In precept, cell safety has all the similar objectives as desktop safety, however the implementation and preventative measures that IT should put in place are sometimes fairly totally different.
Organizations want to lock down all gadgets that entry enterprise knowledge, and put measures in place to make sure that their knowledge will not fall into the fallacious palms. This common objective applies to all sorts of enterprise safety — community, PC, laptop computer, utility — however mobile security provides distinctive challenges for organizations to grapple with.
For instance, device loss and theft are way more of a priority for cell gadgets than different sorts of endpoints. Mobile gadgets may also function with out conventional Wi-Fi or Ethernet connections and in any location that has a good wi-fi sign.
Organizations ought to flip to mobile-specific instruments, merchandise and insurance policies that may allow staff to be productive on their cell gadgets whereas making certain the safety of the system and its knowledge.
What position do cell gadgets have in enterprise?
The trendy workforce is extra cell than ever due to quite a few components, together with the proliferation of laptops, hybrid devices, tablets, smartphones and different cell gadgets. These gadgets enable staff to be productive from a wide range of areas, equivalent to at dwelling, at an airport or in transit.
Working remotely and whereas on the go is a well-established idea in the enterprise and in organizations of all sizes. Mobile gadgets equivalent to smartphones and tablets have a serious half to play in enabling staff to do that. For instance, many staff carry round smartphones with entry to work e-mail and enterprise purposes in every single place they go.
But, cell gadgets can allow extra than simply on-the-go work. Tablets and smartphones can be utilized for level of sale (POS), record-keeping, knowledge logging and customized kind submissions. Mobile gadgets may even function full workstations with the correct auxiliary system help.
When it comes to securing cell gadgets, private gadgets have way more safety issues and problems in contrast to single-use kiosk approaches. The assault surfaces for kiosk gadgets are far smaller than these of workers’ private smartphones due to the wider array of purposes and freedom to browse the Internet. As such, cell safety insurance policies ought to focus predominantly, however not solely, on securing all these gadgets.
Another frequent sort of cell system in the enterprise is a corporate-owned cell system. Some organizations have the capital to buy cell gadgets for sure workers. Securing these gadgets is comparatively easy — particularly in contrast to personally owned gadgets accessing company knowledge — and IT admins can apply strict safety controls to these gadgets.
What are the advantages of cell gadgets in the office?
The most evident good thing about cell gadgets is the flexibility they supply for workers to be productive from varied areas. Laptops had been the first step in the evolution towards enabling mobility with enterprise endpoints, and cell gadgets equivalent to smartphones had been the subsequent step. In common, cell gadgets improve connectivity, communications, collaboration and networking due to their portability and entry to mobile networks. The accessibility of a corporation’s assets improves dramatically with cell gadgets in the combine.
Users can entry enterprise e-mail, unified communications (UC) cell apps equivalent to Microsoft Teams and Slack, customized enterprise purposes and different apps or providers that allow productiveness. This advantages data staff and executives particularly, as they could want to reply to crucial emails or approve sure workflows whereas on the go or from distant areas.
End-user smartphones aren’t the solely main use case for cell gadgets inside a corporation. Kiosk devices that serve a single purpose are a key a part of quite a few sorts of organizations. Tablets, smartphones and different cell gadgets can help with POS wants, buyer or shopper registration, digital waiver signage, knowledge enter and far more.
Why do companies want a cell safety coverage?
It could also be straightforward to overlook cell gadgets in a safety coverage; in spite of everything, they’re hardly ever a consumer’s most important workstation. This is very the case when it comes to customers connecting their private gadgets to work purposes and providers, equivalent to a corporation’s e-mail server or UC platform.
However, organizations that enable for any entry to work knowledge on cell gadgets completely should have some form of cell safety coverage. It could also be useful to consider it as the “weakest hyperlink in the chain” precept: Company knowledge is just as safe as the least safe system accessing it.
Neglecting cell system and knowledge safety leaves placing vulnerabilities in an organization’s overall security architecture and policy. Therefore, a safety structure that features mobile-specific insurance policies equivalent to acceptable use pointers for cell system customers, mobile security best practices, and safety platforms or providers is crucial for organizations that depend on cell gadgets.
Choosing a cell system coverage: Corporate owned vs. BYOD
One of the first steps in establishing a cell coverage is figuring out whether or not customers’ gadgets can be company owned or consumer owned. Each method has its strengths and weaknesses that organizations have to issue in. Generally, corporate-owned gadgets present extra certainty and ease from a administration and safety coverage perspective, however BYOD permits for extra consumer alternative and adaptability.
Considering corporate-owned cell gadgets
Issuing corporate-owned cell gadgets to customers is the extra easy and costly choice for organizations. The greatest advantages of a corporate-owned method are IT’s safety and administration capabilities. Organizations can keep as restrictive of a tool coverage as they need with out having to fear about invading customers’ privateness on their private gadgets. Users are extra seemingly to be understanding when it comes to a tool that they did not buy themselves. The strategy of deploying app and OS updates can be simpler with full system management as a result of customers sometimes desire to replace their private gadgets on their very own schedule.
An organization-owned system program is not good for each state of affairs. For instance, organizations that assign cell gadgets to customers have to pay for these gadgets. Organizations can negotiate offers with smartphone producers — however even with reductions, the value of all that {hardware} can add up shortly. Larger organizations might not have this difficulty when it comes to assets for cell system purchases, however small or tight-budgeting organizations might not need to incur this value.
Additionally, organizations should resolve if corporate-issued gadgets are allowed to function customers’ private gadgets as nicely. Users might admire the lenience of getting a corporate-owned, personally enabled (COPE) system for the flexibility. However, loads of customers have their very own smartphone or different cell gadgets earlier than becoming a member of a corporation, so this is probably not mandatory. The corporate-owned, business-only (COBO) method permits organizations a really excessive stage of management over the system, its safety and privateness insurance policies, its replace schedule and far more.
Looking into BYOD
Many organizations might see BYOD as the simplest and most straightforward device deployment option. The group does not have to buy new cell gadgets for every new rent, and customers can have a single system for each work and private issues. Carrying round a number of cell gadgets may lead to a poor consumer expertise and worker frustration. The BYOD method is simple, however it could actually immediate extra sophisticated safety insurance policies and administration in contrast with COPE and COBO.
For instance, customers have to agree to the group’s phrases of system use and cell coverage earlier than they begin utilizing their private gadgets for enterprise duties. This might embrace compelled OS or app updates for safety, on-device administration brokers and an general lower in the customers’ privateness. There can be the difficulty of value sharing. Some customers — particularly those that work with their cell gadgets fairly a bit — incur further prices equivalent to knowledge use, system repairs and even system alternative. If organizations can form a coverage to account for these BYOD factors, then BYOD might be a great choice.
Comparing BYOD vs. corporate-owned safety
In very common phrases, corporate-owned gadgets present stronger safety for organizations. This is due to the IT administrator’s potential to management gadgets extra intently in contrast to BYOD deployments. A BYOD safety coverage wants to account for customers accepting the stage of system management that a corporation asks for. As such, organizations are extra seemingly to supply extra lenient safety insurance policies to guarantee consumer acceptance.
Corporate-owned gadgets haven’t got this stage of ambiguity when it comes to consumer acceptance. For instance, IT admins can deploy a coverage that permits for distant system wipes with out worrying about deleting a consumer’s private system knowledge.
IT directors ought to observe {that a} cell coverage’s stage of safety is set primarily based on the controls IT implements and never the system possession mannequin. But the path to a powerful cell safety coverage is less complicated for corporate-owned gadgets.
What are the dangers and challenges of cell system safety?
The advantages of cell gadgets are widespread and may match inside an enormous quantity of use instances. However, cell gadgets convey extra assault surfaces and different challenges that IT and finish customers want to tackle.
While there’s a notion that cell gadgets aren’t prone to threats, that is categorically not the case. Like any endpoint, hackers can intercept ingoing and outgoing visitors from the system, trick customers into downloading malware and entry customers’ knowledge through a compromised community connection.
Further, mobile devices face additional threats that typical endpoints don’t. Device loss and theft are extra frequent with cell gadgets, and social engineering assaults are extraordinarily frequent with the quite a few vectors that cell gadgets enable. Phishing attacks that target certain employees’ mobile devices can use SMS messaging, e-mail accounts, messages through quite a few social media purposes and even malicious hyperlinks in browsers.
There additionally could also be challenges with integrating cell gadgets into current back-end programs, legacy and customized purposes, and providers which are tailor-made to endpoints equivalent to PCs and laptops. It’s nice to present customers with entry to e-mail and fundamental company providers, however the value of deploying and managing these cell gadgets is probably not price it for sure organizations if they cannot entry all firm programs. Most enterprise know-how distributors are conscious of the position of cell gadgets and supply services that accommodate cell gadgets, however cell help is not common. This is very true with customized and legacy purposes.
These compatibility issues can morph into bigger problems with compliance as nicely. Highly regulated fields, equivalent to authorities, finance and healthcare, might have problem enabling mobility whereas abiding by every sector’s regulatory legal guidelines.
Steps to outline and implement a cell safety coverage
Organizations can mitigate the safety dangers and shortcomings of cell gadgets with a particular and efficient cell system coverage. This is very true with the cell safety parts of that coverage.
Mobile insurance policies ought to be detailed, complete and largely personalized primarily based on a corporation’s wants. While it may be useful to start a mobility policy from a template, organizations have to outline sure parts, together with acceptable system use, system possession coverage, privateness coverage and disclosure of what knowledge the group can view. The coverage also needs to clarify what on-device safety and administration brokers can be current, and what measures a corporation can take to ensure data security — e.g., can a corporation run a distant system wipe whether it is compromised or remotely lock the system whether it is in danger.
Once IT workers and administration collaborate to construct the cell safety coverage, there may be nonetheless work to do. Organizations should discover the finest means to define this coverage and talk it to finish customers; a coverage is just efficient if customers perceive and cling to it. Ideally, customers ought to evaluate the documentation throughout the onboarding course of.

Organizations ought to observe who wants to evaluate the cell coverage and confirm that every consumer accessing enterprise knowledge with a cell system has learn the mandatory paperwork and accomplished any security awareness training.
Additional cell safety finest practices and measures to think about
Mobile gadgets are extra prone to theft than laptops and PCs, so making certain that cell gadgets have strong authentication necessities is crucial. Organizations can require stronger cell authentication methods, equivalent to an eight-character minimal for system passwords as an alternative of numeral-only PINs, and even two-factor authentication. The two-factor method might complement a passcode with further measures, equivalent to biometric components — normally a fingerprint or iris scan — a consumer location verification or a secondary authentication system equivalent to an ID card or chip.

Direct system theft is much from the solely means hackers goal cell gadgets. Cybercriminals typically goal cell gadgets over public Wi-Fi networks. Because these networks do not require any authentication, hackers can prey on unsecured gadgets which are related to that community. Further, some hackers arrange their very own public Wi-Fi networks that imitate free Internet from companies equivalent to espresso outlets or eating places. Organizations ought to limit entry to unsecured public Wi-Fi through a administration console if attainable and, at minimal, clarify these risks in the cell safety coaching and documentation.
These finest practices could make up a powerful cell safety coverage, however IT directors additionally want to take into consideration how they’ll implement these controls. The most ubiquitous method to cell coverage enforcement is cell system administration (MDM) platforms. Vendors typically bundle these management platforms into bigger choices, equivalent to enterprise mobility administration (EMM) and unified endpoint administration (UEM). The bigger choices embrace broader administration capabilities; for instance, EMM contains cell utility administration (MAM) capabilities alongside MDM controls. UEM takes all that EMM provides and expands it to all sorts of endpoints, together with laptops and PCs.
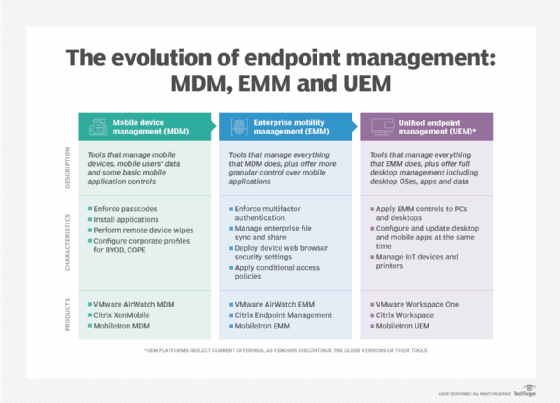
Most EMM and UEM platforms include both MDM and MAM capabilities. Organizations can also need to think about cell menace protection (MTD) platforms, which supply extra superior safety administration capabilities than MDM or MAM. For instance, some MTD platforms supply phishing and spam filters, system well being studies, malware scans and habits evaluation.
IT directors should discover an MDM platform and different supporting applied sciences that may meet their system safety and administration wants. It’s inconceivable to stroll via all the potential integrations, options, licensing fashions and help that totally different organizations may wish, so IT directors ought to work with executives and carry out diligent market analysis earlier than deciding on the excellent product. This might embrace working with product demos, speaking immediately to distributors, and consulting with impartial researchers that consider cell safety and administration choices.





