The emergency patches for the lately disclosed important vulnerabilities in Microsoft Exchange electronic mail server did not come soon enough and organizations had little time to arrange earlier than en masse exploitation started.
Named ProxyLogon, the bug has been exploited within the wild even earlier than Microsoft obtained the vulnerability report, giving attackers a two-month head begin to breach targets earlier than safety updates grew to become obtainable.
Vulnerable servers are scorching targets for a large spectrum of risk actor teams in search of an preliminary foothold right into a community for espionage or monetary functions. Nation-state adversaries, ransomware gangs, and cryptomining actions have already exploited ProxyLogon.
With patches launched and proof-of-concept (PoC) exploit code surfacing on-line, 1000’s of Microsoft Exchange servers worldwide proceed to stay susceptible and the variety of assaults continues to be at a worrying degree.
ProxyLogon risk discovered
On December 10, 2020, DEVCORE researcher Orange Tsai found CVE-2021-26855, a important server-side request forgery (SSRF) flaw that permits bypassing authentication in Microsoft Exchange.
DEVCORE named the bug ProxyLogon and, on the finish of December, Tsai discovered a second one (CVE-2021-27065) that may very well be used to realize distant code execution.
The researcher on January 5, 2021, forwarded to Microsoft a report together with an exploit chaining the 2 flaws to show the validity of his findings.
APT teams had a two-month benefit
The identical month, risk intelligence and incident response firm Volexity detected ProxyLogon attacks aiming to compromise networks or to steal electronic mail information.
Closer examination decided that “cyber espionage operations utilizing the SSRF vulnerability CVE-2021-26855 started occurring on January 3, 2021,” two days earlier than DEVCORE submitted the report back to Microsoft.
In January, a number of cybersecurity firms detected assaults towards on-premise Exchange servers in consumer environments utilizing zero-day vulnerabilities.
The community of not less than one FireEye buyer was breached that month and the intruder created internet shells for persistence entry and distant code execution, and the exercise “urged exploitation of CVE-2021-26858,” the company said.
Dropping internet shells (ASPX recordsdata) can also be what Volexity noticed, adopted by credential dumping, including consumer accounts, stealing copies of the Active Directory database (NTDS.DIT), and lateral motion on the community.
Also in January, Danish incident response agency Dubex investigated exercise on Exchange servers that used a zero-day (CVE-2021-26857) exploit to put in writing internet shells to disk, itemizing a set of three ASPX recordsdata among the many indicators of compromise (IoCs).
On March 2, Microsoft released updates for Exchange Server and knowledgeable of “a number of 0-day exploits getting used to assault on-premises variations of Microsoft Exchange Server in restricted and focused assaults.”
Microsoft attributes the incidents to a state-sponsored group named Hafnium that operates out of China and exploited the next vulnerabilities earlier than a patch was obtainable:
Hafnium, which may have compromised 68,500 Exchange servers by the point patches had been obtainable, is just not the one APT group that leveraged the bugs above earlier than the patches got here out.
ESET stated that different actors – Tick, LuckyMouse, Calypso, Winnti, Websiic – lots of them China-linked, had been actively exploiting them since not less than February 28 and really helpful organizations to look for suspicious ASPX files.
“This means that a number of risk actors gained entry to the main points of the vulnerabilities earlier than the discharge of the patch, which suggests we can discard the likelihood that they constructed an exploit by reverse engineering Microsoft updates” – ESET
MSP risk detection supplier Huntress Labs analyzing a couple of hundred compromised Exchange servers additionally discovered that some had been hacked days earlier than Microsoft launched the patches, on February 27.
Threat actor used DEVCORE’s exploit
One of the exploits used within the wild earlier than the patches arrived is identical chain that DEVCORE submitted to Microsoft on January 5 as a part of the accountable disclosure.
DEVCORE confirms this in an replace on the ProxyLogon website, noting that it started to analyze after Volexity reported lively exploitation of the SSRF bug.
“Regarding the a number of assaults that Volexity talked about on January third [sic], we are not conscious of when our exploit was used within the wild,” DEVCORE advised BleepingComputer.
“After studying that ProxyLogon exploit has been utilized by HAFNIUM from the exploitation advisory from Volexity and the weblog put up from Huntress, DEVCORE instantly launched an inner investigation on March third to confirm whether or not the crew has been hacked or any data has been leaked from our finish.”
DEVCORE advised BleepingComputer {that a} thorough examination of non-public computer systems and units of its workers, and its infrastructure and programs confirmed no indicators of hacking, indicating that the leak could have occurred someplace else.
“Also, we have investigated our inner system and discovered no uncommon login makes an attempt or file entry” – DEVCORE
According to a report from Wall Street Journal, Microsoft is presently investigating whether or not certainly one of its companions that had entry to the data leaked it deliberately or by chance.
Most safety software program suppliers are half the Microsoft Active Protections Program (MAPP), which provides them early entry to vulnerability data so they can replace protections for his or her clients faster.
A large spectrum of attackers
Once official patches got here out, even for unsupported versions, susceptible Microsoft Exchange servers straight uncovered on the web grew to become a good hotter goal as risk actors might reverse engineer the updates to construct an exploit.
ESET noticed greater than 10 APT groups rushing to attack unpatched devices. Many had been operating cyberespionage operations, and this record consists of Mikroceen and Tonto Team, however not all.
The researchers observed exercise from a gaggle they name “Opera” Cobalt Strike that exploited the Microsoft Exchange vulnerabilities to put in the Cobalt Strike penetration testing product that’s frequent to some high-profile ransomware gangs.
In one other occasion, ESET noticed an adversary dropping internet shells to “set up so-called IIS backdoors.” Activity attributed to the DLTMiner [1, 2] cryptomining botnet was seen on servers that had been focused utilizing the ProxyLogon vulnerabilities.
The DLTMiner botnet reveals similarities in infrastructure and habits with one other cryptocurrency botnet known as Lemon_Duck, whose infrastructure has been documented in IoCs for hacked Exchange servers.
Security professionals at Shadowserver noticed yesterday more than 8,000 IP addresses that confirmed indicators of DLTMiner exercise, most of them in China and the U.S.
Ransomware additionally jumped in and started to compromise Microsoft Exchange server utilizing the ProxyLogon vulnerabilities. BleepingComputer broke the story on the night of March ninth a couple of new piece of file-encrypting malware known as DearCry utilized in assaults on Exchange servers.
PoCs and assault instruments
Starting March 10, PoC exploit for the massively exploited Exchange vulnerabilities started to look on-line. The first variant was a buggy distant code execution exploit that Microsoft rapidly pulled from GitHub to forestall abuse at a good bigger scale.
A new ProxyLogon PoC emerged over the weekend, rising the possibilities of even low-skilled attackers to go after susceptible Exchange servers, which are possible within the 1000’s.
Furthermore, there may be loads of data to breed the ProxyLogon exploit by reverse-engineering the official patches from Microsoft. Cybersecurity agency Praetorian revealed a blog with full technical particulars to create a working end-to-end exploit.
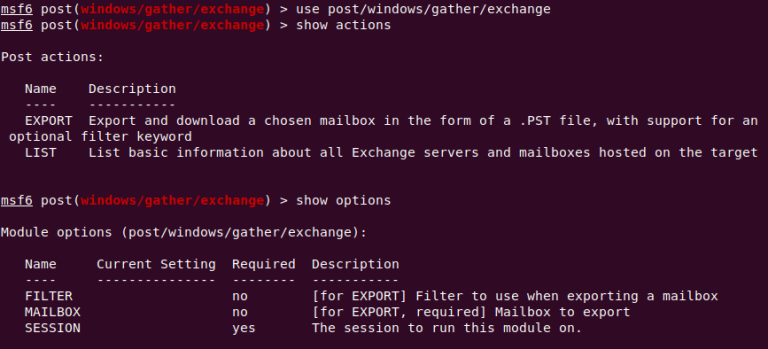
SophosLabs created a device known as metasploit_gather_exchange that may extract all of the contents of an inbox as a PST file. It doesn’t assist hack Exchange servers however is supposed as a post-exploitation tool for pink crew penetration take a look at engagements.
Plenty of unpatched Exchange servers round
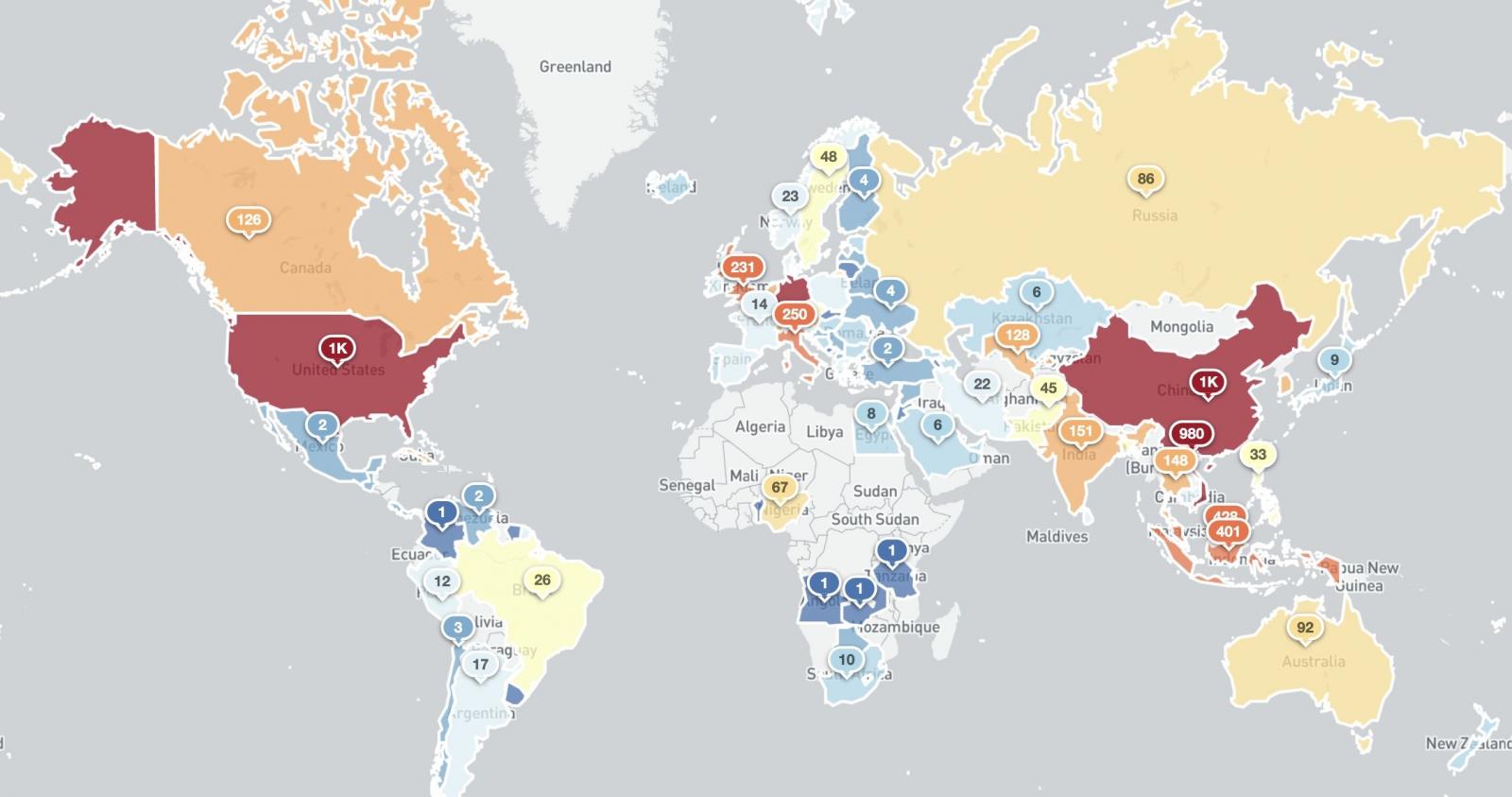
Victor Gevers, the chair of the Dutch Institute for Vulnerability Disclosure, advised BleepingComputer on Friday that there have been about 64,000 susceptible Microsoft Exchange servers world wide.
A report from Shadowserver in the present day, which mixes information from KryptosLogic, reveals that on Sunday, the variety of probably susceptible Microsoft Exchange servers on the earth was 59,218.
These figures are smaller than the 80,000 that Palo Alto Networks recorded in web scans between March 8-11 utilizing its Expanse platform, possible due to the excessive patch charges for Microsoft Exchange.
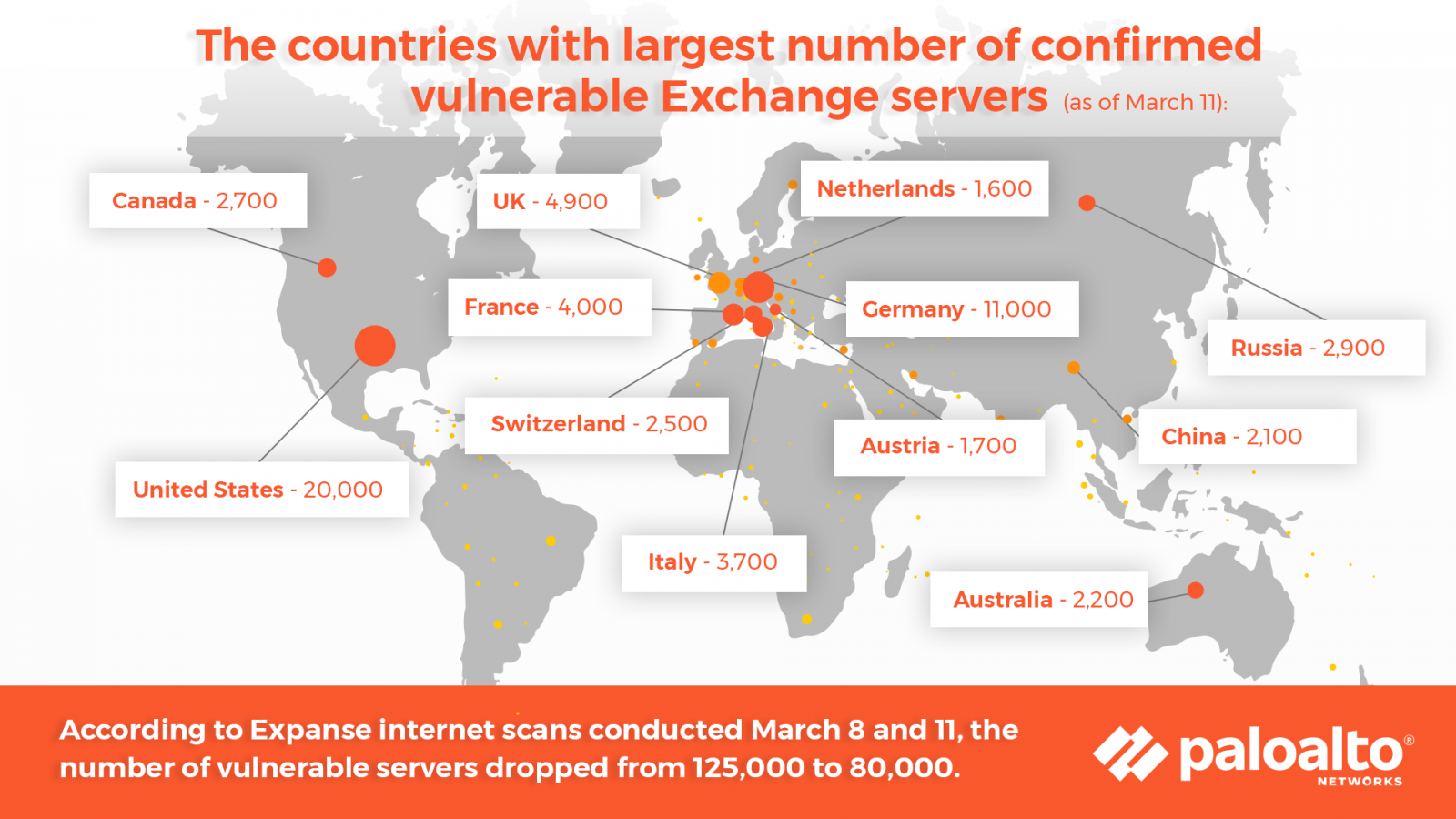
Matt Kraning, Chief Technology Officer, Cortex at Palo Alto Networks, stated that organizations operating any model of Exchange ought to “assume they had been compromised earlier than they patched their programs” due to the large exploitation that started in January.
Even if the servers are not going through the general public web, firms ought to replace them to defend towards actors that may very well be on the native community.
Mandiant vice-president of research, John Hultquist, is anticipating extra exploitation of the ProxyLogon vulnerabilities quickly from ransomware gangs, which can discover the assault vector “notably enticing” as a result of it makes for “an environment friendly technique of gaining area admin entry.”
“That entry permits them to deploy encryption throughout the enterprise. In instances where organizations are unpatched, these vulnerabilities will present criminals a quicker path to success” – John Hultquist
Kaspersky has additionally warned concerning the excessive threat of ransomware an infection and the information theft hazard related to these assaults. Since Microsoft launched the patches, the corporate has seen “an elevated quantity of automated makes an attempt at mass exploitation of latest Exchange vulnerabilities.”
An organization consultant advised BleepingComputer that they’re anticipating the variety of assaults to develop till most customers set up the updates.
“It appears that the actors behind these assaults are making an attempt to compromise as many organizations as doable. It is but to be uncovered how they will attempt to use the entry sooner or later” – Kaspersky
According to Check Point Research, hackers hold making an attempt to take advantage of ProxyLogon, with assaults rising greater than ten occasions over the previous 4 days. Since Thursday, the corporate noticed the number of attempts grow from 700 to 7,200 in the present day.
On Friday, UK’s National Cyber Security Centre (NCSC) stated that greater than 3,000 electronic mail servers within the nation had been susceptible and that malware had been detected on 2,300 of them.
Tools and data of the commerce
With all of the hacking starting greater than two months in the past, many Exchange servers could have already been compromised by the point they get the updates.
CISA has revealed seven Malware Analysis Reports to its alert with mitigations for the Microsoft Exchange Server vulnerabilities. Each of them gives particulars a couple of webshell utilized in assaults to offer adversaries distant administration on the system.
Many cybersecurity firms strongly suggest checking for indicators of compromise earlier than putting in the patches. For this goal, Microsoft added signatures to Microsoft Defender to detect web shells put in after exploiting the vulnerabilities.
The identical will be achieved utilizing the moveable Microsoft Support Emergency Response Tool (MSERT), which robotically deletes any detected recordsdata with out quarantine.
Administrators may use a PowerShell script to test if Exchange servers had been hacked utilizing the ProxyLogon vulnerabilities. It automates a set of commands that will also be run manually to check both one or all on-premise servers.
Dubex recommends checking Exchange and Internet Information Services (IIS) logfiles for identified IoCs [1, 2, 3, 4, 5, 6] and the hosts for indicators of internet shells/hashes, IoCs in identified paths and filenames, LSASS dumps.
Furthermore, firms can test if their Exchange Server has been compromised by utilizing Check My OWA. It’s a brand new service that compiles lists of compromised servers with Outlook Web Access (OWA) turned on. The information consists of affected IP addresses and domains and can reveal if actors within the preliminary assaults had been in a position to load a shell on the machine.
Check My OWA can be utilized by merely loading it from the Exchange server and a warning pops up if it is discovered within the service’s record; or you’ll be able to kind in a enterprise electronic mail deal with and a message will attain your inbox informing in case your area is a match within the database.
IoC checking scripts:
Microsoft > github.com/microsoft/CSS-Exchange/tree/main/Security
PwnDefend > github.Com/PwnDefend/Exchange-RCE-Detect-Hafnium
CERT Latvia > github.Com/cert-lv/exchange_webshell_detection
sgnls > github.com/sgnls/exchange-0days-202103
Soteria > github.com/soteria-security/HAFNIUM-IOC
Daniel Card of PwnDefend > github.com/mr-r3b00t/ExchangeMarch2021IOCHunt
Daniel Card of PwnDefend > github.com/PwnDefend/badExchangePews (community-based record of unhealthy IPs)
Yara rule for DearCry / DoejoCrypt
IoCs for DearCry:
- feb3e6d30ba573ba23f3bd1291ca173b7879706d1fe039c34d53a4fdcdf33ede
- e044d9f2d0f1260c3f4a543a1e67f33fcac265be114a1b135fd575b860d2b8c6
- 10bce0ff6597f347c3cca8363b7c81a8bff52d2ff81245cd1e66a6e11aeb25da
- 2b9838da7edb0decd32b086e47a31e8f5733b5981ad8247a2f9508e232589bff




:max_bytes(150000):strip_icc()/HowtoSpecifyaPreferredSMTPServerforaMacOSXMailAccount2016-01-04-568a7f403df78ccc153b7b78.png)
