3rd Party Risk Management
,
Account Takeover Fraud
,
Business Email Compromise (BEC)
Fraudsters Have Been Using SMTP Multipass Flaw for Business Email Compromise Schemes
Attackers have been actively exploiting a flaw in Rackspace’s hosted email service to send phishing emails, bearing legitimate and validated domain names, as part of business email compromise scams.
See Also: Can You Rely on Microsoft 365 for Email Security?
So warns 7 Elements, an IT safety testing consultancy based mostly in Edinburgh, Scotland, which says that attackers have been utilizing what it is dubbed as an “SMTP Multipass” assault – SMTP refers to easy mail switch protocol – because it’s designed to subvert a number of accounts and bypass DNS-based defenses towards spoofed emails. All organizations that use Rackspace’s hosted e-mail companies seem to have been weak to having their e-mail domains get misused on this method.
7 Elements says one among its shoppers was focused utilizing the assault, as a part of a BEC scheme – aka CEO fraud effort – in July, after which it reported the issue on to Rackspace.
Texas-based Rackspace is the world’s largest managed cloud supplier, and offers entry to such cloud choices as Amazon Web Services, Microsoft Azure and OpenStack.
The firm has advised at the very least some clients, together with Information Security Media Group – a buyer of Rackspace’s hosted e-mail service – that it goals to have a repair in place by the top of November.
But Rackspace didn’t instantly reply to a number of, extra questions in regards to the flaw, together with beneficial mitigation steps pending a full repair, and for what size of time the flaw might have been getting exploited, or to what extent.
Required: Authenticated Access to Any Rackspace Account
Exploiting the flaw requires an attacker to have authenticated entry to a Rackspace buyer’s occasion, 7 Elements says in a weblog submit. With such entry, an attacker can exploit the flaw to ship emails as one other Rackspace buyer. Such emails “can be obtained by the recipient, move e-mail safety checks and be recognized as a authentic sender,” the agency says. “Malicious actors may make the most of this performance to conduct focused phishing assaults or to masquerade because the chosen goal area, doubtlessly inflicting reputational injury.”
Organizations weak to having their e-mail domains get misused on this method embrace not simply ISMG, but in addition quite a few different Rackspace clients, together with a number of U.S. federal companies, U.Ok. native authorities entities, navy companies and politicians, in addition to high-profile people.
A pattern of weak e-mail domains shared by 7 Elements embrace:
- breitbart.com
- cadbury.co.uk
- gitlab.org
- hackerwarehouse.com
- honda.mx
- nationalguard.com
- marines.com
- richmondindiana.gov
- schneier.com
- schwarzenegger.com
- scorpioncomputerservices.com
- 666casino.com
With ISMG’s permission, 7 Elements was ready to make use of the flaw to ship an e-mail to ISMG that spoofed a Rackspace buyer area, handed all safety checks, and which gave the impression to be real.
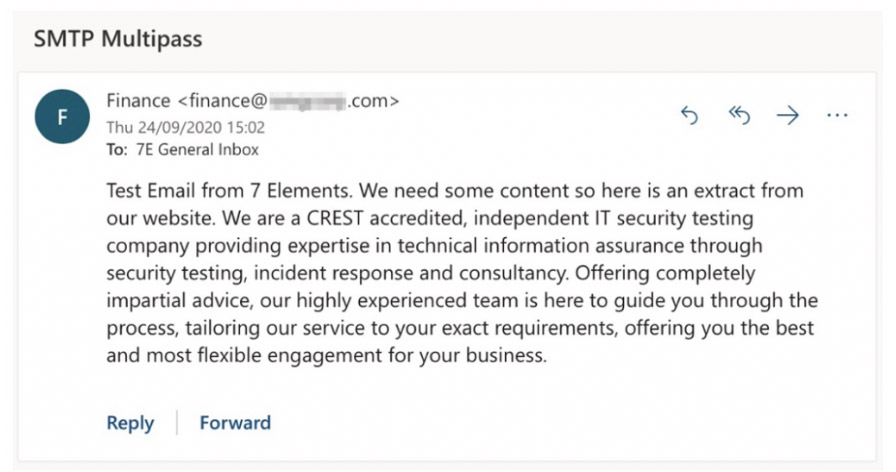
Using technical particulars shared confidentially by 7 Elements, ISMG CTO Dan Grosu was capable of affirm the findings, creating an unbiased proof of idea that leveraged a number of domains hosted by Rackspace for ISMG.
Rackspace has advised ISMG, which raised the problem – as a buyer – that its repair, hopefully arriving by the top of November, will replace e-mail internet hosting logic to limit an authenticated consumer to solely being allowed to ship e-mail from a site tied to their Rackspace area.
Separately, Rackspace has advised 7 Elements that it started alerting clients in regards to the flaw on Oct. 29, that it expects to start rolling out fixes on Thursday, and conclude by the top of November.
Coordinated Disclosure
As famous, 7 Elements says one among its shoppers obtained a phishing e-mail – tied to a BEC scheme – on July 20. After investigating, the agency stated it was capable of establish and reproduce the SMTP Multipass flaw about 10 days later.
“Our investigation confirmed that this vulnerability was being actively exploited by at the very least one malicious actor to spoof emails,” says John Moss, a senior safety marketing consultant at 7 Elements. “There are clearly some critical inquiries to be answered by Rackspace, if it was conscious of this vulnerability, and its exploitation resulted in reputational or monetary loss for a enterprise.”
In early August, after concluding the incident response engagement, 7 Elements stated it started what turned out to be “productive communication with Rackspace round verifying the problem, the timeline for fixing the problem and moral issues of disclosure.”
“Our investigation confirmed that this vulnerability was being actively exploited by at the very least one malicious actor to spoof emails”
— John Moss, 7 Elements
Both organizations agreed a coordinated vulnerability disclosure date of Nov. 5, or greater than 90 days after the flaw was reported. In mid-September, in the meantime, 7 Elements says Rackspace knowledgeable it that another person had subsequently found and reported the flaw to it.
Technical Details
Specifically, the flaw subverts sender coverage framework, or SPF, which is used to confirm that an e-mail has originated from a real sender, utilizing a site’s DNS data to make sure that the IP tackle from which the e-mail has been despatched is doing so on behalf of the real area, in accordance with a full technical teardown of the flaw launched by 7 Elements on Thursday.
“The flaw was the results of how the SMTP servers for Rackspace – emailsrvr.com – approved customers, mixed with clients particularly authorizing these SMTP servers to ship e-mail on their behalf by way of DNS entries,” as denoted by SPF data, “particularly if their SPF report was set to move emails from emailsrvr.com – as recommended by Rackspace,” 7 Elements says.
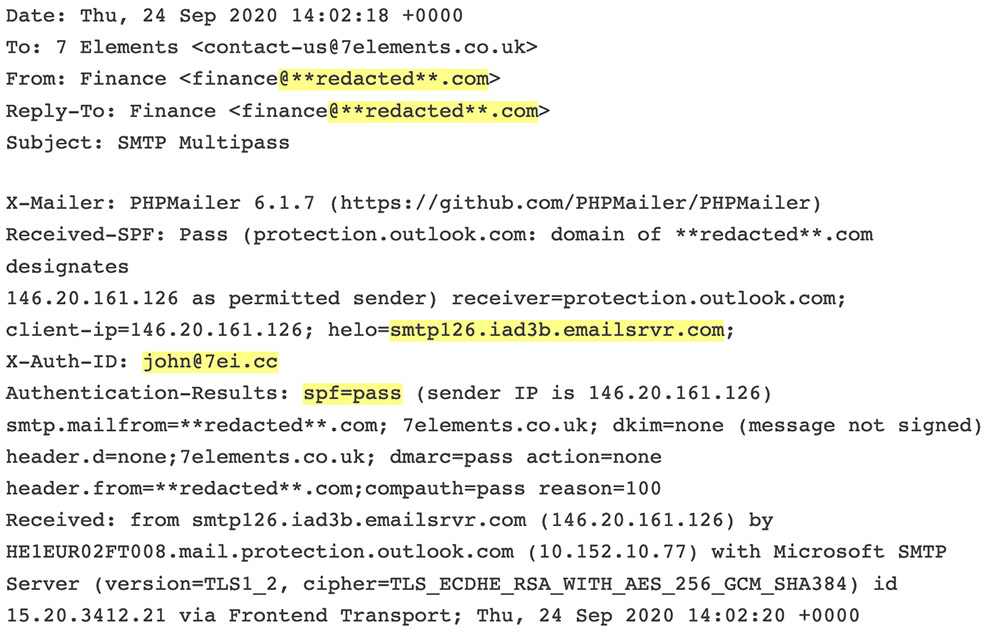
One method to establish emails which were despatched utilizing the flaw is to interrogate header data, the safety agency says, “searching for an X-Auth-ID worth that doesn’t match the ‘from’ tackle,” in addition to “emailsrvr.com” being the sending e-mail server. “The malicious actors now we have discovered to be utilizing this in the actual world additionally made use of PHPmailer to ship the e-mail, though this may not be required to take advantage of the vulnerability,” it provides.
PHPmailer is a code library designed to ship emails from an online server. From an attacker’s perspective, they may run the code on any server, together with one to which they’d gained illicit entry.
“For our check, we used a trial account inside Rackspace and set our area to 7ei.cc,” 7 Elements says. “A malicious actor may have achieved the identical or as with the real-life instances now we have investigated use compromised accounts.”
How Long Has Flaw Existed?
With attackers actively exploiting the flaw, it is unclear how lengthy Rackspace has identified about the issue. “Cloud-hosted e-mail affords a cheap and versatile method to handle your company e-mail necessities. However, the cloud is not any totally different to the broader challenges of managing a company’s knowledge securely,” says 7 Elements CEO David Stubley.
“In this case it might seem that Rackspace had determined to make a threat determination on behalf of its clients, slightly than informing them of the problem in order that organizations may make an informed determination” about what diploma of threat they is likely to be prepared to simply accept from their e-mail internet hosting supplier, he says.





