinks within the e mail they discover malicious. That stated, this isn’t a foul rule to have usually. Anything vital would normally come as an attachment and also you hardly ever have a motive to click on on hyperlinks.
You might need some inside necessities for sharing supplies, however it’s significantly better to share these by way of co-working apps than to use e mail choices. These apps might be Slack, Trello, or Asana.
After all, keep in mind that phishing hyperlinks are largely powerless in case you don’t click on on the hyperlinks.
5. Google Your Emails
Googling your emails is the only method to examine if an e mail is a rip-off. It’s nonetheless very efficient although. Copy your complete contents of the e-mail and paste them into Google. If it’s a rip-off, it’ll present up within the search outcomes. If it’s official, it’ll additionally seem as a query with a solution on the discussion board of that firm.
This methodology isn’t 100% foolproof. Some scams won’t be seen but. That stated, it’s a great way to rapidly show to your self if one thing is certainly a rip-off.
Now that I’ve gone by way of the protocols and worker coaching components, it could be good to point out some third occasion software program to assist your community safety.

The Top 3 Email Security Software
The software program I’ll point out right here aren’t the one choices on the market however they’re a few of which I do know are good and comparatively accessible. As is at all times the case with cybersecurity, there wants to be a steadiness with software program. You ought to discover one to defend you with out diminishing your capability to work.
When it comes to how they work, most e mail safety software program shall be related. That stated, every may have totally different options. Here you’ll want to see if the options offered are one thing you would wish.
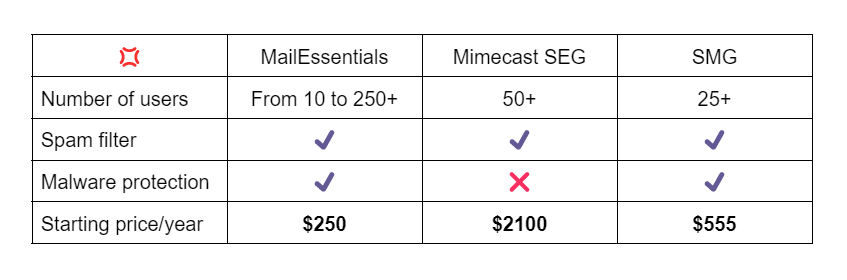
1. MailNecessities
MailEssentials is a third-party e mail safety software program that’s very highly effective and among the finest choices available in the market at present. On its personal, it provides a really thorough malware and virus record from which it’ll block assaults in addition to a spam filter.
It’ll additionally scan your despatched and obtained emails to make them protected. This means within the case of a rip-off e mail, it could want for somebody to kind out the username and password in plain textual content, which received’t occur.
The GFI MailNecessities can even join with different GFI merchandise just like the LanGuard and the HelpDesk. This can vastly enhance the interior safety of your organization’s communication.
This possibility begins at ~$250 for 10 emails for a yr or simply over $2 per thirty days per individual. It’s very cheap and even cheaper if in case you have over 250 customers.
2. Mimecast Secure Email Gateway
Mimecast goals to stop inbound threats from exterior of your organization like phishing by way of e mail spoofing. It makes use of all 4 of the protocols I’ve talked about above. It even pushes them to work tougher and wider, catching extra spam and malicious emails.
This software program has fewer built-in options than different choices. It’s nonetheless quite simple to use although and could be attention-grabbing for these corporations with out devoted cybersecurity specialists on workers.
The beginning worth for this service is $3.5 per consumer per thirty days. The worth is technically greater than the others. It’s nonetheless very accessible although in contrast to the overall costs.
3. Symantec Messaging Gateway (SMG)
SMG used to be the best choice available in the market. Now, they appear to lag behind the opposite two when it comes to their malware record. It’s nonetheless a superb alternative although. Combined with good firm tradition and coaching, it’ll immunize you from cybersecurity assaults.
The worth is $3 per consumer per thirty days, which is totally okay in case you’ve already made the expense for added coaching.
Final Words
Email spoofing is, in its essence, a quite simple idea. Cybercriminals can hack a server and faux to be another person. Alternatively, they’ll use a really related however totally different title to idiot your workers. These scams appear foolish, however they wouldn’t be so frequent in the event that they weren’t efficient. Everyone might be a sufferer.
This is why you must have 3 layers of defenses, generally known as protocols, to stop your organization from sharing its personal data with malicious entities. Next, you could have good e mail safety software program, particularly if your organization makes use of e mail repeatedly. This software program will filter out one other 9.9% and make rip-off emails barely a month-to-month incidence, even for probably the most communicative corporations.
Finally, you must arrange worker coaching for the folks that learn the emails. You must also guarantee good communication throughout the firm.
Got extra questions on e mail spoofing? Check out the FAQ and Resources sections under.
FAQ
Can massive corporations turn into victims of scams?
Yes. While not each rip-off will work on each individual, some scams will resonate with anyone. Scams enchantment to our human feelings and play on the truth that folks working are normally drained and bored. This makes them miss the apparent cues that one thing is a rip-off. As a outcome, it’s essential to embrace cybersecurity coaching in your organization.
Will opening the improper e mail compromise my system?
No. Simply opening an e mail which may have a malicious attachment or phishing hyperlink inside received’t compromise your system. That stated, clicking on these hyperlinks and attachments will. That’s why a finest apply isn’t to click on on hyperlinks despatched by way of emails. If the sender has an inquiry, message them individually. That method, you make sure the authenticity of the hyperlink.
How do I do know if somebody is phishing me?
They’ll ask for personal data. In the identical method, you realize details about your prospects, and different companies have yours. You don’t want to ship your passwords or usernames by way of e mail. No particular person individual will ever ask anybody for his or her password, banking data, or related knowledge. In that case, at all times report to somebody in your organization who is aware of the protocols.
Will my firewall cease e mail malware?
No. Your firewall will solely cease malware that straight assaults you from the web. On the opposite hand, e mail malware makes you settle for the malware. You’ll carry it in by your self. In flip, you permit it to assault the system from the within. Even with multiple firewalls, they could cease an executable file, however not non-technical phishing scams.
Do scammers know in case you open their e mail?
In most circumstances sure. Partially-hacked e mail servers would possibly use P2P encryption codes to stop this metadata from going to the cybercriminal. That stated, typically, the scammer will know in case you’ve opened their e mail and when. The aim isn’t to keep away from this however to make sure you don’t reply and confirm the e-mail as malicious.
Resources
TechGenix: Newsletters
Subscribe to our newsletters for extra high quality content material.
TechGenix: Article on Firewall Services
Learn extra about a few of the top firewall services.
TechGenix: Article on Firewall Vendor Strategy
Choosing between a single vendor and a multi-vendor strategy could be robust. Check out this text to be taught extra.
GFI: Article on Unblocking Legitimate Emails
Learn how to unblock some emails you wanted to receive in.
TechGenix: Article on Secure Email Gateways
Learn how one can secure your internal email system and manage itbetter.
TechGenix: Article on Email Defense
Learn extra about email defense and how to manage it perpetually.
https://techgenix.com/email-spoofing-guide/






