Hackers hijacked an Oxford e-mail server to ship malicious emails as a part of a phishing marketing campaign designed to reap Microsoft Office 365 credentials from European, Asian, and Middle Eastern targets.
The attackers additionally made use of area hosted on an Adobe server and used by Samsung throughout 2018’s Cyber Monday occasion.
By leveraging the respected manufacturers of Oxford University, Adobe, and Samsung inside the identical marketing campaign, the risk actors’ assaults had every little thing wanted to bypass their victims’ safety e-mail filters and trick the victims themselves into handing over their Office 365 credentials.
“Using official Oxford SMTP servers allowed the attackers to go the fame verify for the sender area,” Check Point researchers who found the marketing campaign explain.
“In addition, there was no must compromise precise e-mail accounts to ship phishing emails as a result of they may generate as many e-mail addresses as they needed.”
Phishing disguised as Office 365 voice mails
The marketing campaign was noticed by Check Point researchers in early April 2020 after observing a collection of suspicious emails pretending to be notifications of missed Office 365 voice mails.
To implement the phantasm of a official e-mail, the phishing messages additionally had been adorned with a “Message from Trusted server” notification above the content material.
These emails had been claiming that an incoming voice message was ready within the targets’ voice-portal, asking them to click on on a button that might have taken them to web page on their Office 365 account the place they may pay attention or obtain the missed message.
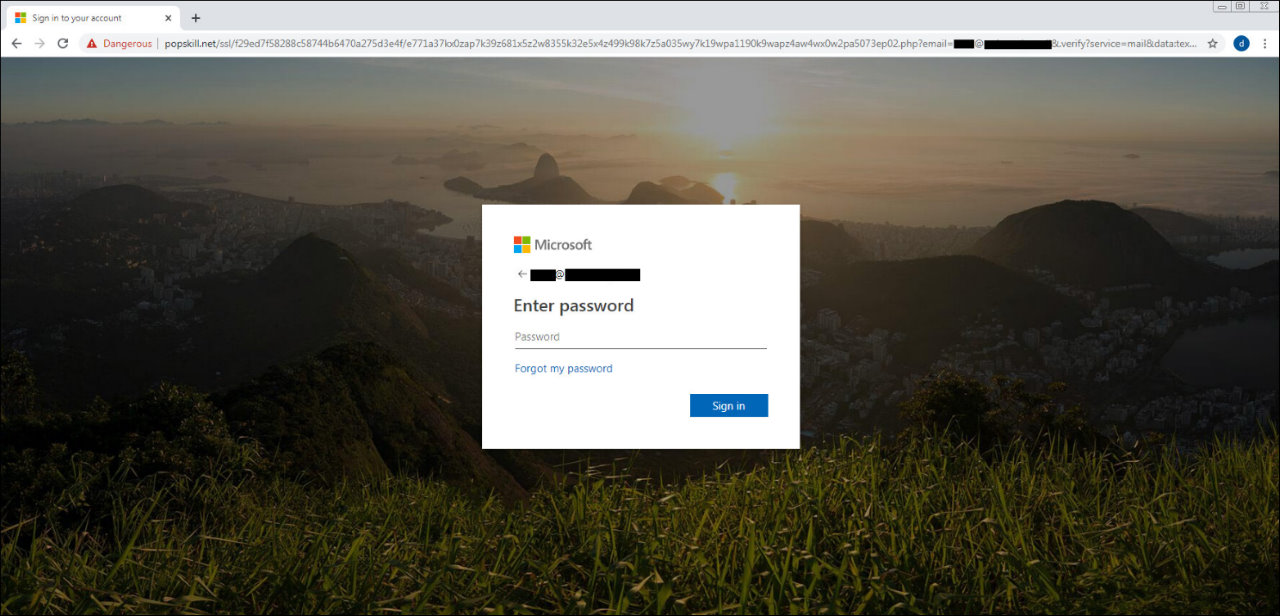
After the potential victims clicked the Listen/Download button embedded within the phishing message, they had been as a substitute redirected to a phishing touchdown web page disguised as an Office 365 login web page.
.png)
Redirects used to filter victims
“Behind the scenes, this redirection consists of two levels: the primary stage abused an current redirection scheme on the official area (e.g. samsung[.]ca), and the second stage redirected the person to a compromised WordPress web site,” Check Point explains.
The phishing kits used as a part of the second stage of the assault had been hosted on a number of compromised WordPress web sites, with the redirect code checking if the guests arriving on the hacked websites got here by way of a phishing e-mail, stopping the assault in its tracks in the event that they weren’t and sending the guests to the precise web site as a substitute of the phishing web page.
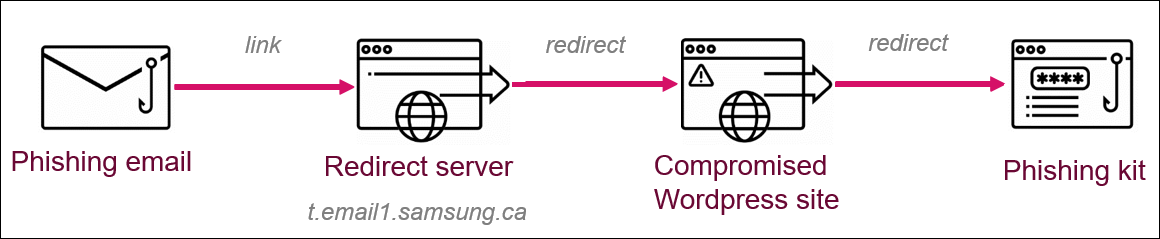
Throughout this marketing campaign, the malicious actors additionally repeatedly modified and improved redirection strategies and URL parameters within the phishing hyperlinks to evade detection by pattern-based engines by making them unbiased of a particular area and the Adobe Campaign servers.
Additionally, “[m]ost of the emails got here from a number of generated addresses belonging to official subdomains from totally different departments within the University of Oxford (UK).”
The closing web page internet hosting the phishing package and used to gather and exfiltrate Office 365 credentials to attacker-controlled servers was fully-obfuscated and it created separate digital directories for every sufferer so that every of them had distinctive URLs assigned.
“Adobe took the related actions to stop any such assault by means of its server throughout all prospects,” Check Point stated.
Last month, one other highly convincing Office 365 phishing campaign used cloned imagery from automated Microsoft Teams alerts making an attempt to steal credentials from roughly 50,000 customers.
Earlier in June, enterprise homeowners with Microsoft Office 365 accounts had been focused by a phishing marketing campaign utilizing bait emails camouflaged as legitimate Small Business Grants Fund (SGF) relief payment messages from the UK authorities.
More particulars on the Office 365 phishing marketing campaign utilizing a hijacked Oxford e-mail server and indicators of compromise (IOCs) together with redirect websites’ URLs and a listing of compromised WordPress websites internet hosting Office 365 phishing pages and intermediate redirects can be found in Check Point’s report.

:max_bytes(150000):strip_icc()/registration-3938434_1280-e2aa7e5d57264ae19b69027f14c85c2f.jpg)




