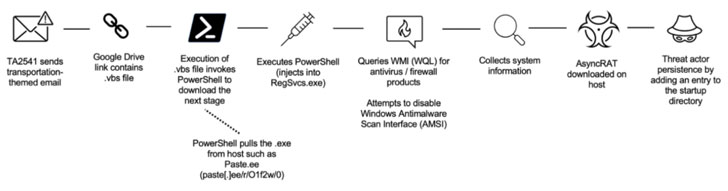
Entities within the aviation, aerospace, transportation, manufacturing, and protection industries have been focused by a persistent menace group since at the very least 2017 as half of a string of spear-phishing campaigns mounted to ship a range of distant entry trojans (RATs) on compromised methods.
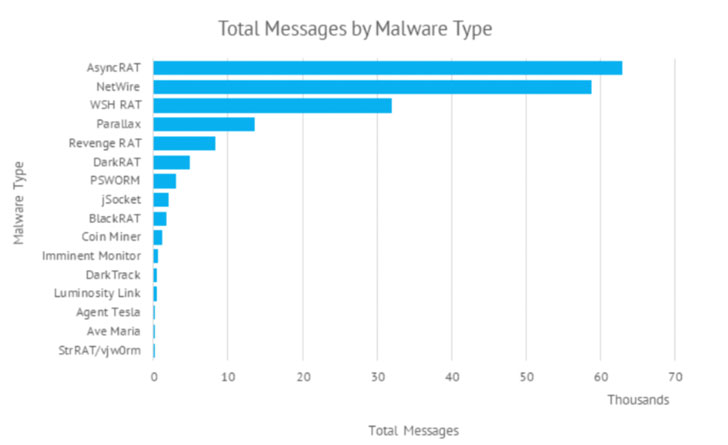
The use of commodity malware corresponding to AsyncRAT and NetWire, amongst others, has led enterprise safety agency Proofpoint to a “cybercriminal menace actor” codenamed TA2541 that employs “broad focusing on with excessive quantity messages.” The final goal of the intrusions is unknown as but.
Social engineering lures utilized by the group doesn’t depend on topical themes however quite leverages decoy messages associated to aviation, logistics, transportation, and journey. That mentioned, TA2541 did briefly pivot to COVID-19-themed lures within the spring of 2020, distributing emails regarding cargo shipments of private protecting tools (PPE) or testing kits.
“While TA2541 is constant in some behaviors, corresponding to utilizing emails masquerading as aviation corporations to distribute distant entry trojans, different techniques corresponding to supply technique, attachments, URLs, infrastructure, and malware kind have modified,” Sherrod DeGrippo, vice chairman of menace analysis and detection at Proofpoint, informed The Hacker News.
While earlier variations of the marketing campaign utilized macro-laden Microsoft Word attachments to drop the RAT payload, current assaults embrace hyperlinks to cloud services internet hosting the malware. The phishing assaults are mentioned to strike a whole bunch of organizations globally, with recurring targets noticed in North America, Europe, and the Middle East.
The repeated use of the identical themes apart, choose an infection chains have additionally concerned the use of Discord app URLs that time to compressed recordsdata containing AgentTesla or Imminent Monitor malware, indicative of the malicious use of content material supply networks to distribute info gathering implants for remotely controlling compromised machines.
“Mitigating threats hosted on professional companies continues to be a troublesome vector to defend in opposition to because it possible includes implementation of a sturdy detection stack or policy-based blocking of companies which could be business-relevant,” DeGrippo mentioned.
Other methods of curiosity employed by TA2541 embrace the use of Virtual Private Servers (VPS) for his or her electronic mail sending infrastructure and dynamic DNS for command-and-control (C2) actions.
With Microsoft saying plans to turn off macros by default for internet-downloaded recordsdata beginning April 2022, the transfer is anticipated to trigger menace actors to step up and shift to different strategies ought to macros develop into an inefficient technique of supply.
“While macro-laden Office paperwork are among the many most often used methods resulting in obtain and execution of malicious payloads, abuse of professional internet hosting companies can also be already widespread,” DeGrippo defined.
“Further, we frequently observe actors ‘containerize’ payloads, utilizing archive and picture recordsdata (e.g., .ZIP, .ISO, and so forth.) which can also affect capability to detect and analyze in some environments. As all the time, menace actors will pivot to make use of what’s efficient.”
https://thehackernews.com/2022/02/experts-warn-of-hacking-group-targeting.html