Cyberattackers are actually utilizing the notoriety of the Colonial Pipeline ransomware attack to leverage further phishing attacks, in accordance with the findings of a cybersecurity firm.
It is widespread for attackers to use widely-covered news occasions to get individuals to click on on malicious emails and hyperlinks, and cybersecurity agency INKY stated it just lately acquired a number of helpdesk emails about curious emails their clients have been receiving.
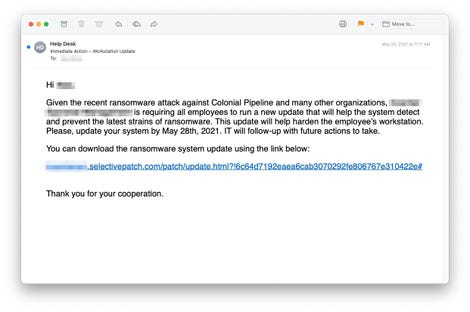
INKY clients reported receiving emails that debate the ransomware attack on Colonial Pipeline and ask them to obtain “ransomware system updates” with a view to shield their group from an identical destiny.
The malicious hyperlinks take customers to web sites with convincing names — ms-sysupdate.com and selectivepatch.com — each of that are newly created and registered with NameCheap. The similar area that despatched the emails additionally managed the hyperlinks, INKY defined in a weblog publish.
INKY
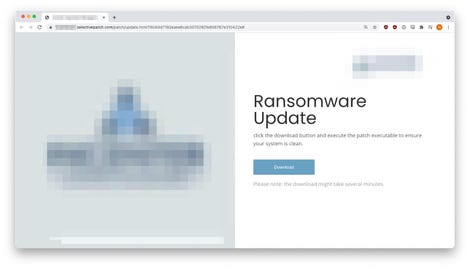
The individuals behind the attack have been in a position to make the pretend web sites look much more convincing by designing them with the emblem and pictures from the goal firm. A obtain button on the web page downloads a “Cobalt Strike” file onto the consumer’s laptop known as “Ransomware_Update.exe.”
In March, Red Canary’s 2021 Threat Detection Report listed “Cobalt Strike” because the second most often detected menace and the INKY report notes that Talos Intelligence discovered it was concerned in 66% of all ransomware assaults in This fall of 2020.
Bukar Alibe, knowledge analyst for INKY, stated they started to see the phishing attack just some weeks after news broke that the pipeline paid millions to the REvil ransomware group with a view to restore the corporate’s methods.
“In this setting, phishers tried to take advantage of individuals’s nervousness, providing them a software program replace that will ‘repair’ the issue by way of a extremely focused e-mail that used design language that might plausibly be the recipient’s firm’s personal,” Alibe wrote. “All the recipient needed to do was click on the massive blue button, and the malware can be injected.”
In addition to capitalizing on the concern round ransomware, the attackers made the emails and faux web site appear like it got here from the consumer’s personal firm, giving them an air of legitimacy, Alibe added.
The attackers have been additionally in a position to get previous many phishing methods through the use of new domains.
INKY
“If it seems to be as if it was despatched by the corporate itself (e.g., from HR, IT or Finance), does it in reality originate from an e-mail server beneath the corporate’s management? If it seems to be just like the HR or IT Departments however deviates from the norm, that ought to be a flag,” the weblog publish stated.
Alibe urged IT groups to inform staff that they’ll “not be requested to obtain sure file sorts” as a result of these sorts of phishing emails search to take advantage of staff want to do the correct factor by following purported safety pointers. Alibe famous that the attack was focused towards two corporations and stated IT groups ought to count on extra assaults alongside the identical strains.
“We wouldn’t be shocked if we see attackers use the latest Nobelium-USAID phishing marketing campaign as a lure,” Alibe stated.





:max_bytes(150000):strip_icc()/HowtoSpecifyaPreferredSMTPServerforaMacOSXMailAccount2016-01-04-568a7f403df78ccc153b7b78.png)