The web site safety panorama is as difficult as it’s treacherous. We typically take care of purchasers who grow to be reinfected over and over. Once the attackers set up a foothold in an surroundings and acknowledge {that a} web site is weak, you’ll be able to assure that they are going to be again to attempt to reinfect the web site.
Our web site firewall is designed to guard web sites from assault and an infection, however there are various totally different ways in which attackers set up their presence right into a compromised surroundings. A web site firewall is however one side in a bigger defense in-depth technique to guard your web site!
In this submit I’ll evaluation some of these different assault vectors and a few ways in which web site homeowners can defend their websites from changing into reinfected.
First, let’s evaluation how our internet utility firewall (WAF) works
Our firewall service acts as a reverse proxy. Essentially, it sits between the net server and acts as a form of “gateway” for the visitors coming to your web site. At its core it’s a fairly simple idea: block dangerous visitors, enable good visitors. Attacks comparable to SQL injections, cross web site scripting (XSS) and DDoS assaults will get blocked by our generic guidelines. Any identified exploits towards weak web site software program comparable to plugins, themes and core recordsdata also needs to be blocked. However, our firewall is a really difficult product with so much of totally different options! Let’s check out some of them:
Our firewall is designed to be platform agnostic. That is, it’s going to work with any CMS platform. It doesn’t matter in case your web site is utilizing WordPress, Magento, Joomla, OpenCart or any of the opposite CMS platforms accessible on the internet; our firewall can be utilized to guard your web site from assaults.
Different CMS platforms range enormously from each other and work in very alternative ways. Since it’s not particular to any platform, the essential firewall guidelines that apply throughout the board have to be generic sufficient to not intervene with the routine operations of regular web site visitors. So, out-of-the-box it needs to be tailor-made to your web site and the CMS it’s primarily based on to enhance safety!
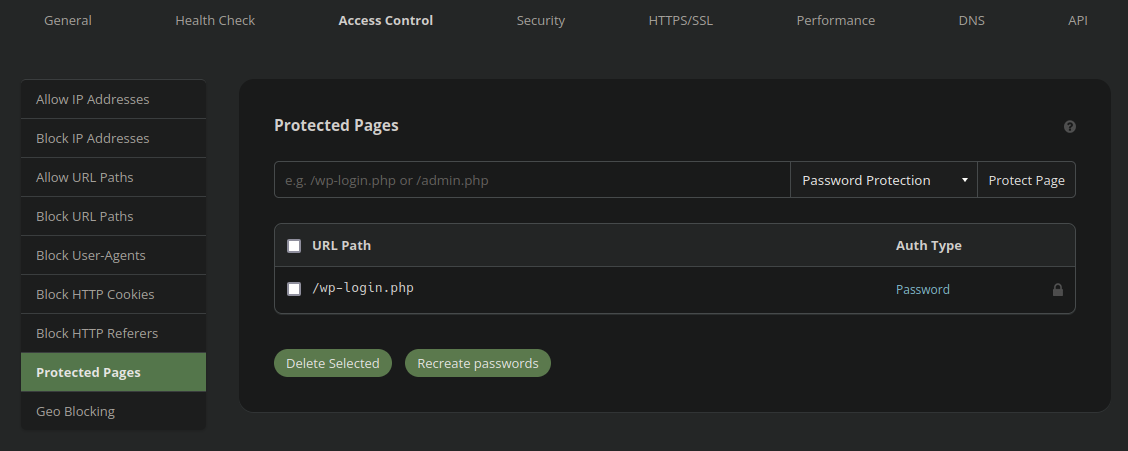
Different CMS platforms have totally different admin panel URLs and the firewall must be configured to work along with your web site. Firewall choices like the next:
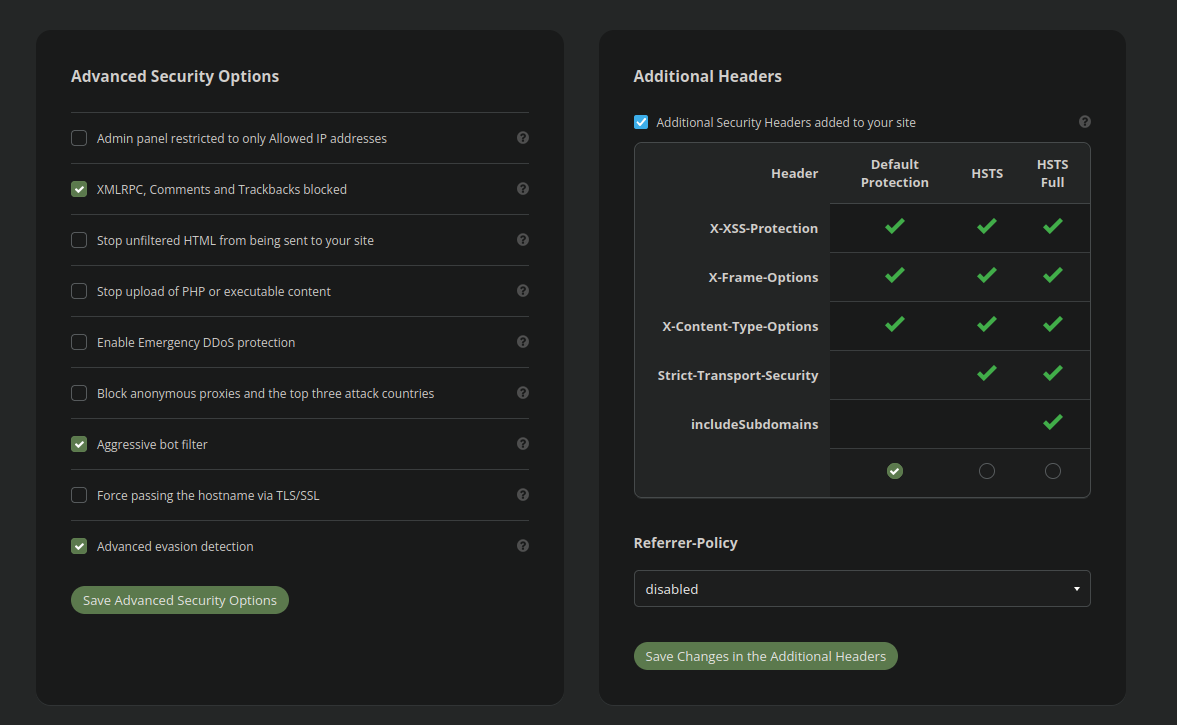
Admin panel restricted to solely Allowed IP addresses
Are not enabled by default for that reason. If you need the firewall to enhance the safety of your admin panel the URL needs to be added into the entry management settings:
Moreover, in case your web site incorporates a weak add type or skill to add probably malicious content material, then this must be enabled manually as properly within the superior safety settings:
Stop add of PHP or executable content material
You and/or your web site developer ought to evaluation the safety and entry management settings throughout the firewall configuration to find out essentially the most sturdy configuration that isn’t going to intervene with regular operations. If you aren’t certain how to do that, you’ll be able to all the time submit a product assist ticket and our analysts are glad to help you with figuring out the optimum configuration on your web site!
Exploring Different Attack Vectors
Websites may be attacked in many various methods. Not all malicious visitors goes to return by means of the firewall itself. Most notably, assaults can goal the internet hosting IP itself, however there are various different facets to the assault floor for a median web site.
Bypass Prevention
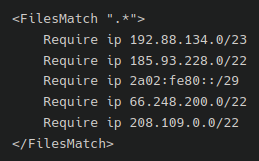
One of essentially the most ignored facets of our firewall is the presence of bypass prevention. Without including some customized guidelines to the web site’s .htaccess or NGINX configuration file the attackers can circumvent the firewall by attacking the host IP instantly (whether it is identified). We want to make sure that all visitors coming to the web site is being filtered by our firewall service. To try this this guide may be adopted, or you’ll be able to submit a ticket to our analysts to configure that for you!
Admin Panel Attacks
Attacks on web site admin panels are tremendously frequent. By default admin login panels on CMS platforms are open to the world and at excessive threat of brute force attacks. Unless some third celebration safety plugin or extension is put in on the web site attackers won’t face any difficulty making an attempt hundreds of passwords till they break their manner in. It is one of the commonest assaults that we see.
Many privilege escalation vulnerabilities have been discovered prior to now. These enable low-level “subscriber” accounts to maliciously execute “administrator” capabilities. Some vulnerabilities enable attackers to execute administrator operations with none account in any respect. It is essential to maintain all plugins, extensions and parts updated in order that your web site has minimal probability of being weak on this manner.
Our firewall ought to block these varieties of vulnerabilities, however we of course nonetheless suggest maintaining your surroundings totally patched and updated.
It can also be quite common for attackers to go away behind “rogue” admin accounts. This permits them to reinfect the web site even after the malware is cleared from the web site surroundings. These accounts should be eliminated within the wake of a compromise.
Our web site firewall can go to nice lengths to assist defend your admin panel from abuse. As I discussed earlier on this submit, the firewall safety and entry management settings needs to be tailor-made to your particular web site for optimum safety. We even have a WordPress hardening guide that covers some of the ways in which WordPress web site homeowners might help hold themselves secure even with out our firewall.
Insecure Hosting Environments
Let’s check out some of the totally different ways in which the internet hosting surroundings itself (slightly than the web sites) can lend itself to a compromise.
FTP/SFTP/SSH
Even the presence of firewall bypass prevention will not be going to forestall assaults on the server itself, nonetheless. Most internet servers enable for both FTP, SFTP or SSH visitors normally by way of ports 21/22. Most typically this visitors is not restricted by way of IP tackle and is open to the world. This locations these accounts in danger of brute drive assaults and may be compromised, notably if the passwords are weak. A compromised FTP/SFTP/SSH account will present the attackers with full management over the file construction and database.
Exactly how this visitors is dealt with varies from internet hosting supplier to internet hosting supplier. Typically they’d have some safety software program comparable to mod_security to assist stem attackers, however no safety is ideal. Some hosts require you to “unlock” FTP for a sure interval of time, or enable solely sure IP addresses to entry the server utilizing this methodology, however they’re a small minority. Most typically these community protocols are open to the world with none management from the internet hosting supplier.
Make certain that each one FTP or SFTP accounts have sturdy passwords. Ideally, the server needs to be restricted to solely SSH key authentication and restricted to solely allowed IP addresses. This is markedly safer than any password might ever be. However, relying in your host this is probably not attainable. If your web site is hosted on an unmanaged Virtual Private Server (VPS) then the server safety lands in your lap.
Cross-Site Contamination
One of essentially the most frequent assault vectors that we run into is cross-site contamination. This is when a number of web sites share the identical internet hosting house. Using the default configuration settings in lots of environments will enable web sites to contaminate one another and can all be as insecure because the weakest hyperlink. A single poor password on a single wp-admin panel can result in a complete surroundings falling sufferer to a malware assault!

Insecure cPanel environments
Many web site directors haven’t one however many web sites. These are sometimes all configured as Addon Domains inside a regular cPanel interface.
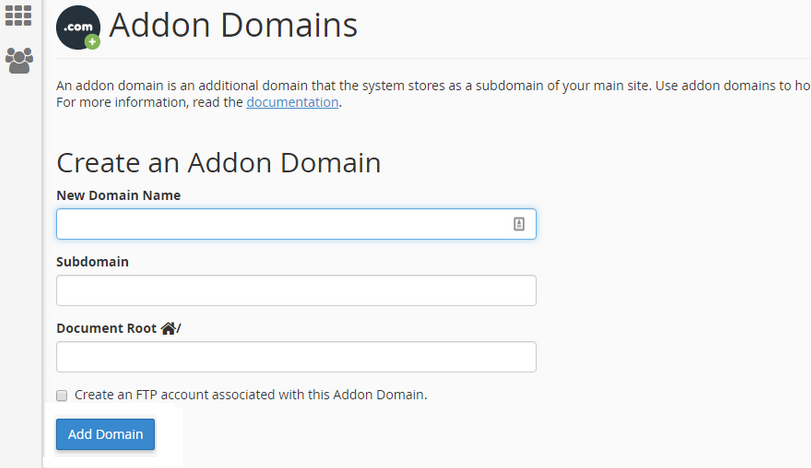
This is a well-liked manner so as to add extra web sites to your internet hosting plan as a result of it’s straightforward, handy and (most of all) low cost! However, that is simply essentially the most insecure technique to host a number of web sites. The downside with this configuration is that the web site recordsdata for web site A are going to be owned by the identical person:group as web sites B and C. The underlying PHP course of may even run as the identical person.
What does this imply? It implies that if one web site is contaminated then there’s a big threat that malware will unfold to all the opposite web sites hosted in the identical cPanel. If web site A is protected by our firewall however web sites B and C should not then web site A can nonetheless simply get contaminated.
If you’re utilizing cPanel with a number of web sites, ideally these needs to be configured inside WHM to every have their very own separate, remoted cPanel surroundings.
Which brings us to our subsequent assault vector…
Insecure WHM Environments
Another difficulty that we regularly see is cross web site contamination by means of insecure WHM environments. Namely, WHM servers that should not have symlink safety enabled.

The default choice for symlink safety is for it to be disabled. Enabling symlink safety will trigger a modest efficiency lower on the server however the safety advantages far outweigh this price. Having this selection disabled renders your entire surroundings in danger of cross contamination, whether or not or not the file possession and permissions are configured appropriately and even when every web site has a separate cPanel occasion. The cause being is that attackers can transfer laterally by means of the community by way of the use of symbolic hyperlinks. Some extra aggressive infections (for instance, the infamous AnonymousFox hack) particularly goal this and actively exploit whole environments to unfold malware, phishing and spam.
Compromised cPanel Account
We have seen some slightly aggressive assaults that rapidly reinfect cPanel environments. The manner that they do that is quite simple however efficient!
If an attacker has write entry to the recordsdata (ie: a compromised wp-admin administrator account with default WordPress settings) then they’ll edit the next recordsdata:
- .cpanel/contactinfo
- /residence/
/.contactemail
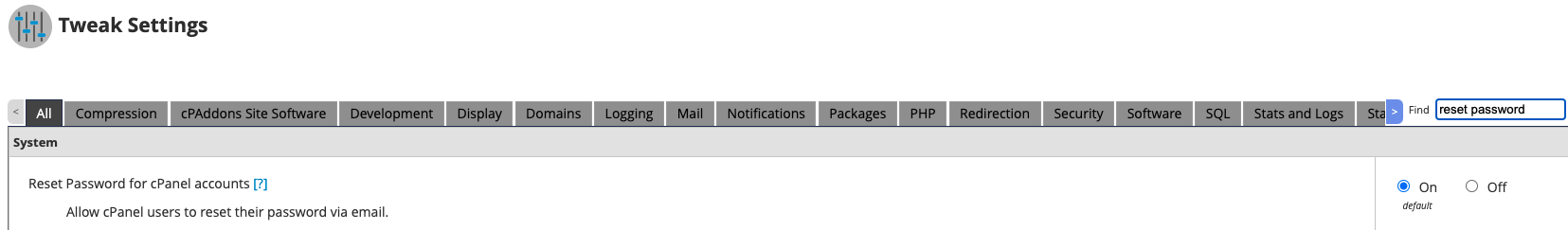
And place their very own e-mail inside. Once that’s achieved all they should do is request a password reset by way of e-mail and voila! They’ve compromised your entire cPanel.
To preserve a safe WHM surroundings we suggest disabling password reset by way of e-mail totally!
Compromised Hosting Provider Account
Hosting accounts should not proof against compromise both, notably if the password is weak or if two issue authentication (2FA) will not be enabled. Most hosts present a file supervisor kind utility to can help you instantly edit and modify recordsdata throughout the web site surroundings. This could be very helpful for routine web site administration and configuration, however like the rest, may also be misused by attackers to unfold malware.
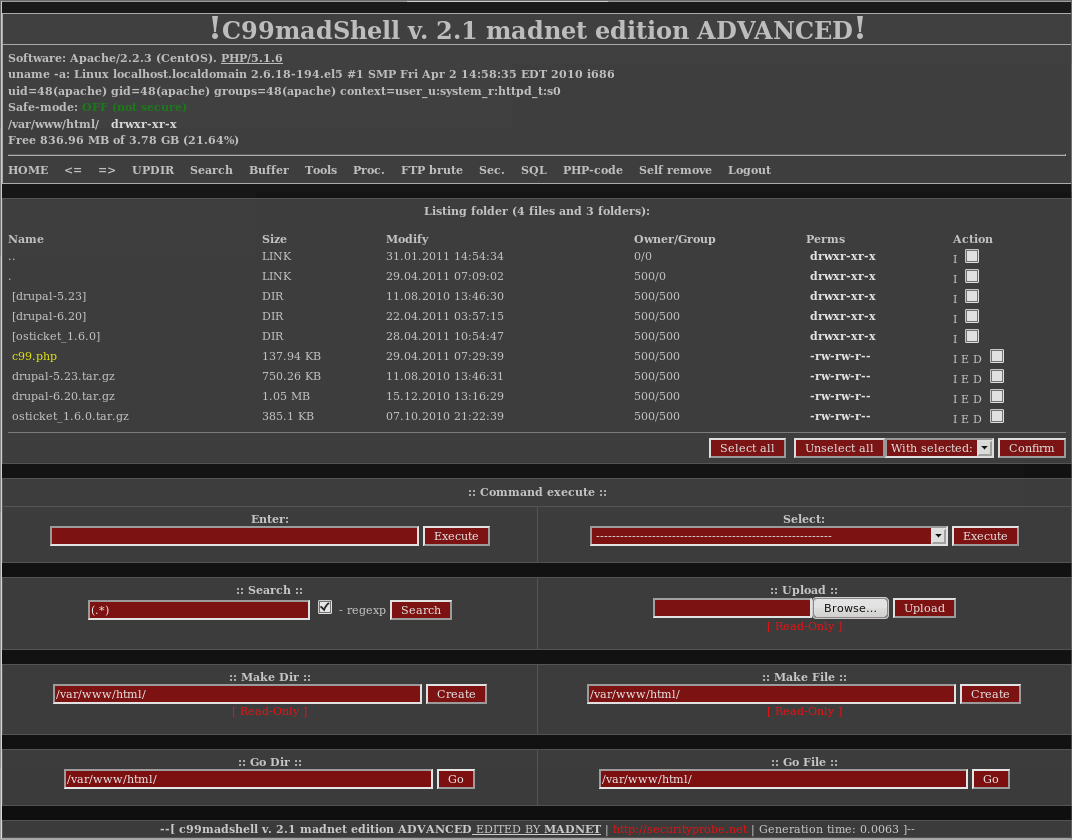
If your internet hosting supplier account is compromised, the attackers can simply log in remotely and have full management over the surroundings. Most probably the attackers would begin by importing a webshell since their performance far exceeds what most hosts present to their purchasers.
Insecure Hosting Provider
Most internet hosting suppliers do an excellent job of sustaining their server safety. They are likely to have a devoted safety crew ensuring that each one safety patches and updates are put in to their servers and to make sure that the file/listing person:group permissions are all above board.
In some cases, nonetheless, we have now seen internet hosting environments which have been fully misconfigured to provide internet hosting accounts write entry to all different internet hosting accounts on the server. Sometimes this has been a misconfiguration within the file construction. Other instances, it’s a misconfiguration within the database software program. In both case it has led to repeated web site compromises that had nothing to do with the web site homeowners themselves in any respect.
Compromised Server
While fortunately uncommon, some exploits found prior to now enable for full, distant takeover of a webserver on the root stage. For instance, in late 2019 a crucial vulnerability was found in Exim, the default mail server software program utilized in WHM and cPanel environments. This exploit allowed for each native and distant root-level privilege escalation. Many servers the world over, notably poorly maintained VPS servers, have been affected by this obvious flaw on the server backend. This left many web site homeowners questioning how they have been hacked within the first place.
Other Vectors of Compromise
Not all assault vectors are instantly associated to the web sites and even the internet hosting surroundings. Let’s discover another facets of the assault floor!
Compromised Workstation or Browser
Another assault vector is the pc that you’re sitting at this very second!
If a pc that’s used to handle your web site turns into compromised then it’s totally attainable for the attackers to make use of it as a reinfection vector. For instance, if a keylogger trojan is put in into your workstation then it doesn’t matter what number of instances you modify your web site password, the attackers will all the time have the ability to authenticate into the surroundings. This is one of many explanation why enabling two issue authentication (2FA) in your administrator panel is extremely beneficial.
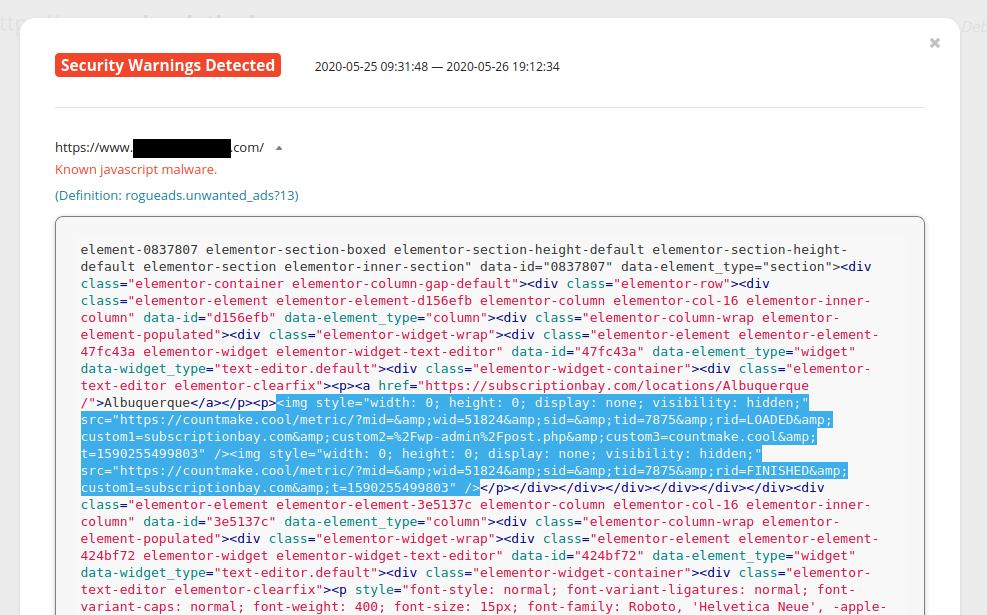
Malicious third celebration browser extensions have additionally been identified to insert malicious javascript into WordPress posts and pages whereas the web site administrator is logged into the admin interface and dealing on their web site content material.
Remote Database Administration
Most host environments don’t enable for distant database administration, however there have definitely been cases the place it has been enabled. This is especially true of VPS servers that haven’t been configured correctly.
Most typically the database can solely be modified by means of connections on the internet hosting server itself. However, if distant database administration is enabled this will enable the attackers to:
- Brute drive the database password
- Remotely inject malware into the database
Sometimes internet purposes do require distant database administration. For instance, in case you want to enable purchasing cart or guestbook purposes on different servers to entry your databases. Typically, solely the required IP tackle can be added to the enable checklist to do that. However, like all helpful options, attackers may also abuse this by including their very own IP tackle to the enable checklist in the event that they’re capable of compromise the cPanel account. This can later be used to reinfect the web site surroundings.
Compromised Repository
This will not be as frequent on web sites that use primarily open supply code comparable to WordPress. However, it’s definitely not out of the realm of risk {that a} software program repository might be compromised and unfold malware to any web sites that deploy code from it.
It’s additionally value mentioning that many extensions web site homeowners use on their web site are premium; that’s to say, not open supply and require cost to make use of. This software program is developed by non-public firms and we have now no manner of figuring out what goes on behind their closed doorways, what their safety insurance policies are, or even when a compromise occurred in any respect.
Nulled/Hacked Bootleg Extensions
To proceed on the subject of compromised extensions or different software program, this leads me to the subject of nulled/hacked extensions. Some premium extensions price a good bit of cash and never all web site homeowners have the revenue to shell out for sure software program extensions. Instead of simply utilizing fully open supply options some web site homeowners take the naughty shortcut of downloading pirated variations of these plugins to make use of on their web site.
As we have now explored on our weblog prior to now this software program almost always comes pre-loaded with backdoors, spam or different unwelcome friends.
Security Misconfiguration
Exposed delicate recordsdata may also end in an internet site compromise. Certain recordsdata in CMS installations include delicate info like database credentials comparable to the next:
WordPress: ./wp-config.php Joomla: ./configuration.php Magento1: ./app/and so forth/native.xml Magento2: ./app/and so forth/env.php Drupal: ./websites/default/settings.php Laravel Framework: ./.env
It’s not unusual for web site homeowners to create backups of these recordsdata on the server with names comparable to:
./wp-config.php.bak
This is a grave error because it exposes the database credentials to the world. Files with the .bak extension should not handled as PHP recordsdata and will likely be viewable in plain textual content to anyone poking round in locations they shouldn’t be!
Phishing
Most typically phishing assaults are looking for banking info, Facebook or Netflix logins. However, we have now additionally seen phishing assaults that try to steal internet hosting account login info.
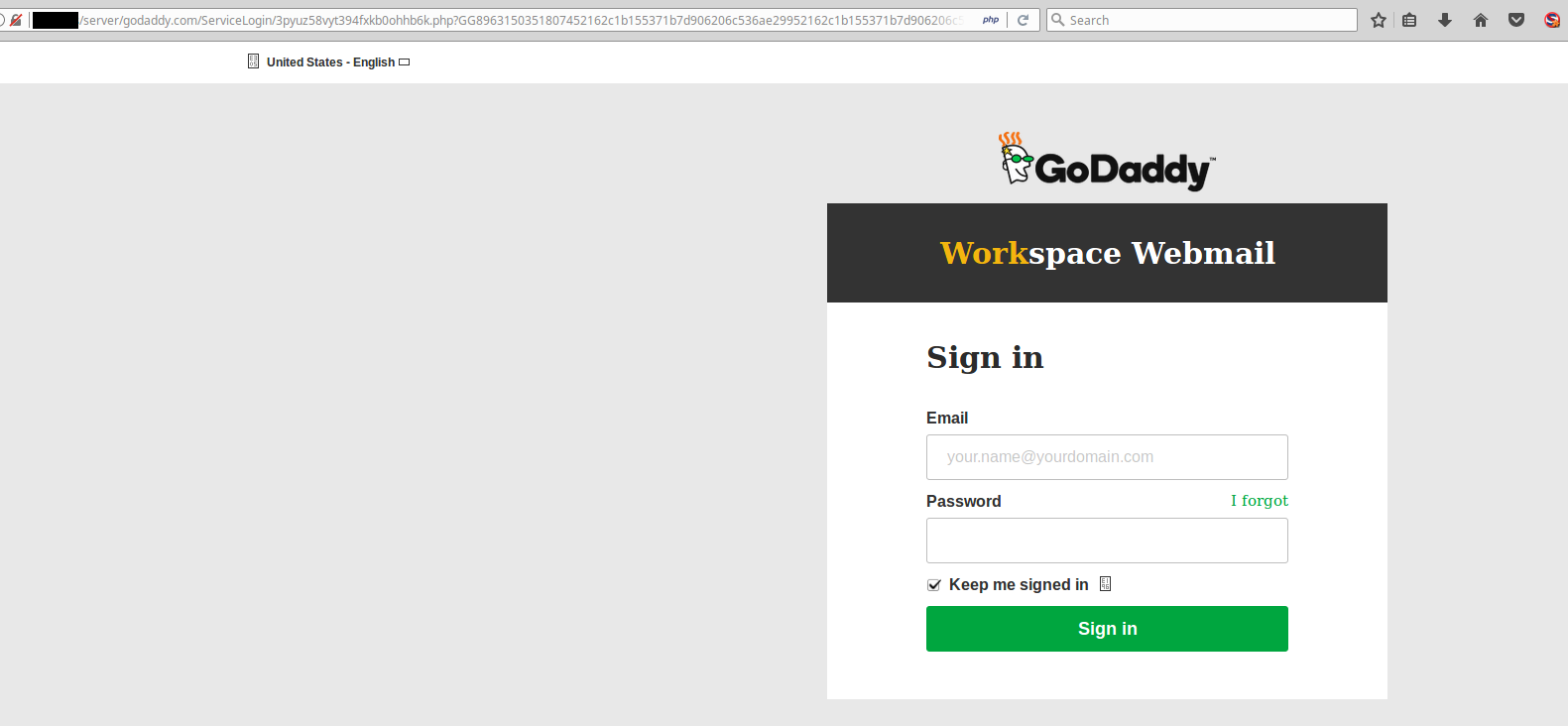
This will not be the official GoDaddy web site!
Thankfully, many internet hosting suppliers (and banks!) have taken the step of enabling two issue authentication (2FA) by default. This prevents any unauthorized person from logging into your account with out bodily entry to your cell system. This is a superb step ahead, though not all internet hosting suppliers have this characteristic enabled and even accessible.
Zero Day Exploit
And lastly, now and again the invention of a zero day exploit happens within the wild. This is when a model new vulnerability is found in a bit of software program for which there isn’t a accessible patch but.
Depending on the sort of exploit, our firewall might block it. For occasion, SQL injections and cross web site scripting assaults needs to be blocked it doesn’t matter what. However, some extra unusual varieties of assaults might require the writing of a brand new firewall signature to dam it. These new firewall guidelines have to be written by our engineers and undergo high quality assurance (QA) testing earlier than they’re deployed to our servers.
Security is an everlasting recreation of cat and mouse between the defenders and attackers.
In Conclusion
As we have now seen laid naked on this article: Website safety is a sophisticated beast! There are many transferring elements and the assault floor is broad to say the least. A web site firewall is a wonderful addition to any web site proprietor’s safety roster, however it ought to by no means be thought-about a panacea.
A correct on a regular basis safety posture can also be an essential process to be saved in thoughts to attempt to stay as secure as possible.
Remember, of us: There isn’t any such factor as a superbly safe system. Anybody who claims in any other case is both a liar or a idiot.
https://securityboulevard.com/2021/11/an-overview-of-website-reinfection-vectors/





