| Specs at a look: Helm Personal Server | |
|---|---|
| CPU | Quad-core 1.6GHz ARM Cortex-A72 w/TrustZone crypto module |
| RAM | 2GB ECC |
| Storage | 128GB NVMe SSD w/256-bit AES-XTS encryption |
| Connectivity | 802.11ac/a/b/g/n, Bluetooth 4.2, Gigabit Ethernet, 2x USB-C 3.0 |
| Dimensions | 111.1mm x 180.9mm x 130.1mm (4.375″ x 7.125″ x 5.125″) |
| Price | $499.99 at the Helm store (plus $99/12 months subscription, waived for first 12 months) |
As Ars security-meister Dan Goodin famous in his preliminary write-up back in October, the Helm Personal Server is a small-ish ARM-based email server that sits in your house and does for you what Gmail or Outlook.com or whomever your present email supplier does for you. It’s a full-featured, single-domain (for now) MTA in a field that you need to use with a vast variety of email addresses and accounts, and it offers you 128GB of house to make use of as a mail retailer for these accounts. It additionally offers you CalDAV calendaring, notes, and CardDAV contacts, and it does all of it with open-source purposes which might be chosen and configured in a approach that demonstrates a strong bias towards particular person safety and privateness.
And I prefer it. I prefer it lots. I didn’t suppose I’d, however after spending every week with the system, I’m nearly able to spring for one—nearly. And that’s excessive reward, coming from a paranoid email self-hoster like me.
Based on my brief time with the Personal Server, the reward is correctly earned. The Helm workforce primarily based its product principally across the similar mail stack that I personally want and use—the holy trinity of Postfix for SMTP, Dovecot for IMAP, and SpamAssassin for holding issues clear. The system correctly makes use of SPF, DKIM, and DMARC—and handles all of the DNS stuff essential to make these issues work. End-user information is well encrypted at relaxation and in flight. Clever use of tunneling to AWS-based gateways transparently works round widespread ISP blocks on email service ports. And, maybe most significantly, you don’t must know what any of that stuff means to make use of the system securely—informal people who perhaps simply wish to reduce their reliance on Google or Microsoft will discover the transition to Helm comparatively painless, and there aren’t some ways to screw it up and make your self much less safe.
But technical customers may balk at a few of its shortcomings and annoyances—the underlying Postfix/Dovecot configuration (together with the constellation of smaller apps like OpenDKIM which might be essential to make it work) can’t be considered, modified, or edited. If you’re bringing an present area to the Helm service, you presently have to switch your area’s authoritative DNS to Helm’s AWS-based DNS servers in order that the service can handle the required MX and TXT information. The alternative of AWS for DNS means Helm presently doesn’t provide DNSSEC help. And a couple of different minor points may make skilled email sysadmins hesitant—although conversations with Helm’s help workforce throughout the evaluation have me satisfied of the corporate’s willingness to evolve the product in a path extra suitable with the (typically troublesome) calls for of energy customers like me.
All that being stated, the tl;dr right here is that I like Helm. I like what the corporate is doing, and I like the best way it’s doing it. With a couple of minor modifications (and a few extra uncovered knobs and levers so I can tweak issues a bit), I’d fortunately purchase a tool and transition my email internet hosting off of my present setup.
Now let’s dig somewhat deeper into what we’ve obtained right here.
How Helm suits into the email-hosting dilemma
In early 2014, I penned a four-part series about learn how to host your personal email in your personal area, primarily based by myself adventures in self-hosting. Although the guides are at this level in dire want of updating, they’re among the many hottest issues I’ve written in my whole tenure at Ars (eclipsed solely by the time I talked non-stop about farts for a whole week). Doing my very own email internet hosting has on the entire been a rewarding and difficult endeavor that’s yielded large quantities of information, expertise, and grey hair—and, after doing it for a bit greater than 5 years, I’ve no plans to cease.
There are important advantages to self-hosting your email, however they arrive with important downsides, too—most notably, you’re on the hook for any errors or issues. “Email,” said Past Lee, “is sort of a pet, and when you step up and personal your personal pet, you’ve obtained to handle it, clear up after it, and ensure evil individuals do not infect it with horrible viruses and remodel it right into a zombie.” Looking after an email server does sometimes require work—a accountable sysadmin must sustain with updates, keep watch over the log recordsdata, verify often on RBLs, be aware of deliverability and sender repute, and different miscellaneous sysadmin-y duties. It’s not overly onerous, but it surely’s not hands-off, both.
Helm goals to provide the better of each worlds—the reassurance of getting a tool stuffed with delicate data bodily underneath your management, however with nearly the entire heavy sysadmin lifting accomplished for you.
The main issue Helm will face right here is the advertising and marketing message—who is that this factor for? Most people within the offended graybeard set (of which I rely myself a member) are both already self-hosting or have dismissed self-hosting as way more bother than it’s price; the casual-user set doesn’t actually suppose a lot about how email works or what “internet hosting” actually means.
Helm subsequently has determined in its advertising and marketing literature to lean closely on the privateness points of self-hosting. Helm’s website leads with that message and performs up how switching to Helm is a technique to take possession of 1’s on-line identification and divorce oneself from technological dependence on big data-hungry companies:
Your most important information (like emails, search historical past, passwords, images, and movies) is saved on a large company server outdoors your property.
Increasingly, this leaves you susceptible to hacks, firms profiting out of your information and on-line habits, and mass authorities surveillance.
It’s a advertising and marketing message not with out some mandatory caveats—so long as you’re exchanging emails with different individuals who use these huge company companies, you’re simply as susceptible to mass surveillance and information harvesting as earlier than, since marketeers (together with any three-letter company) will merely vacuum up your message on the receiving finish reasonably than the sending finish. And Helm’s utilization of AWS for a lot of its infrastructure—even with a accountable eye towards encryption and holding delicate information correctly siloed—means you’re nonetheless relying closely on one of many most data-hungry companies of all of them.
The message, nevertheless, isn’t wholly inaccurate—you’re higher off self-hosting. It stays an open query, although, of whether or not the typical shopper (and even the typical tech-savvy Ars reader) could be prepared to spend $499 and a further $99 every year for a nebulous and difficult-to-fully-quantify enhance in safety. Convincing individuals to take action will probably be Helm’s biggest problem—most likely an excellent deal tougher than truly designing the service within the first place.
The Helm service—or, “the place does my $99 a 12 months go?”
I wish to discuss only for a second about exactly what that ongoing $99/12 months cost pays for. Obviously, Helm has workers, and they should make payroll; the Helm service requires ongoing work behind the scenes for it to stay long-term practical. But the subscription charge additionally covers a good quantity of actual AWS-based infrastructure prices that include every Helm system offered.
Helm makes use of Amazon’s Route 53 DNS service on the back-end, which supplies you a strong DNS setup with numerous quick, geographically distributed resolvers. To work round ISP restrictions on ports and to eliminate the Sisyphean job of making an attempt to make use of a residential ISP IP addresses for email service, the corporate spins up Amazon EC2-based gateway machines that set up tunnels to the residential Helm gadgets. “All the gateway does is ahead packets backwards and forwards,” defined Helm CEO and co-founder Giri Sreenivas to Ars. “All TLS terminates on this system. All we’ve accomplished is introduce an additional hop on the Internet. We’re funneling encrypted visitors.”
Helm additionally places some care into the AWS IP addresses assigned to the Helm gateway, doing all the required legwork to vet these addresses towards the ever-changing listing of anti-spam IP address blacklists utilized by most email servers.
The AWS prices for Helm additionally embrace built-in cloud redundancy; the corporate makes use of Amazon’s US-West-2 area for its gateways and retains machines in all three of the area’s availability zones. The firm makes use of a separate area, US-East-1, for all of its information storage—that’s, the place the place your gigabytes of encrypted email back-ups reside.
The mail circulate
Those EC2-based gateways are one of many keys to creating Helm work. When your native Helm server powers on, it establishes an IKEv2-based tunnel to an EC2 gateway. That EC2 occasion is assigned the general public IP tackle referenced in your area’s MX information, and makes use of good ol’ iptables to ahead choose packets via the tunnel to your Helm server.
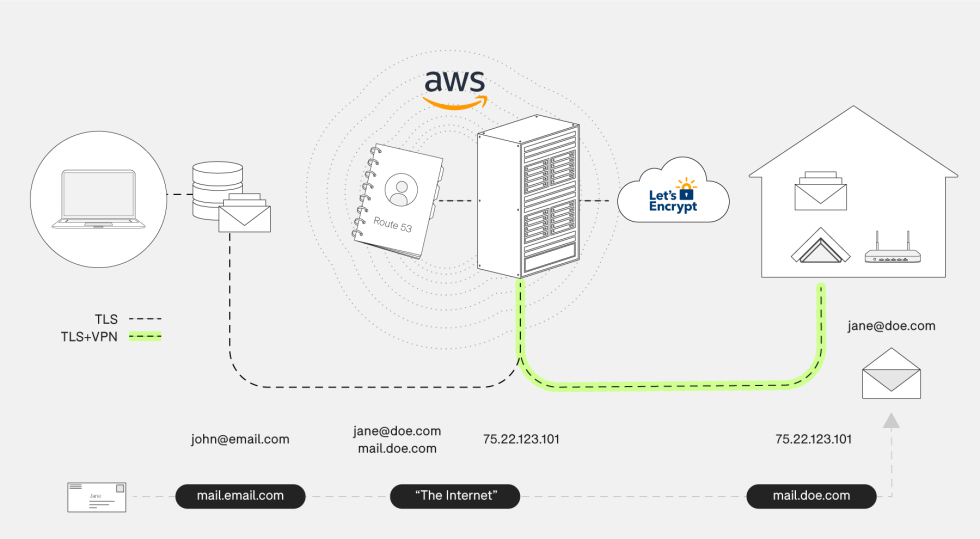
The path is identical whether or not you’re an IMAP consumer checking your inbox or one other email server transmitting a message over SMTP—all the things goes through the gateway.
Interestingly, because of this email purchasers on the identical LAN because the Helm server nonetheless run their visitors throughout the Internet, via the tunnel by means of AWS. When you configure your consumer, you level it at “helm.yourdomain.com” for SMTP and IMAP and ahead DNS lookups on that hostname will at all times return the AWS gateway’s Internet IP tackle.
I requested Helm help about bypassing the tunnel and addressing the Helm server’s mail ports immediately on the LAN, which is likely to be one thing a buyer with split-horizon DNS would do. The response was reassuring: “This should not be an issue,” the help individuals stated. “If the person units up DNS to level on to the native Helm IP tackle for native purchasers, these ports are presently open, and so it ought to work. This isn’t a configuration that we’ve examined, nevertheless, however technically we don’t see any concern with this.”
(While the SMTP and IMAP ports are domestically addressable, there’s not a lot else you may truly do to the Helm server immediately—there isn’t any technique to log into it. Configuration duties are all accomplished through an app, which we’ll get to shortly.)
The choice to wrap all server comms in a tunnel pleasantly sidesteps the 2 main points that usually include making an attempt to self-host an email server on a residential ISP connection. Namely, you don’t have to fret about your ISP blocking inbound connections on widespread email ports, and also you don’t have to fret about the truth that most residential IP addresses are everlasting residents on nearly each blacklist ever. By shifting the connection level to Amazon’s cloud and being picky with the IP tackle pool they must work with, Helm saves you no scarcity of complications. (You additionally don’t have to fret about updating a DNS entry when/if your property IP tackle modifications, however that’s principally a solved downside at this level anyway.)
Unboxing and setup
The server comes packaged with a quickstart information, a community cable, a good-quality branded AC adapter, a USB key for storing your backup encryption key(s), and a Helm sticker (our evaluation system additionally got here with a separate USB stick loaded with press belongings and pictures).
Setup is fairly darn simple. You unbox the server, peel off the plastic protecting movie round it and its AC adapter, plug it in, and join it to your LAN. The system has built-in 802.11ac and may be run wi-fi, however you want to set issues up wired first earlier than you may configure Wi-Fi. Update: Helm notified me after the evaluation went reside that the preliminary setup can certainly be accomplished wirelessly if desired.
After you’ve got plugged within the community cable, you flip the factor on, set up the cellular app in your iOS or Android system, and comply with the steps.
-
Here it’s: your Helm Personal Server. Well, the field, no less than.
Lee Hutchinson -
The high of the field comes off, revealing a sharp package deal.
Lee Hutchinson -
The field backside incorporates the remainder of the package deal: a community cable, a sticker, a quickstart information, an AC adapter, and an important USB stick in your encryption keys. The inexperienced PNY stick is only for reviewers and incorporates a presskit with images (a few of that are scattered via this evaluation).
Lee Hutchinson -
The Helm Personal Server, going through the digicam.
Lee Hutchinson -
The Helm Personal Server, going through away from the digicam. Visible are two USB-C ports (one reserved for energy, because the AC adapter terminates in a USB-C plug), energy button/standing mild, and gigabit Ethernet.
Lee Hutchinson -
The peak of Helm’s roof incorporates a small cut-out housing one other USB-C port—this one for attaching a stacking growth unit (when/if one is finally launched).
Lee Hutchinson -
One of the system’s eaves homes a detachable (however glued in place) 2.5″ SATA bay.
Lee Hutchinson -
Apologies for the standard of this photograph—it was annoyingly troublesome to take. This is a peek into the two.5″ SATA bay.
Lee Hutchinson
Those steps, pictured in a gallery under, will see you first pairing your Helm server along with your smartphone through Bluetooth to kick off the setup. The Helm server and your smartphone carry out a token alternate through Bluetooth that permits your cellphone to proceed getting used for admin duties; configuring new smartphones to work with the Helm app requires bodily proximity and one other Bluetooth connection. (Configuring smartphones to ship and obtain email with Helm, although, doesn’t—you solely want to fret concerning the one-time Bluetooth connection for gadgets you’re going to make use of to manage the server.)
It’s essential to pause and reiterate that, after the preliminary token alternate through Bluetooth, all communications between your administration smartphone and the Helm server occurs over the Internet through the AWS gateway. That’s the case even when your cellphone and the Helm server are on the identical LAN phase. This is definitely a aid for folk like me who’re maybe greater than somewhat paranoid about placing a tool we will’t handle or improve on a trusted LAN phase with different trusted gadgets—since there’s no direct communication between your administration system and the Helm server, there’s no motive you may’t completely plop the Helm server in your IoT VLAN if in case you have one and even onto its personal remoted phase.
Per a observe from Helm help, the one factor the field wants to have the ability to do is ship outbound visitors on UDP ports 500 and 4500 and on TCP port 443. You don’t want any incoming port-forward guidelines.
The evaluation models Helm despatched out had been preconfigured with check domains (I obtained “helmdomain21.com”), however for those who’re an precise buyer, you’ll both have bought a website from Helm once you purchased the system otherwise you’ll have switched your present area’s authoritative DNS over to Helm’s DNS servers once you purchased the system.
Regardless of how you bought there, the setup continues by displaying you the area assigned to you and asking you to enter an activation code Helm sends you at buy. After that, you create your first mailbox for the area, which can also be your administrator account.
The setup assistant then prompts you to insert that flashy silver USB stick into one of many Helm’s ports. At this level, the server generates an encryption key pair and writes the non-public key to the stick. The encryption keys are used each for encrypting the Helm’s native filesystem and in addition for encrypting the server’s automated backups, that are mechanically uploaded to AWS for you. If your Helm server dies or is stolen, you’ll want this bodily key to revive your email backups and configuration to a alternative Helm system.
-
After unboxing your Helm and powering it on, you put in the app and are greeted with this.
-
You should pair your smartphone with the Helm server over Bluetooth to alternate a token. You should do that with any smartphone or pill you wish to use to admin your Helm server. (You do NOT want to do that for those who simply wish to ship and obtain Helm email on a tool—solely if you wish to set up the Helm app and do admin stuff.)
-
Next you enter an activation code and confirm that the area preconfigured on the server matches your email area. (For reviewers, Helm despatched out gadgets preconfigured with generic domains for testing functions. I obtained “helmdomain21.com”.)
-
Then you create an admin account, which can also be an email inbox.
-
Give it a password and permit notifications (which you’ll be able to disable as desired later).
-
Then the setup course of asks you to insert the silver USB stick that got here with the server. Your Helm server’s encryption secret’s written to the stick. Store it in a safe place: you will want it for those who ever have to revive a backup.
-
Next—no less than on iOS—the Helm server will ship you some preconfigured profile recordsdata in order that you do not have to manually add your Helm inbox to your cellphone.
-
Tapping “set up” kicks off the profile set up course of.
-
One profile, three accounts.
-
And there they’re.
-
Tapping on the email account reveals pre-populated account particulars.
-
Calendar account particulars.
-
Contacts account particulars.
-
Once the profile is put in, you are prepared to begin utilizing the server.
-
The app’s admin interface presents you with an inventory of extra duties you may wish to do.
-
The email account reveals up in your listing of email accounts within the default iOS email consumer.
-
Account particulars from the iOS settings display.
-
Calendar account particulars.
-
Contacts account particulars.
Finally—no less than on iOS, which is what I exploit—the appliance generates a set of profiles containing your Helm account’s email, calendar, and contacts settings. Then the appliance installs all of that for you, although you need to hit OK a couple of instances to shepherd the method alongside. This is a pleasant comfort that eliminates you probably needing to copy-and-paste (or, worse, write down and manually enter) a bunch of server and account settings.
Once the profiles are put in, you’re instantly capable of ship and obtain email out of your new area. After that, the app has a set of wizard-like duties in the principle window to indicate you learn how to import email from exterior accounts, create extra email addresses, and set per-device passwords in your Helm account so it may be accessed on different gadgets like a laptop computer or pill.






