You do not like having the FBI knocking in your door at 6 am within the morning. Surprisingly, nor does your typical cybercriminal. That is why they disguise (a minimum of the great ones), for instance, behind layers of proxies, VPNs, or TOR nodes.
Their IP tackle won’t ever be uncovered on to the goal’s machine. Cybercriminals will at all times use third-party IP addresses to ship their assaults.
There are numerous methods to ship cyberattacks. But one factor is widespread to all of them. The want for a pool of IP addresses to function a medium. Criminals want IP addresses to ship distributed denial of service assaults.
Criminals want IP addresses to cover behind when probing companies. Criminals want IP addresses to try brute power assaults. Criminals want IP addresses to run bot networks and companies. In a nutshell, criminals want to take care of IP addresses below their management for just about something. It is their most vital asset and is the ammo they should ship assaults.
So how do cybercriminals get their hand on these notorious IP addresses, and what does this price them? Here are some examples.
“admin/admin”
Hijacking machines and extra particularly networks of IoT gadgets. Poorly secured and managed fleets of IoT gadgets left with default entry credentials and outdated firmware are the proper goal for that. Easy method to zombify a lot of gadgets, freshly served for DDoS assaults…hey “sensible” safety cameras…we’re watching you!
“VPS are low-cost”
Take any cloud supplier, fireplace up some situations, set up bots to scan & try Log4j injections. At a restricted price, you’ve your bot community to scan targets for vulnerabilities. Of course, sooner or later, you’ll get flagged or the supplier may catch you. But you may replicate your method with cloud suppliers in different international locations, possibly much less relating to the utilization of these VPS…
‘Into darkness”
They can even go to the grocery store for criminals, aka. “darkish internet” and purchase a community of bots to ship assaults like DDoS for a few hundred {dollars}. Script kiddies, welcome.
Two take-aways from these approaches :
Acquiring IP addresses, though not unattainable, prices cash, time, and sources. Tamper with that, you tamper with a felony’s skill to do his job effectively. Ban recognized IPs utilized by criminals and you may simply drastically enhance the safety of your on-line property.
Those bots and scan automation actions generate a number of web background noise. Imagine all these numerous botnets scanning the IP area for various nefarious functions. This is well-known by SOC analysts as “alert fatigue”, which means, this generates a considerable amount of information, with out much-added worth, however that analysts nonetheless must take note of.
But excellent news everybody, there are answers to make life tougher for cybercriminals.
IP status is a part of the answer. Suppose customers can preventively consider the chance of an IP connecting to a service. In that case, it may possibly lock out recognized malicious customers and make sure that these IPs cannot damage anybody anymore, de-facto taking away the IP tackle pool criminals hung out and cash to construct.
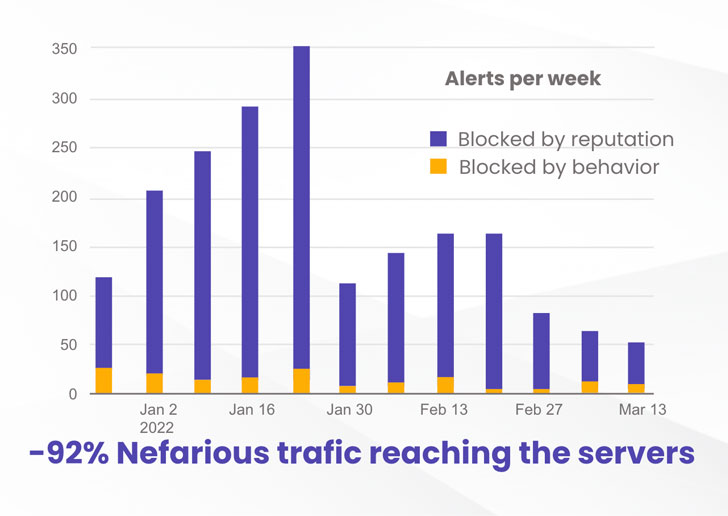
At CrowdSec, we did enjoyable experimenting: we arrange two equivalent VPSs on a well known cloud supplier, with two easy companies, SSH and Nginx. Nothing fancy, identical to hundreds of thousands of machines on the market within the wild. CrowdSec was put in on each to detect intrusion makes an attempt. Still, one machine had the remediation agent (IPS), receiving IP status data from the CrowdSec neighborhood (day by day 1 million indicators shared) and preventively banning flagged IPs.
The outcome was fairly beautiful.
Thanks to the neighborhood blocklist, the machine with the IPS preventively blocked 92% of the assaults in comparison with the machine with out the IPS. That is a notable enhance in safety degree.
You can learn extra in regards to the methodology and detailed outcomes at: https://crowdsec.net/
 |
| Source: crowdsec.internet |
Community IP blocklists – with the earlier curation – deal with each challenges.
It cripples criminals by nullifying their IP tackle pool. They hung out, cash, sources to construct them, and we, as a neighborhood, merely take them away within the blink of a watch. Take that scum!
But it additionally makes the lifetime of analysts and cybersecurity specialists a lot simpler. By preventively blocking these nefarious IPs, the background noise is considerably decreased. We are speaking about decreasing by 90% the alerts that must be analyzed by SOC folks. That is way more time to concentrate on extra vital alerts and subjects. Alert fatigue? – bye-bye.
If you want to partake within the greatest IP status neighborhood and hunt nefarious IP addresses whereas successfully defending your on-line property, be a part of us at crowdsec.internet
https://thehackernews.com/2022/03/of-cybercriminals-and-ip-addresses.html






