PKI digital signatures could be discovered just about in all places — from digitally signed emails and software program to safe web sites. We’ll break down what a PKI signature is and the way it helps shield your information’s integrity
Remember whenever you had been a child and your dad and mom informed you that when you put your thoughts to it, you are able to do or be something you need? Well, on the web, that’s type of true. You can just about make your individual reality about your self — you could possibly be a youngster, an grownup, or an organization’s CEO. Without a method to show your claims are respectable, nobody might be any the wiser.
Cybercriminals know this and like to benefit from it. That’s why we now have all the problems that we do at this time referring to phishing different kinds of predatory cyber assault methods. Before the web, you needed to meet up with somebody head to head to securely trade data or ship coded, encrypted messages.
But now that persons are speaking and doing enterprise with others internationally instantaneously, face-to-face meetups are now not possible usually. So, to guard your self and your clients, it’s essential have a method to show your identification on-line and assist folks know that your emails, information, and software program are respectable and haven’t been faked. This is the place PKI signatures come into play.
But what’s a public key signature? How is a digital signature completely different from different digital signatures? And the place can you discover PKI digital signatures in motion?
Let’s hash it out.
What Is a Public Key Signature? A Simple PKI Digital Signature Definition & Analogy
Before we will dive head-first into the nitty-gritty of public key signatures, it will be sensible to a minimum of briefly recap what a digital signature is in addition to the position it performs in public key infrastructure (PKI). After all, you’ll be able to’t run the play when you don’t know the principles.
A PKI signature is a type of verifiable digital identification that helps you show you (or one thing you create) is actual. In a means, it’s type of like a fingerprint as a result of it’s one thing that uniquely identifies you. However, it’s greater than “simply” identification. A digital signature is a means on your group to affirm its legitimacy via the usage of a digital certificates (similar to a code signing certificates) and a cryptographic key.
In a nutshell, utilizing a PKI digital signature lets you connect your verifiable identification to software program, code, emails, and different digital communications so folks know they’re not faux. This helps you:
- Prove your identification so you are able to do issues that require licensed entry (authentication)
- Assert your group’s digital identification so folks know you’re you and never an imposter (non-repudiation) utilizing the signature and different instruments (similar to timestamping), and
- Protect and show the authenticity of your messages, information, connections and information (information integrity).
If that every one appears a bit sophisticated, let’s break this down with extra of a easy analogy…
A Public Key Signature (PKI Digital Signature) Is the Wax Seal of Internet Communications

A PKI signature is the fashionable equal of a wax seal that individuals traditionally would use to safe delicate communications. Before the web or the invention of the phone, folks would both meet up in individual or talk remotely through written letters. Of course, with out digital communications, these messages must be delivered by hand — through prepare, boat, or horseback riders — which signifies that these messages could possibly be intercepted on their method to their meant recipients.
Say, you need to ship a delicate message to a pal. You’d need to have a method to allow them to know that you simply signed it and that the message hasn’t been tampered with in any means. Years in the past, you’d use a wax seal to attain this. This course of would entail:
- Melting some wax,
- Pouring it on the envelope, urgent your private seal (i.e., stamp) into the wax, and
- Giving the wax time to harden.
When your pal receives your message, they’ll see that the wax seal intact. This unbroken wax seal signifies that your message is respectable in two essential methods:
- The crest proves your identification as a result of try to be the one one with that stamp. Sealing the message along with your particular person crest lets the recipient know that you simply’re the one who sealed the message.
- The unbroken wax seal means nobody altered the message in transit. This lets your pal know that the message’s integrity has been protected and that nobody altered it because you despatched it.
In a lot the identical means, communications on the web additionally have to have these similar kinds of protections. While they’re not being despatched by horseback, digital communications pass through a lot of “hands” as they transmit throughout the web within the type of servers, routers, and different intermediates till they attain the precise vacation spot. This signifies that cybercriminals would have many alternatives to change or manipulate your data in transit if there wasn’t a means for the recipient to confirm the message’s integrity.
Here’s an incredible video from Computerphile that helps to elucidate PKI digital signatures in one other means:
PKI Digital Signature vs Electronic Signature
People usually mistakenly conflate PKI digital signatures and digital signatures as being the identical, however that’s not fairly true. Yes, a digital signature is a kind of digital signature, however not all digital signatures are digital signatures. It’s type of like how all iPhones are smartphones however not all smartphones are iPhones. Sure, they each are a method to say you’re somebody on the web, however solely one in all them (*cough*PKI signature*cough*) can truly assist you to show your identification as a result of it’s greater than simply an internet signature that may be altered.
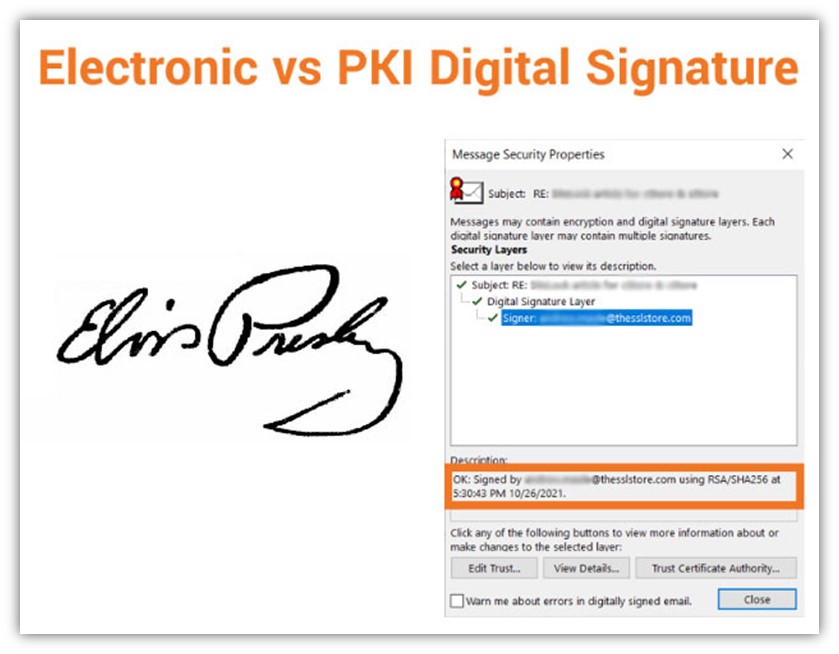
It’s type of like getting an autograph of your favourite athlete — like, say, quarterback Tom Brady. (Sorry, Pats followers, Tom is ours now! #TampaBayBucs) Sure, you could possibly simply stroll as much as Tom at a bar and ask him to signal one thing. But with out having some method to authenticate that his signature is actual — like, say, an official certificates of authenticity — then somebody may argue that anybody may have signed his title.
Or, for all they know, you actually may have gotten Tom to autograph one merchandise. But what would cease you from sitting at dwelling on the weekends, utilizing his signature for example in an effort to forge his autograph on a bunch of Buccaneer’s group gear that you simply need to promote? Well, nothing, until your potential patrons had a method to confirm the autograph’s legitimacy.
This is type of just like the distinction between an digital signature and a digital signature:
- An digital signature is signing your title in an digital format. Instead of placing a bodily ink-writing pen to paper, you’re signing your title utilizing digital means.
- A PKI digital signature is sort of a certificates of authenticity. In this fashion, a public key signature is a means so that you can signal one thing in order that others can confirm:
- You, because the respectable individual or group consultant, truly signed the e-mail, file, or software program, and
- The merchandise you signed hasn’t been modified or tampered with because you signed it.
Two Cryptographic Processes Are Integral to the Digital Signing Process
To actually get on the coronary heart of understanding public key signatures, it’s essential find out about two cryptographic processes that play pivotal roles of their creation: encryption and hashing.
Encryption
This cryptographic course of takes a mathematical algorithm and applies it to plaintext (readable) information to “scramble” it into an unreadable state. It can use:
- a single key to encrypt information and decrypt information (symmetric encryption), or it may use
- two separate keys (uneven encryption) to do the identical.
As you’ll be able to see, there are some key variations (excuse the pun) between asymmetric and symmetric encryption. Regardless of these variations, the method is, primarily, reversible (utilizing the decryption key), which signifies that encryption is a two-way operate.
In digital signatures, encryption is used to particularly encrypt the hash information to create the digital signature. (It doesn’t encrypt the file or e mail you need to digitally signal — it solely encrypts the hash worth.)
Hashing
Hashing is a cryptographic operate that additionally applies a mathematical algorithm to information and information. However, its function is completely different than an encryption algorithm — a hashing algorithm takes information of any size and maps it to an output (hash worth) of a particular size. For instance, you’ll be able to take a single sentence or a whole e book, apply a hash function to it, and the end result might be an output (hash worth) of the identical size.
Because the method isn’t reversible, there’s not a key that reverts or maps the hash worth again to the unique enter. This signifies that hashing is a one-way cryptographic operate. (You know… as a result of hashing solely works in a single path.)
5 Uses for a Public Key Signature
In reality, digital signatures could be discovered all throughout the web. For instance, you need to use digital signatures within the following functions:
1. Enabling HTTPS on Websites
A website security certificate, or what’s often called an SSL/TLS certificates, is without doubt one of the most central elements of safety on the web. Installing this certificates in your server lets you safe your web site utilizing the safe HTTPS protocol. Enabling HTTPS signifies that every time clients connect with your web site, their particular person connections (and any information they share throughout their session) might be secured utilizing encryption. This is what makes that nifty little padlock icon seem in your browser.
A digital signature is part of what’s often called the TLS handshake (or what some folks nonetheless name the SSL handshake). We received’t get into the entire specifics right here, however the first a part of the handshake entails the web site’s server and person’s browser exchanging data (together with the server’s SSL/TLS certificates and digital signatures) through an uneven encrypted connection. Using a digital signature helps the server show that it’s the respectable server for the web site you’re making an attempt to go to.
2. Signing Digital Documents to Prove Their Legitimacy
A document signing certificate lets you apply your digital signature to many kinds of paperwork, together with Microsoft Office paperwork and PDFs (relying on the particular certificates you employ). Here’s a fast instance of what a digital signature appears like:
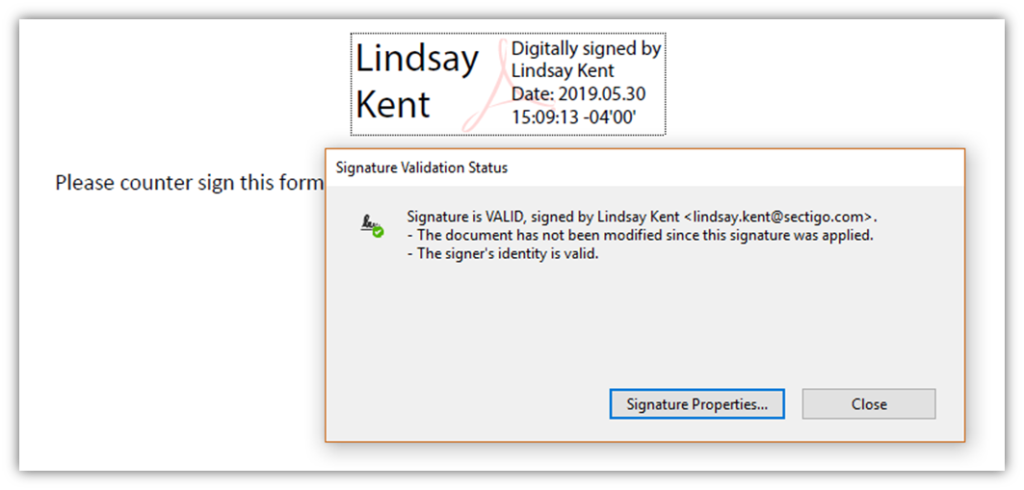
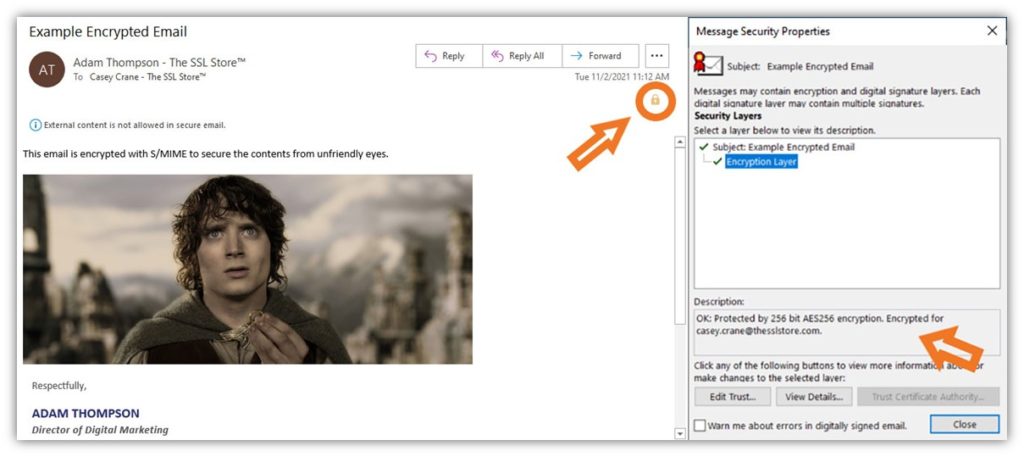
Using an e mail signing certificates (i.e., an S/MIME certificates) means that you can apply your digital signature to your emails. This offers identification assurance and protects the integrity of your communications.
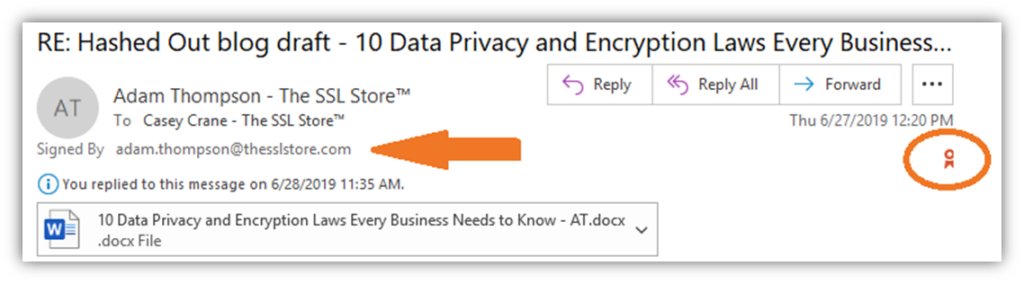
Note: For further safety, you can too use this certificates to ship encrypted emails (to customers who additionally use e mail signing certificates). This offers safe, end-to-end encryption that protects your information each whereas it’s bouncing between servers and routers and sitting in your recipient’s e mail server.
4. Securing Your Software and SaaS Supply Chain
Using a code signing certificate lets you shield your provide chain. It additionally provides assurance to customers who obtain your software program that your software program is each respectable and unmodified.
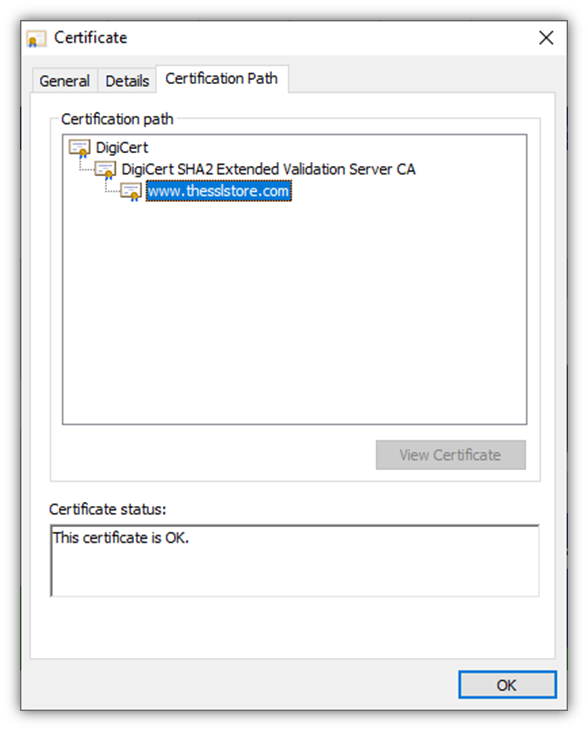
When you signal your certificates utilizing a code signing certificates, you’ll show your verified firm group data (as proven within the screenshot on the precise):
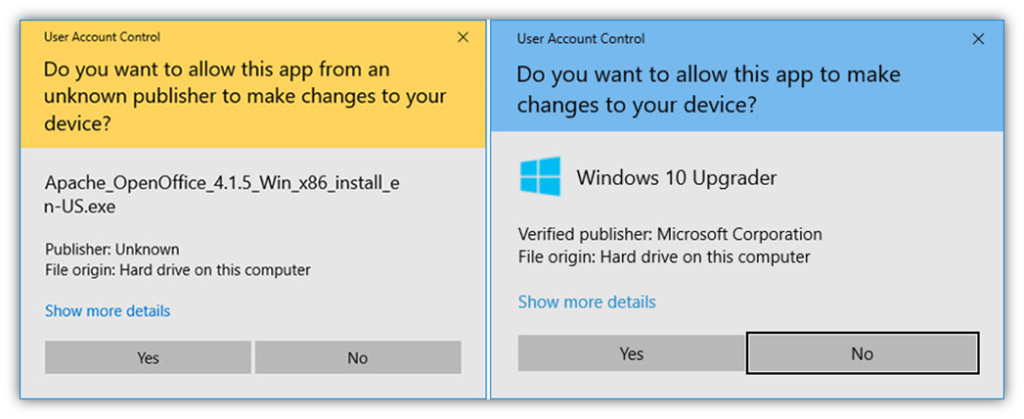
Of course, unsigned (and software program signed utilizing normal code signing certificates) can even set off Windows SmartScreen warning messages as effectively — the distinction could be that digitally signed software program would show the verified writer data as a substitute of “Unknown writer.”
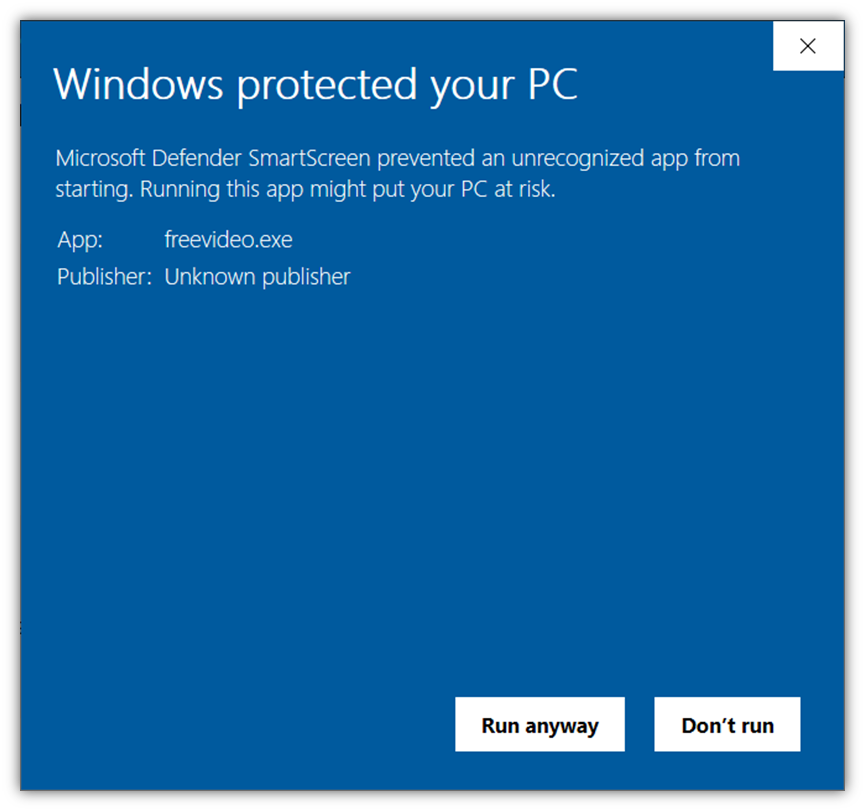
To keep away from displaying Windows SmartScreen messages, make sure to signal your software program, code, and different executables utilizing an extended validation code signing certificate. Using this PKI digital signature ensures Microsoft and its browsers routinely belief your software program.
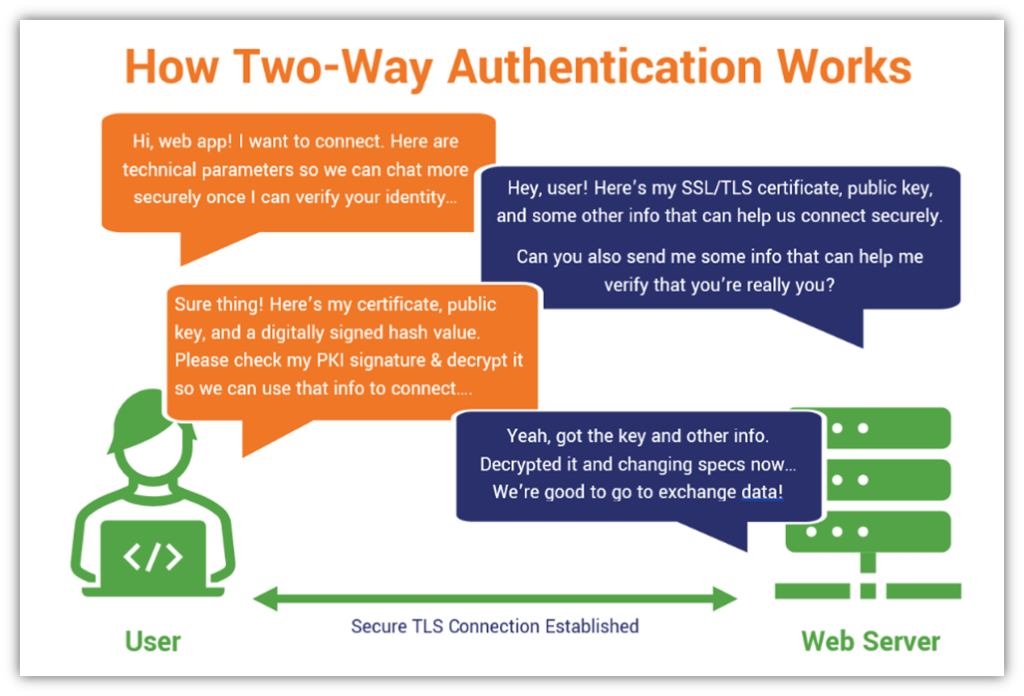
5. Enabling Secure, Two-Way Authentication (Mutual Authentication)
Remember the SSL/TLS handshake that we talked about earlier? Well, in two-way authentication, or what’s often called mutual authentication, each the server and the shopper show their identities to at least one one other. This signifies that along with the server offering its data to the shopper, the shopper should do the identical by offering data to the server.
This data features a generated hash worth, digital shopper certificates, and cryptographic public key. The shopper generates the hash utilizing information it exchanges with the server and encrypts the fastened size string utilizing its personal key (which is mathematically associated to the general public key it shares).
Here’s a primary overview of how this course of works:
Why Using a Public Key Signature Matters to Your Business & Customers
Public key signatures are important in an internet-oriented world. As more companies are moving to the cloud and counting on this public community to conduct enterprise and supply companies, the roles of identification and integrity in safety grow to be extra vital.
Of course, we’ve talked in regards to the explanation why it’s so vital at size in a earlier article. Be positive to take a look at our article on why you should use digital signatures to sign everything. But we’ll shortly summarize the important thing causes right here for you about why digital signatures matter:
- Attaches your identification to your software program or communications. The greatest means to assist customers know whether or not your software program or communications are respectable is by giving them a method to confirm your identification.
- Helps you shield your provide chain. If you’re a software program developer or writer, one of many worst issues that may occur is it somebody makes use of your provide chain to assault clients whereas impersonating you. By signing your software program or different executables, you’re offering a means for customers to confirm whether or not your code is respectable or if it’s been altered after it was signed.
- Protects your group’s popularity. If you’ve a verifiable method to show that you simply’re genuine and your merchandise or information are reliable, potential clients usually tend to need to do enterprise with you.
Wrapping Up Public Key Signatures (TL;DR)
Thanks to all of you who’ve caught via this text to get up to now. For these of you who’ve determined to skip to the tip for the “too lengthy; didn’t learn” portion of our article, welcome. We know your time is valuable, so right here’s a fast overview of what we’ve lined on this article so you’ll be able to skim and head out in your means.
- A digital signature is the fashionable wax seal for delicate communications.
- Organizations use digital signatures to claim their identification and make sure the integrity of their communications, information, software program, and connections. Simply put, PKI signatures:
- Identifies you as you (and never an imposter).
- Provides verification methods to assist show that the message got here from you (i.e., not another person).
- Protects the integrity of your communications and information so recipients comprehend it’s respectable (not faux).
- Public key signatures are a kind of digital signature (however that doesn’t imply all digital signatures are digital signatures).
- PKI digital signatures depend on public key infrastructure and cryptographic elements like certificates and keys.
All of that is to say that this cryptographic approach is all about serving to firms show their authenticity and giving customers a method to confirm that information, software program, and different data haven’t been manipulated or altered since they had been digitally signed.
Stay tuned subsequent week for a associated article that can break down how digital signatures work.
https://www.thesslstore.com/weblog/public-key-signature/





