The Dynamic Malware Analysis System by BitNinja
The COVID-19 outbreak has accelerated the expansion of Internet visitors. The variety of web sites is rising quickly, and there are extra eCommerce companies than ever. Therefore, the shared hosting firms are doing a roaring commerce. But sadly, these will not be the one numbers which are rising. Cyberattacks are additionally on the rise, and no enterprise is protected these days. By now, cybercrime is among the most continuously reported financial crimes in the organizations, making cybersecurity a C-suite and board-stage concern.
Today we are going to speak about detect and take away obfuscated malware from shared hosting servers.
What is Obfuscated Malware?
The obfuscation method is for hiding the actual objective of a program. The hacker creates a code that isn’t readable by people, however the performance behind it stays the identical. So, while you run this system, it should behave just like the encapsulated program it was designed for.
How to research several types of malware
There are two several types of evaluation once we speak about malware: static and dynamic.
Static Analysis
The static evaluation contains hash algorithms, string matching, code-based mostly detection, and there’s a new, patent-pending method invented by George Egri (Co-founder and CEO of BitNinja), the source code structure analysis.
| Signature kind | Example |
| MD5/SHA2/SHA3 | 5d41402abc4b2a76b9719d911017c592 |
| String match | eval(base64_decode( |
| Code-based | if the primary line begins with a whole lot of house and … |
| SA-MD5 | Full structural match |
| SA-SNIPPET | Partial structural match |
This creates a particular construction-based mostly signature from the supply code after which does the matching on the construction. This means, irrespective of how the supply is altered, the construction would be the identical. It is similar to how plagiarism checker methods work.
Dynamic Analysis
But bounce again to the forms of analyses. Besides the static evaluation, there may be the dynamic evaluation. When utilizing the dynamic evaluation, you run the supply code partially or totally and observe this system’s habits.
Deobfuscation
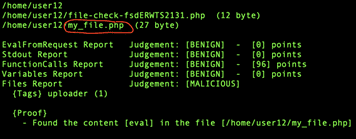
You can see the eval obfuscation in the screenshot right here.
One of the habits evaluation strategies is deobfuscation. If you discover the obfuscation mechanism, you may deobfuscate the code. After that, you may decapsulate the actual program and match the deobfuscated supply code. But consider me, there are too many various obfuscation methods. So, it’s not that straightforward to deobfuscate the code, and there are different facets which are arduous to research with out partially operating the code.
Output
Another method is from the output while you analyze the output of this system. Most of the time, while you run malware, you may discover traces of malicious habits from the output.
Function Calls

Within the confines of the “Function Calls” evaluation, you run the code, and you discover which capabilities are used for malicious actions.
Variable Content

The subsequent one is variable content material evaluation. This program incorporates one thing “phishy”, as you may see in the image. It’s at all times suspicious when a supply code contains perform names like explode and primary instructions used to decode attention-grabbing variable names.
File Manipulation
It can occur with actual information or inside a simulated setting to securely analyze file manipulations.
Multi-Path Execution

Finally, you are able to do multi-path execution while you analyze what would occur when you compelled the interpreter right into a code department. This means, you could find locked code components, and this system can also be fairly useful in discovering malicious behaviors.
How to make use of these methods
The old skool means
Sandboxing is a technique to make use of these methods you probably have a few particular servers for that objective.

These servers can spin up digital servers, and also you add the PHP file to it, run the code and do the above-talked about analyzing strategies. The drawback of this system is that it takes round 20 seconds to research one PHP file. Analyzing all your PHP information would take a whole lot of time and eat up too many sources.
The new means
BitNinja has constructed a PHP simulator. It’s a protected setting the place you may partially run PHP information on the server and run all of the analyses that we have been speaking about. With this function, you may analyze previous PHP information on the servers and may uncover the latest zero-day malware, even when they’re obfuscated.
How to safe shared hosting servers?

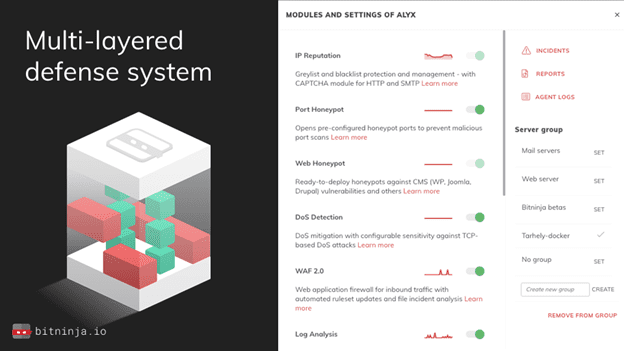
You want totally different options in opposition to DoS assaults, brute pressure, botnets, vulnerability scans, backdoors, and the record is nearly by no means-ending. The finest method to safe your servers is to arrange a multi-layered protection system that stops the assaults on every layer.
That’s precisely what BitNinja gives. You can set up it with a one-line code, after which you will have a fancy system of layers from actual-time IP popularity by way of honeypots, DoS detection, WAF, log evaluation, and naturally, malware detection.
About BitNinja in a nutshell
George Egri is a cybersecurity and internet-internet hosting professional. He is the co-founder and CEO of BitNinja and the proprietor of the second-largest shared-internet hosting firm in Hungary, the Web-Server Ltd. Some years in the past, they’d a whole lot of buyer complaints due to hacked web sites. They tried to mix the totally different instruments available on the market to safe their servers in opposition to the totally different sorts of cyberattacks, however after some time, it grew to become unmanageable. So, they determined to resolve this downside by creating an inside all-in-one answer. This mission was the ancestor of BitNinja. They realized that it might be helpful not only for them but additionally for the shared internet hosting business and the entire Internet. Therefore, they began to determine their sources in BitNinja and make the Internet a safer place.
About Author: Akos Molnar Content Marketing Manager, BitNinja Technologies