LogRhythm’s Analytic Co-Pilot Services assist clients speed up risk detection and response by guiding customers by means of the implementation and optimization of safety analytics content material and customized safety use instances.
While working intently with clients in Q2, 2022, the Analytic Co-Pilot staff found fascinating and helpful safety use instances to share. We evaluate these every quarter to recap what we’ve been engaged on and supply helpful developments we’re seeing. Some of those use instances require customized guidelines that we create from scratch, whereas others are derived from LogRhythm Knowledge Base (KB).
In this weblog, we’ll talk about a number of current safety use instances that embody user and entity behavior analytics (UEBA), endpoint risk detection, community detection, and MITRE ATT&CK methods. We’ll cowl how we deploy the use instances, in addition to tune and take a look at the foundations.
To perceive the complexity of a use case and the way it might apply to your setting, we offer a key at the beginning of every part to clarify:
- Which Module the use case aligns to
- The log sources required to efficiently implement a use case
- Difficulty rating that charges the complexity of implementing and sustaining a use case
- Impact ranking to evaluate how a use case can positively influence risk monitoring
Q2 2022 Analytic Co-Pilot safety use instances
1. Use case: Monitoring deleted and disabled person accounts
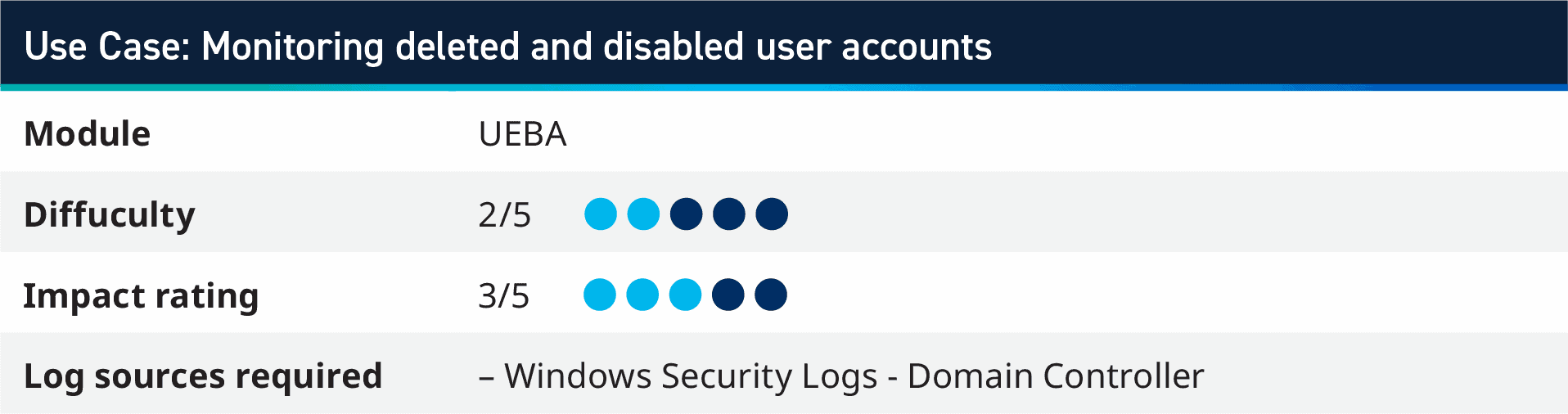
This use case is impressed from the AI Engine (AIE) rule in our UEBA Module which screens for disabled account authentication failures. Customers can leverage the bottom rule, which seems to be for an account deleted after which authentication failures inside twenty-four hours, and implement this into a few AI Engine guidelines with a report, too!
The first rule screens system logs for deleted and disabled accounts. This takes the User Impacted and provides them to a listing of Disabled/Deleted Users through SmartReponse™ automation. Optionally, SmartResponse can robotically shut the alarm, which permits for a longer-term checklist of person accounts which have been deactivated.
2. Use case: Log4Shell vulnerability monitoring
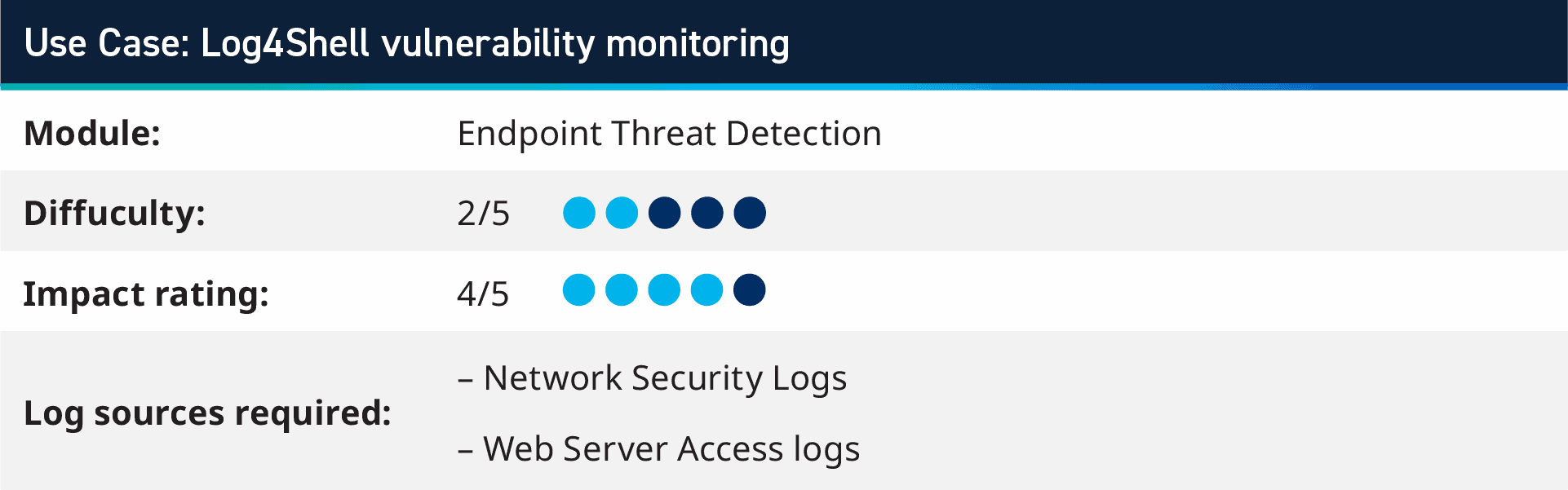
After the cybersecurity world was hit by the widespread Log4Net vulnerability, there are a number of safety use instances that the Analytic Co-Pilot staff has created to observe for Log4Shell assaults. These search for the JNDI strings inside any metadata area, in addition to encoded and obfuscated makes an attempt for delivering the payload. Customers can take the IP tackle of the supply of the assault, in addition to any IP addresses or domains which are within the payload, to observe outbound community visitors and DNS logs for these IOCs to know if there may be any execution of those assaults, both within the unique goal or downstream processing of logs.
3. Use case: Detecting a big quantity of BCC’ed recipients
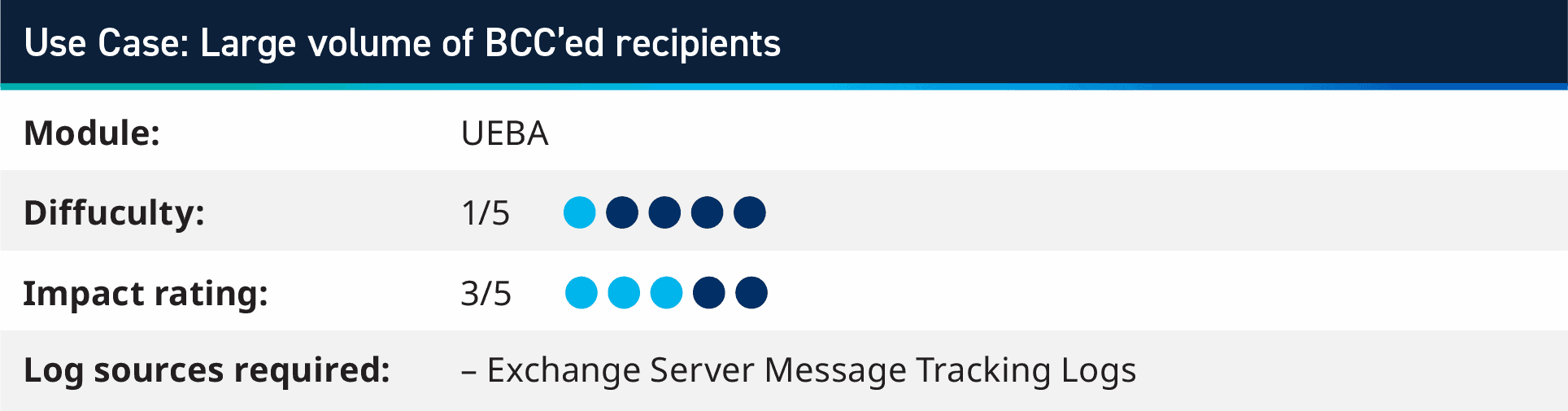
During a current session with a Co-Pilot buyer, we found that one among their customers fell sufferer to a phishing assault and their e mail was used to ship a whole bunch of spam emails. As a end result, the group’s e mail server IP addresses have been added to spam lists and legit emails weren’t obtained by the supposed recipient.
To detect this habits, we created an AI Engine rule to observe for a big quantity of recipients in BCC. This allowed their safety staff to cease a second phishing assault on a special person, pausing e mail move and remediating the person account swiftly, saving their IP addresses from being added again onto spam lists.
This may apply to “CC” and “To” fields inside an e mail being despatched; nonetheless, if these are greater in quantity, a suggestions rule will be created to observe for a similar person triggering both of those guidelines a number of occasions and inside 5 minutes.
4. Use case: DNS giant variety of DNS queries – T1071.004
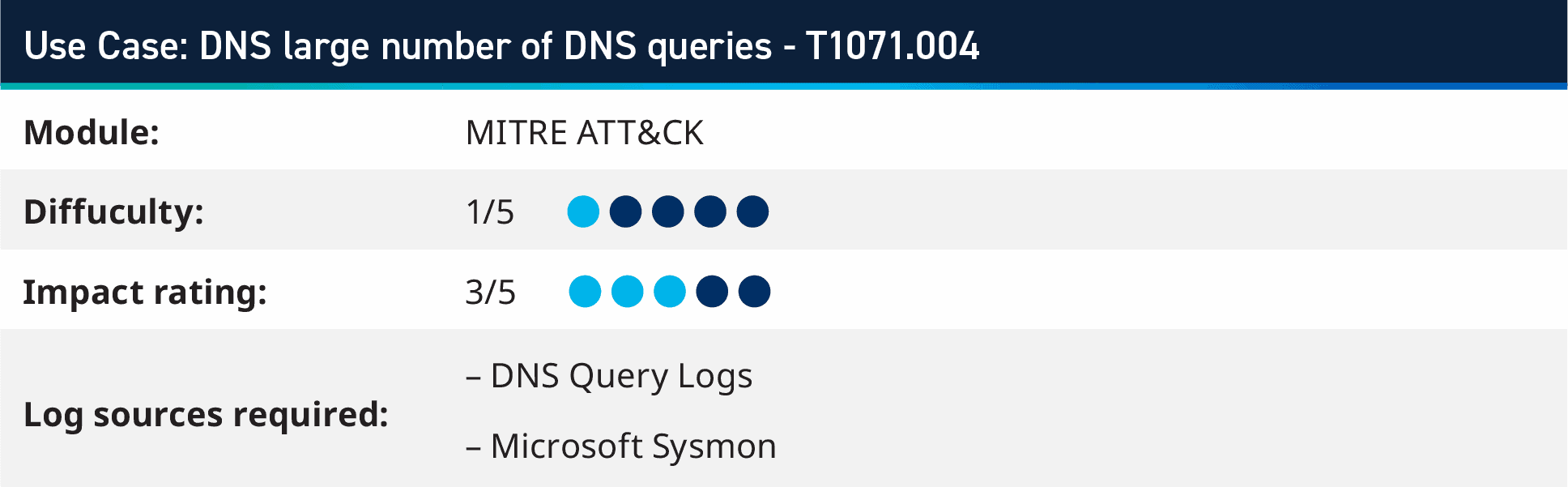
In this use case, we’ll dive into MITRE ATT&CK method T1071.004: “Adversaries might talk utilizing the Domain Name System (DNS) software layer protocol to keep away from detection/community filtering by mixing in with present visitors. Commands to the distant system, and sometimes the outcomes of these instructions, shall be embedded inside the protocol visitors between the shopper and server.”
This safety use case screens for big variety of DNS requests coming from a system. This signifies communication to a command and management system, knowledge exfiltration, or adjustments to a system configuration. By utilizing both Sysmon Event ID 22 DNS request logs from an endpoint or through the use of DNS Server question logs, you possibly can monitor for multiple hundred DNS queries inside two minutes from the identical host.
When tuning these guidelines, you need to use primary exclude filters to take away queries to your inside domains, well-known domains, and different queries which may be widespread out of your setting.
5. Use case: LogRhythm UEBA excessive rating person password change
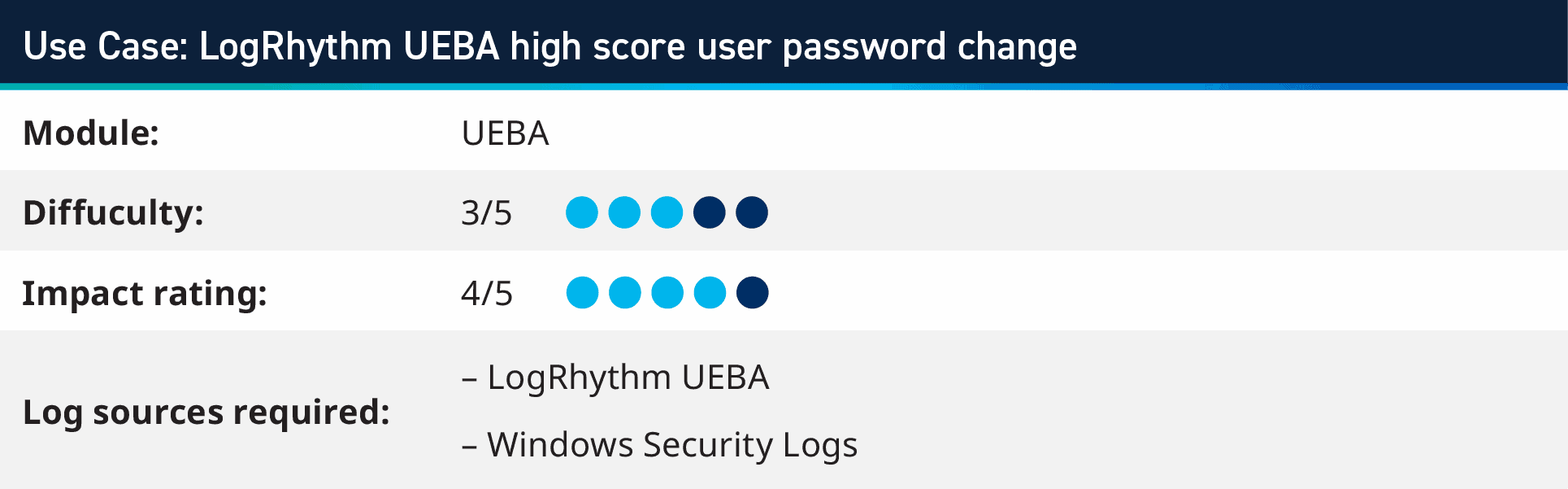
LogRhythm UEBA is a cloud-based add-on to the LogRhythm SIEM Platform that makes use of machine studying to detect person assaults corresponding to insider threats, compromised accounts, administrator abuse, and misuse. Using output from LogRhythm UEBA’s person with excessive rating alert, you possibly can mix these alerts with monitoring for different actions, which may point out greater severity confidence.
For instance, the use case combines a person excessive rating from LogRhythm UEBA with the person’s account Password Change, indicating {that a} person that has suspicious exercise has then triggered the alert, which could possibly be a nefarious actor gaining entry and altering the password to keep up long run entry. This can elevate a password change log into an alert when mixed with suspicious habits triggers.
6. Use case: DNS C2 – Command and management utilizing DNSCAT2
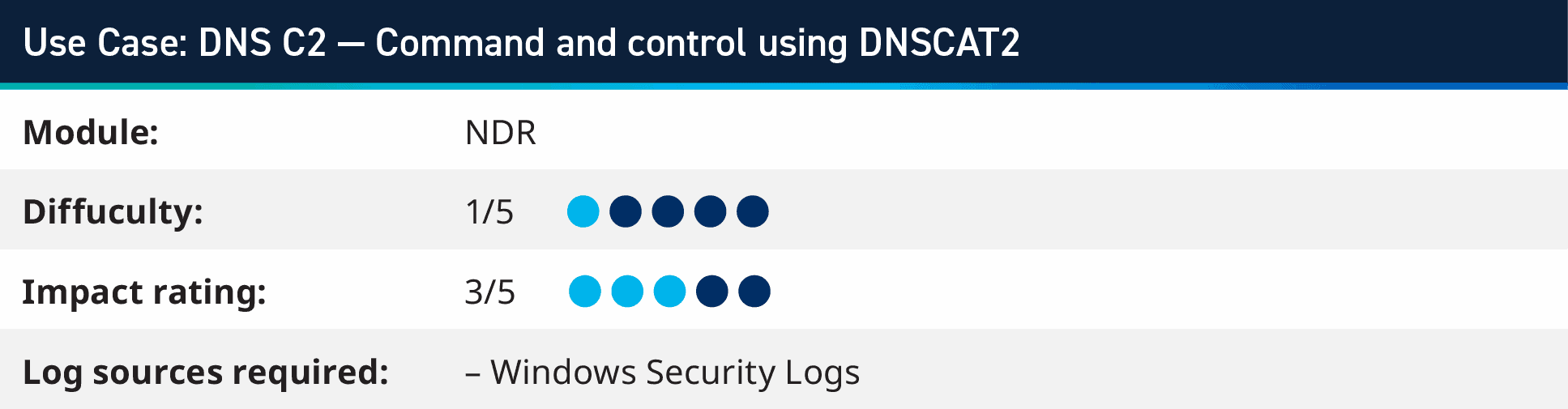
For our second DNS-based use case this quarter, we’ll have a look at how you can monitor for DNS tunneling utilizing DNSCAT2. The device makes use of DNS to ship knowledge over channels that might not be anticipated for use apart from identify decision. It works as a Client/Server mannequin, the place the server is a DNS server which will be configured to ahead up stream requests that it doesn’t need, and solely monitor the visitors for sure domains. When it receives this knowledge, it may well both export the encrypted knowledge or paperwork that it obtained (knowledge exfiltration) or return instructions to the system to be executed (tunneling).
You can monitor for this rule in two methods, the primary is utilizing encoded PowerShell (which is often how the shopper is initially executed) and the second is by monitoring for excessing NSLookup processes being began. that the DNSCAT2 shopper creates very giant variety of NSLookup processes to speak to C2 Server.
Hone your safety use instances with a Co-Pilot
Since the start of 2022, the Analytic Co-Pilot staff and our clients have noticed a number of totally different and fascinating developments, starting from world occasions influencing cyberattacks to new vulnerabilities present in open-source logging libraries that are utilized in a variety of functions inside enterprise environments.
The periods we run with our clients and the analysis we work on in our labs, ensures that clients are monitoring towards the most recent threats. We optimize their potential by serving to to tune their present setting and sustain with safety finest practices.
You can discover out extra about LogRhythm’s Analytic Co-Pilot Services here, or please attain out to your buyer success supervisor or account staff to find out how we can assist you with all issues analytics.
The submit Analytic Co-Pilot Security Use Cases appeared first on LogRhythm.
*** This is a Security Bloggers Network syndicated weblog from LogRhythm authored by Kelsey Gast. Read the unique submit at: https://logrhythm.com/blog/analytic-co-pilot-security-use-cases/
https://securityboulevard.com/2022/06/analytic-co-pilot-security-use-cases/






